Energy systems historically have been consistent, safe and reliable, but that doesn’t mean they’re not a target of cyber threat. More and more attackers are now explicitly targeting the kinds of industrial control systems (ICSs) the electric sector relies on. Bringing the energy market into the future to meet changing needs was the focus of Day 2 of Fortinet’s Operational Technology Symposium, Energy Day, an online event held on Aug. 31, 2021. The goal of Energy Day was to provide advice and best practices on how to secure the future of industrial controls.
Opening Keynote: OT Cyber Threats and Recommendations for the Electric Sector
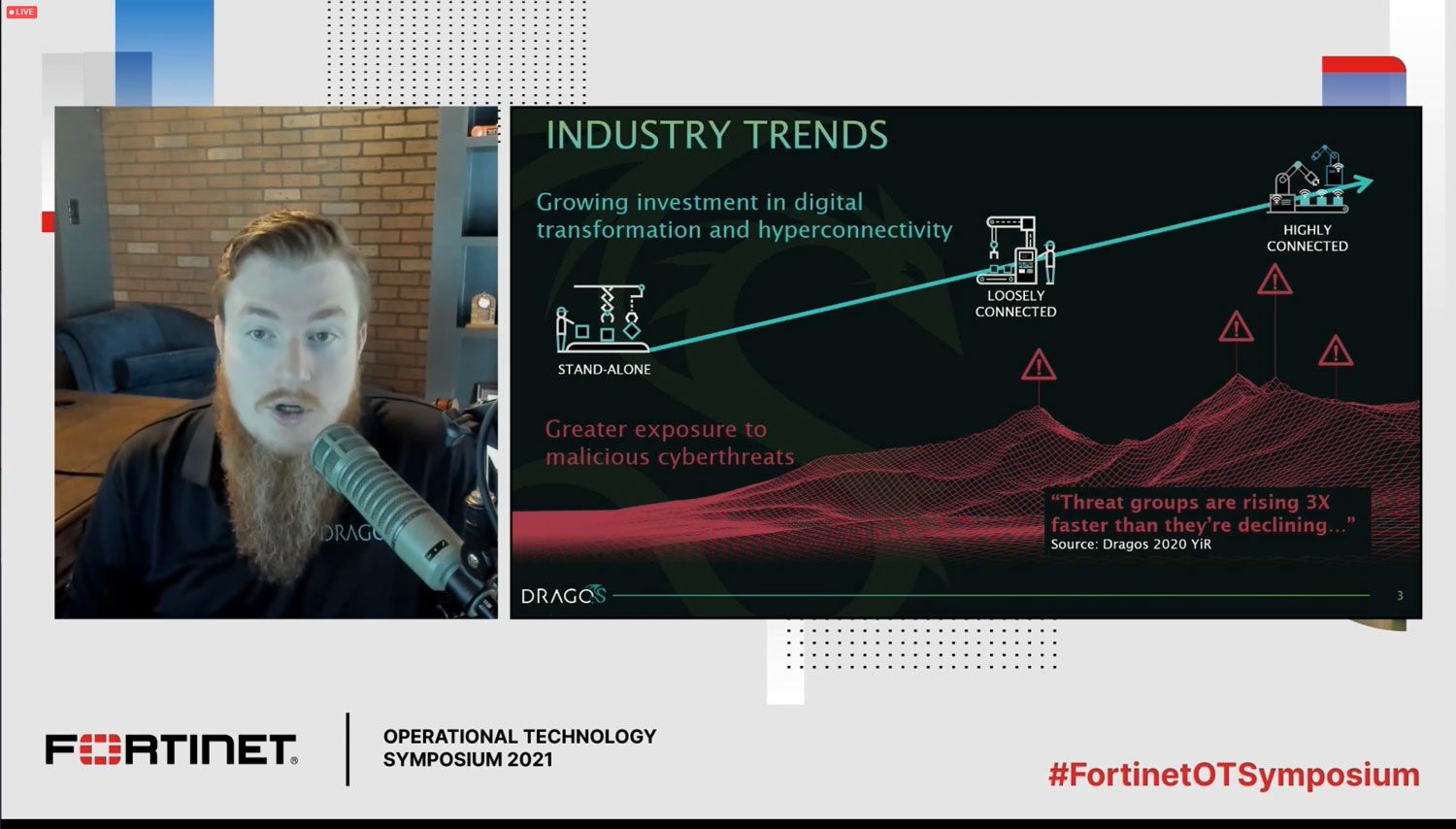
Robert M. Lee, CEO of Dragos, kicked off the event with his opening keynote on cyber threat in the electric sector. While energy systems have been resilient, they face many of the same challenges as other ICS environments. The growing investment in digital transformation and hyperconnectivity has benefitted the industry overall — creating safer, more reliable and more affordable systems — but it has also opened it up to greater exposure to cyber threats. Dragos has found that threat groups are rising three times faster than they’re declining.
