Discussing risks associated with cybersecurity is no small task, but it’s perhaps one of the most important conversations any business can undertake.
In December 2018, HDR moved 1,000 of its employees from three buildings in Omaha, Nebraska, to fully occupy a new 10-story facility that the firm leased. During the building’s construction, we became aware of potential operational technology cyberphysical risks and sought an immediate and permanent solution.
Knowing that contract changes may be required, we provided a simple presentation to key members of the team, including the building’s owner, general contractor and heating, ventilation and air conditioning controls contractor. Our goal was to identify cyberphysical risks, provide an action plan and request buy-in from all parties.
Each member saw this endeavor as an opportunity and we started the journey with an eight–step process.
1: Recognize cyberphysical risks
Understanding the risk — i.e., what we are protecting ourselves from — is essential to putting together an action plan. We closely followed the plan that our information technology department had in place for its practices. That plan included staff education on cyber concerns, physical security (card access and cameras), cybersecurity measures and a sustainable documentation plan moving forward.
2: Identify all operational technology systems
OT devices are sensors and controllers for the physical environment. As an example, think of building systems that include electrical generator systems, fire alarms, lighting controls, physical security, mechanical chillers, boilers, pumps and building management systems.
As we enjoy the benefits of internet protocol-based OT systems to provide a safer and more efficient environment, we also have increased the cyberattack landscape. What is particularly concerning is that life safety systems could be disabled by cyberattackers, or they could hack through an OT system to gain access to a company’s IT network. Such cyberphysical risks are covered in more detail in the Whole Building Design Guide.
For purposes of this document and as related to the headquarters building, OT includes the same scope as platform IT, facility-related control systems and industrial control systems.
3: Assign priorities in the OT system
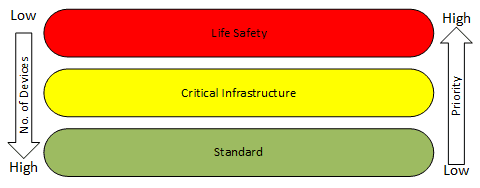
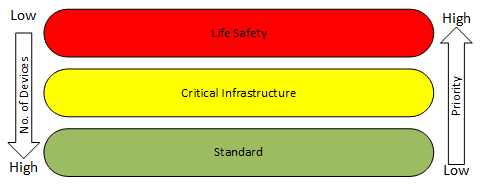
A thoughtful OT cyberstrategy starts with an evaluation of network connections required for safe and efficient building operation. The Guide to Industrial Control Systems Security provides guidance. All OT devices were assigned to one of three priorities: life safety, critical operations or standard (see Figure 1).
4: Consider the OT network layout as it was bid
As a starting point, the HVAC controls contractor provided the network as bid. The network was designed to meet all requirements of the performance specifications in our contract documents. The network’s cyberreadiness was considered next.
5: Conform the OT network to the Purdue Model
The Purdue Model is the Purdue Enterprise Reference Architecture, a model developed in the 1990s to segment elements of networks to increase security and safety.
This is where the heavy lifting began.
Devices were separated from the IT network when possible. Where there is no need to connect to the data network, physically separating, or “air-gapping,” is generally recommended. For example, the fire alarm and elevator systems have no data network requirement and are therefore physically segregated. All outside connections to these systems, such as the audio connection to the fire alarm, were evaluated by our IT group. All controls from the fire alarm control panel (for example, the air handling shutdown) are hard-wired to other systems.
Another example is the elevator controller connectivity, which includes a hard-wire connection to the source automatic transfer switch. Yet another example is the generator system, which includes hard-wired interfaces to the automatic transfer switches and dampers. A project use case study included the generator system to be visually annunciated on the building management system.
Part of HDR’s IT cyberstrategy is to physically segregate from OT networks in the spaces the firm leases, although the headquarters project does have exceptions. Upon review of the use-case matrix, we determined it was required to integrate data between our audiovisual system and the owner’s lighting and shade control systems.
