
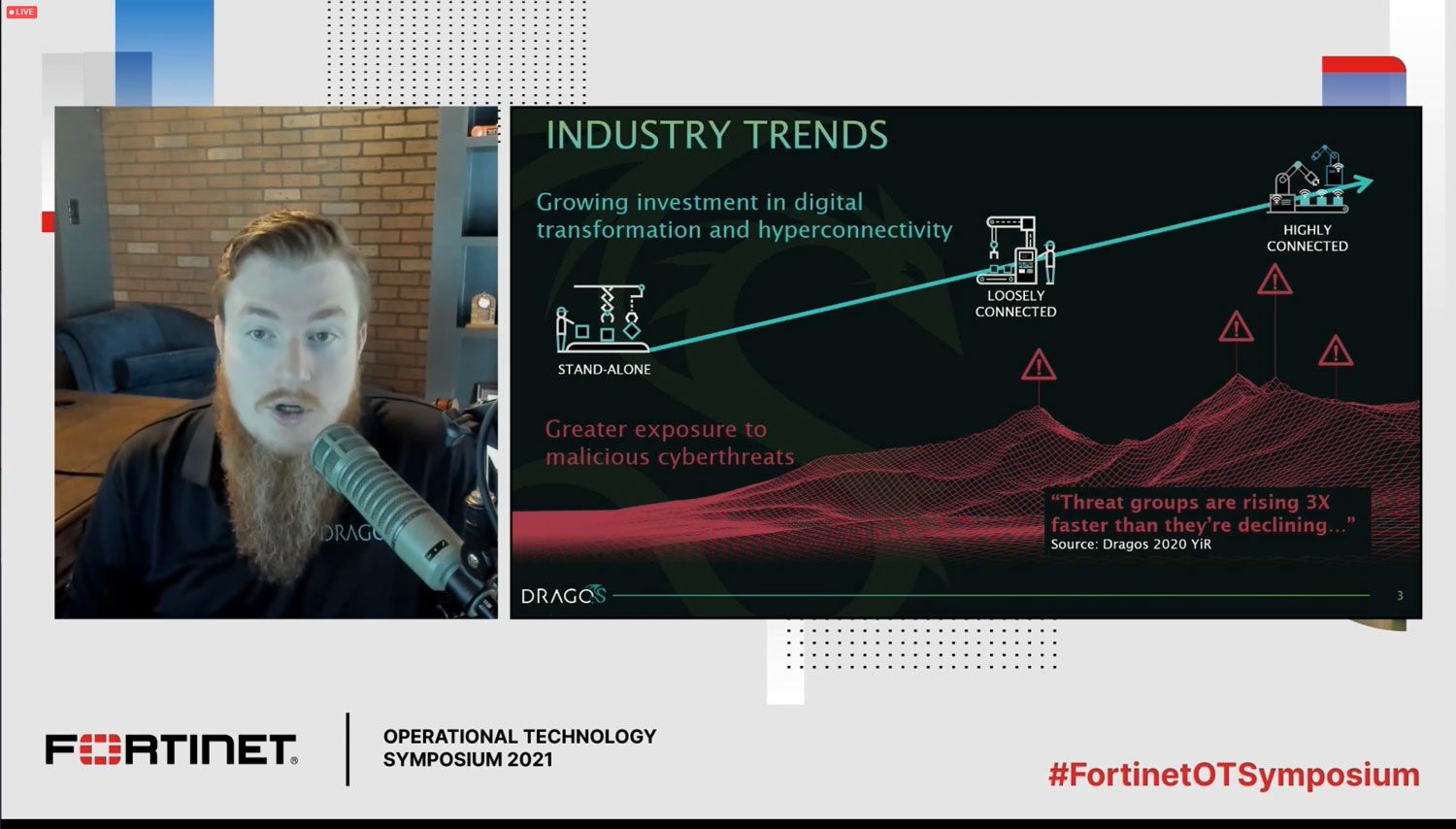
Webcast: Bridging the Cybersecurity Gap, 5 Things IT and OT Can Learn From Each Other
To protect against attacks, companies need IT and OT to work together. This webcast presents 5 things OT can learn from IT (and vice versa)

To protect against attacks, companies need IT and OT to work together. This webcast presents 5 things OT can learn from IT (and vice versa)

Building on its success in preparing professionals for careers in cybersecurity, Indiana University (IU) has been awarded a grant from the National Science Foundation (NSF) for a new project to train the next generation of […]

In late September, the U.S. Department of Energy (DOE), in partnership with the Manufacturing Innovation Institute (CyManII), announced an investment of more than $1 million in five projects to help make advanced manufacturing processes and […]

The Cyber Security for Critical Assets Summit (CS4CA) will bring together hundreds of information technology (IT) and operational technology (OT) security leaders from across U.S. critical infrastructure for two days of strategy planning, insight building […]

In early August, the industry’s largest hybrid event – Black Hat USA 2021 – took place online and at the Mandalay Bay Convention Center in Las Vegas. The event, which highlighted the latest security trends […]
Energy systems historically have been consistent, safe and reliable, but that doesn’t mean they’re not a target of cyber threat. More and more attackers are now explicitly targeting the kinds of industrial control systems (ICSs) […]

Edge computing is one of the fastest growing areas in the industrial sector as organizations pursue Industry 4.0 opportunities to gain insight from assets at the edge. Over the next few years, IDC projects edge […]

Computing at the edge is one of the fastest growing areas in the industrial sector, but it can also create new cybersecurity risks

Without the right approach to cybersecurity, cyber-physical systems involving the Internet of Things, Big Data and cloud computing are nothing more than an expanded attack surface for hackers

In this session, the presenter will outline the current threat landscape, identify some of the most common vulnerabilities and outline some practical first steps to take to secure industrial control systems, as well as how to take a more holistic view of ICS security

To protect against attacks, companies need IT and OT to work together. This webcast presents 5 things OT can learn from IT (and vice versa)

Building on its success in preparing professionals for careers in cybersecurity, Indiana University (IU) has been awarded a grant from the National Science Foundation (NSF) for a new project to train the next generation of […]

In late September, the U.S. Department of Energy (DOE), in partnership with the Manufacturing Innovation Institute (CyManII), announced an investment of more than $1 million in five projects to help make advanced manufacturing processes and […]

The Cyber Security for Critical Assets Summit (CS4CA) will bring together hundreds of information technology (IT) and operational technology (OT) security leaders from across U.S. critical infrastructure for two days of strategy planning, insight building […]

In early August, the industry’s largest hybrid event – Black Hat USA 2021 – took place online and at the Mandalay Bay Convention Center in Las Vegas. The event, which highlighted the latest security trends […]

Energy systems historically have been consistent, safe and reliable, but that doesn’t mean they’re not a target of cyber threat. More and more attackers are now explicitly targeting the kinds of industrial control systems (ICSs) […]

Edge computing is one of the fastest growing areas in the industrial sector as organizations pursue Industry 4.0 opportunities to gain insight from assets at the edge. Over the next few years, IDC projects edge […]

Computing at the edge is one of the fastest growing areas in the industrial sector, but it can also create new cybersecurity risks

Without the right approach to cybersecurity, cyber-physical systems involving the Internet of Things, Big Data and cloud computing are nothing more than an expanded attack surface for hackers

In this session, the presenter will outline the current threat landscape, identify some of the most common vulnerabilities and outline some practical first steps to take to secure industrial control systems, as well as how to take a more holistic view of ICS security
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.