Lee said people are explicitly targeting industrial OT systems, making it a much more complex environment. The threats are always getting worse, but we don’t need to “freak out” about every vulnerability out there. As the industry matures, people are looking deeper into cybersecurity, so they are naturally finding more, but that doesn’t mean people should be hyping up the problem. Not all threats are created equally.
“Threats are worse than you realize, but not as bad as you imagine,” Lee said.
We need to understand where that “hurricane path” of increasing threat is heading so we can stay ahead of the adversaries. Dragos has examined ICS critical vulnerabilities in the electric sector and found that while some vulnerabilities are useful, others are “trash.”
“If a vulnerability doesn’t introduce new risk, why bother your operations team with it?” Lee asked.
In the electric sector, Dragos found that:
- 27% of critical vulnerabilities and exposures (CVEs) contained errors
- 46% of advisories had incorrect data
- 56% had a patch but no alternative mitigation
- 21% had no patch and no alternative mitigation
- 26% had no patch
The goal should be to work with original equipment manufacturers (OEMs) to understand which vulnerabilities matter and need to be attended to. Potentially affected OEM devices include cellular gateways, routers, wireless bridges and access points.
Lee said Dragos has been tracking known threat groups and found 11 groups specifically targeting electric (there are 15 that are around every industry). The electric sector tends to be more mature, so it’s further along with visibility and does more monitoring than other sectors. The question is: What are the tactics, techniques and procedures (TTPs), or repeatable patterns and behaviors, we can get insight from.
There are specific ICS things we have to worry about, one of which is breaches with OEMs. OEMs have remote access to critical parts of customer networks, so hackers that breach an OEM could use their credentials to control critical customer processes. Compromising an OEM, as in the SolarWinds incident, magnifies the potential risks to infrastructure. According to Lee, we need to get better at having mature discussions around compromises and how we deal with incidents. Transparency is a big part of this.
Lee then discussed the Biden administration’s recent 100-day electric plan. As part of this, owners and operators need to modernize cyber defenses, as well as improve visibility, detection and response. As of Aug. 16, there were at least 150 electric utilities, serving almost 90 million electric customers, that had adopted or committed to adopting new technologies.
Lee cited this 100-day plan as an example of a true public-private partnership. As in, “We have a problem; you guys go solve it.” It’s always important to let the experts figure out what the action should be. Lee said the real heroes of the discussion were the electric utilities, who answered the call and understood the problem. Now, other industries, such as oil and gas, chemical and water, need 100-day action plans as well.
Digital and Security Trends in the Energy/Power/Utilities Sector
Next on the docket was Ricky Watts of the Intel Internet of Things group talking about digital and security trends in the energy/power/utilities sector. He said the energy sector has a rigid architecture that was designed well over 100 years ago and is mostly the same now. While it is centralized and rigid, it is also very reliable. As we think about transforming the industry to meet new demands and standards, we must learn from what we’ve done in the past.
According to Watts, the world is changing, and reducing carbon emissions is becoming more important. At the same time, renewables are becoming much more efficient. So how do we bring these new sources into the old grid?
Solar and wind are a little more unstable and less reliable than coal because the sun and wind are variable in terms of supply. This creates instability, so we need to flatten the power grid.
Thanks to things like electric vehicles, power storage, data centers and microgrids, there has been a massive increase in demand that cannot be met with carbon-based fuels. This increasing demand will need to be answered with renewables — and their instability. The industry can’t bring this in with the infrastructure it has today so it’s essential to transform grid distribution.
To read more about Watts’ vision for the future of the electric grid, check out our comprehensive article on his talk.
A Case Study: Securing Energy/Power/Utilities Digital Infrastructure using Fortinet
Following Watts was Radhika Chaturvedi of GE Renewable Energy speaking about security in the electric sector. Chaturvedi looked at OT security and defending against cyber threat from the business side.
OT systems are under attack, and control systems are often the target. She cited a Wired article from June 2017 where researchers found they could hack an entire wind farm, access the control systems and manipulate the turbines. Since then, there has been more proof of the susceptibility of OT systems, with the attacks on Oldsmar and Colonial Pipeline. Control systems are the heart of OT environments, so how do we address these risks?
Chaturvedi said governments are definitely paying attention. In North America, there have been things like the NERC-CIP standards, and the Biden administration’s executive order and executive memos focused on cybersecurity for critical infrastructure. Globally, the European Union (EU) NIS Directive is the first legislation to bolster cybersecurity in the EU. This, Chaturvedi said, is a really good step in driving home the importance of industrial control systems and how security needs to evolve.