Conference area use-cases included an automated lighting scene and shade position from the AV controller. Whenever data are shared, a connection is required between components. It took a few conference calls between the IT staff and the lighting control and shade control manufacturers to come up with a solution. HDR’s IT team configured the connection, mitigating the cyberrisk of a direct connection to the network. Clearly, IT engagement is key.
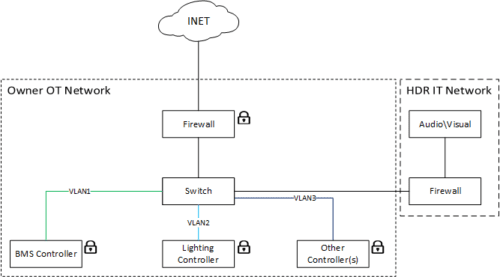
The building management system is at the heart of building controls and includes fan, chiller and boiler control. The network is essential for facility operation, so where a network is required, a thoughtful cyber design should be implemented. The HDR team started with a color-coded OT network design compliant with the Purdue Model found in Cybersecurity of Facility-Related Control Systems. The five–level control system architecture was the basis of all discussion during project construction.
A network firewall was configured by the owner’s IT group and is the first line of defense for network protection. No connectivity to or from the internet is allowed, except through the firewall.
Typical cyber strategies of virtual local area networks and whitelisting are employed. The configuration and documentation of the network was completed by the HVAC controls contractor to conform both cyber protection and building management system network functionality.
Visibility from the internet into the BMS (on the OT network) is completed through a secured virtual private network (see Figure 2).
The HVAC controls contractor alerted the group that to conform to the configuration requirements of Unified Facilities Criteria 4-010-06, a network switch upgrade was required. The approval to upgrade was made before ordering OT switches.
6: Inventory devices
Completing an inventory of OT devices, which referenced firmware, software, communications and hardening guides, established fruitful discussions between contractors and the IT group. IT reviewed the consolidated inventory of devices to confirm the applicable cyberstrategy was employed, based on the capability and robustness of each device. Because Level 0 devices are sensors and cannot be hacked, data were collected on Level 1 through 5 devices, according to the Purdue Model.
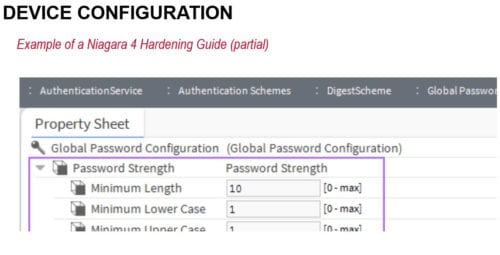
7: Configure components
Some OT components adopt standard IT practices and have all typical authentication, authorization and accounting capabilities. For OT devices, which are less robust than typical IT devices, our IT group provided alternative network configurations. Mitigation of cyberrisk is both an art and a science (see Figure 3).
8: Ensure sustainable network management and documentation
Network setup, configuration of components and documentation are necessary upfront and for the life of the building. The building owner has a process that may be audited by HDR to confirm equipment is being patched and logs are maintained.
HDR’s new headquarters building provided us an opportunity to include thoughtful cybersecurity perspectives to our OT network. Our first step was to build a functional use-case matrix. On our project, a use-case is defined as bridging the gap between what outcomes are desired and how to achieve them in the design documents, through the integration of data between OT systems. The use-case matrix provided the reason to integrate and connect building systems to the network.
In addition to all use-cases being realized and commissioned, working through these eight steps resulted in an IT/OT network that leveraged the OT savvy of the controls contractor within the familiar framework of our IT group.
See additional stories on cybersecurity and facilities including:
Four ways to sharpen the technology that runs buildings in 2020
When remote monitoring and control becomes essential for manufacturing operations
When remote monitoring and control becomes essential for manufacturing operations
Original content can be found at Consulting - Specifying Engineer.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.