Learning Objectives
- It is helpful to look beyond national borders and English language dominated sources.
- Kindly don’t allow external devices to be plugged to your controls without considering the consequences.
- Think again about opportunities for cybersecurity improvements as a process rather than event and see three articles on cybersecurity in this issue.
Those answering the 2020 Control Engineering cybersecurity survey provided advice to peers based on knowledge and experiences. A summary follows. Data was collected Feb. 7 through March 5. Answers are lightly edited for grammar; tips covering multiple categories generally fall in the group matching the first tip. A categorical tally of 48 cybersecurity tips showed:
20 cybersecurity related to processes
17 cybersecurity related to technologies
9 cybersecurity related to people (internal)
2 cybersecurity related to external threats.
Cybersecurity tips related to process
Always be active and vigilant to stay ahead of the threats.
Be prepared for the unthinkable
Being aware of deficiencies in your cyber defenses only brings to light opportunities you have to improve. Don’t be afraid of audits. They should only help provide knowledge, understanding and management support allowing for change for the better to happen.
Closely follow the updates and trends. Be aware of vulnerability and incidents.
Create a physical security plan ahead of the cybersecurity plan.
Do not allow the use of mobile equipment without a strong procedure.
Follow security basic industry best practices.
Have the proper governance and resources in place, for both engineering and operational technology (OT).
Make sure a project incorporates the cybersecurity at the beginning of the project. Needs to be at the forefront of all water/wastewater plant upgrades.
Never click on hyperlinks of unknown or unattended emails. Always use a secure virtual private network (VPN) for wide area network (WAN) navigation. Use a crypted password utility. Never bridge industrial control network with WAN.
No system is perfect, the threats are always evolving, there is never enough staff or budget. Provide an even level of protection across your assets and maintain current offline backups.
Prevent by design, continuous watch, detect and protect.
Since a majority of penetrations come from spear-phishing, it is incredibly important to apply controls and training to prevent this.
Test your networks often for discovery of new devices.
Think about cybersecurity early on in the design process. It is much harder to implement it later.
Training on availability vs security. Is it worth the risk of loss of availability for the security protection. An example is installing the latest security patches too quickly. Another is too strict a policy on password complexity vs refresh rate.
Understand and implement appropriate guidelines.
Understand where IT, IoT, and OT security overlap and work independent within your company and its extended customer and supply chain networks.
Verification of proper implementation by means of testing is more important.
Vigilance.
Cybersecurity tips related to technology
ALWAYS UPDATE
Be knowledgeable of your industry
Be proactive and start implementing new appliance/software to protect your/the customers assets
Be up to date on cyber security technologies news.
Constant surveillance and updating as the threat continually evolves.
Constant update of security patchup
Converged plant wide Ethernet designs are frequently vulnerable. Air gaps are undervalued and easily implemented capital design solutions which can simplify operations and grant protections without in depth knowledge and should be employed where professional cyber protection guidance cannot be afforded.
Do not allow any mobile or external device to have read/write privileges. Some remote observation might be allowed. Do timeout detection and recovery (TDR) for all hardware connections to detect the impedance change caused by any connection. On detection connect to sandbox and attempt to back trace source of intrusion. Sandbox runs simulation program, but has no actual access to control system.
Include cybersecurity tools/layers of defense in all capital projects.
Keep vigilant for unknown threats and update security defenses as often as possible
Never stop improving your systems, and learn from others mistakes.
Physically separate your industrial control system (ICS) network and manage USB ports.
Process control security
Protection method needs to be flexible/adaptable to keep up with latest technology to prevent attacks.
Secure the control system network from the business network. Only allow access to the control system network through VPN for offsite engineers and any system integrators etc.
Secure you equipment now, don’t wait for an attack
Use a random password generator.
Cybersecurity tips related to people (internal)
Always be on the look out.
ALWAYS expect the unexpected.
Be alert
Cybersecurity is real and has to be treated seriously.
Don’t let IT fool senior management into thinking they can secure the process control domain!
I know I should know more. Yet there is much information on cybersecurity without any real substance. Let’s share best practices from real-world experience.
Stay informed
Stay vigilant, my friends.
User education is the biggest threat to security. No matter how advanced or expensive something is, we need users to be educated.
Tips related to external threats
It is helpful to look beyond national borders and English language dominated sources.
Kindly don’t allow external devices to be plugged to your controls without considering the consequences.
Think again about opportunities for cybersecurity improvements as a process rather than event and see three articles on cybersecurity in this issue.
Mark T. Hoske is content manager, Control Engineering, CFE Media, mhoske@cfemedia.com.
ONLINE
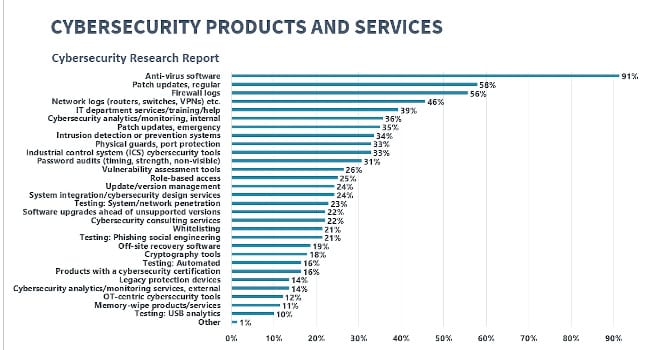
See more tips and bar graph of cybersecurity products and services used with this article online at www.controleng.com/magazine.
See prior article online based on this research: Cybersecurity requires asset updates
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.