So what does this mean for OEMs? Future services have to align with these regulations and requirements, and build that into the products and procedures as they provide services. This will require a greater focus on supply chain security and critical infrastructure.
One of the real positives is that customers’ requirements are starting to converge around IEC 62443, and there is enough overlap between NERC CIP and IEC 62443 to enable a North Star for compliance.
But some customers have developed their own unique requirements, which can make things more complicated. Ideally, we want more convergence around a single set of requirements.
Another issue with these new standards is that in a cost-sensitive industry, IEC is adding costs to product security and engineering. Chaturvedi said 64% to 84% of the capital cost in an average onshore wind system is the wind turbines. Less than 4% of the capital cost is the supervisory control and data acquisition (SCADA) and ICS systems, with very little focus on cybersecurity.
While customers are taking it seriously and asking better questions, the gap between security teams and procurement teams still exists.
To add cost in a cost-sensitive industry, Chaturvedi suggested introducing the costs into the entire value chain. Some ways the industry can evolve to address market needs are:
- Organize by objectives of secure product development, implementation and operational compliance
- Create a playbook/policy to drive security into the product development process with reviews/approvals
- Embed a team of security engineers within engineering to assist product line readers
- Translate security requirements into engineering speak and distill them by applicable requirements
- Define the reference architecture to better security across the fleet and the business
- Create value-based product options and services to meet customer compliance and budget needs
Security adds cost in the value chain that needs to be expected. Budgets must reflect this, and companies need to reset expectations. They need to use process, people and technology to streamline costs, and this implementation can be made easier with the right technology.
Defense-in-Depth Security for Energy/Power/Utilities
Chris Blauvelt of Fortinet was up next to talk about battling cyber threat with defense in depth. Now that OT systems are increasingly connected, defense in depth can strengthen the resiliency of networks. The threat landscape of power, utilities and renewables continues to expand as the value chain transforms with increased digital transformation. In the modern era, moving data reliably and securely is key.
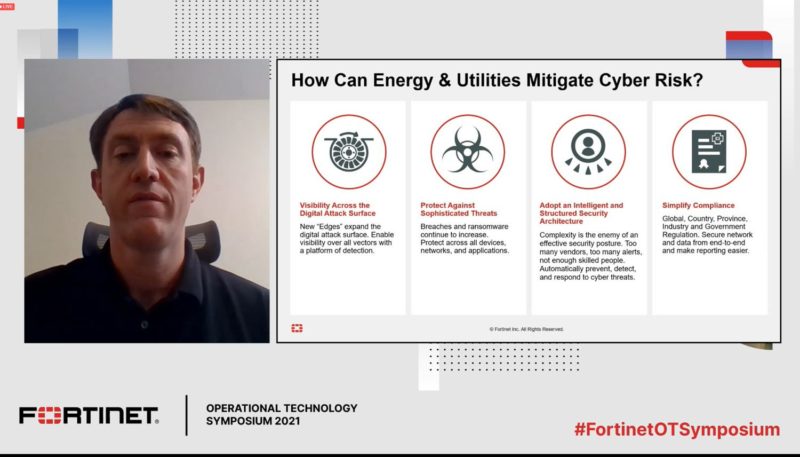
Digital innovation is also causing increased risk, as cyber threats take advantage of the disruption, Blauvelt said. The threat to OT infrastructure is very real, as is the rise in the sophistication and quantity of attacks on critical infrastructure. The big question is: How can energy and utilities protect, defend and respond to attacks?
Blauvelt recommended a standards-driven security implementation. It’s important to embed security within the design process and follow a platform-based approach.
Defense in depth requires multiple layers of security controls throughout the network. These redundant protective schemes can’t stop all cyber threat, but they do help in the event that one control fails. Blauvelt mentioned policies, physical, perimeter, internal network, host, application and data layers as a way to build defense in depth.
The key takeaways from his talk were:
- The digital attack surface is growing with connected digital infrastructure
- We need to identify weaknesses in the digital infrastructure and apply a risk-based approach
- We can devise a holistic cybersecurity strategy by following industry standards
- Companies should choose a platform approach rather than point products
- Remember that cybersecurity doesn’t end with security zones and conduits; it’s a lifecycle
- Audit your security implementation using industry standard compliance frameworks to identify any gaps in the implementation and for continuous improvement.
Closing Keynote: Operational Resilience in The Face of An Increasing Cyber Threat
Dale Peterson, CEO of Digital Bond, closed out the event talking about Operational Resilience in the Face of an Increasing Cyber Threat. Peterson began by discussing the Colonial Pipeline attack and how it acted as a sort of Rorschach test for cybersecurity professionals. The general response was about how people need to use two-factor authentication for remote access and that private industry needed to take a stronger hand by adding more controls to their systems. But Peterson suggested it’s more important to focus on the consequence side of the risk equation, or the effects of the attack.
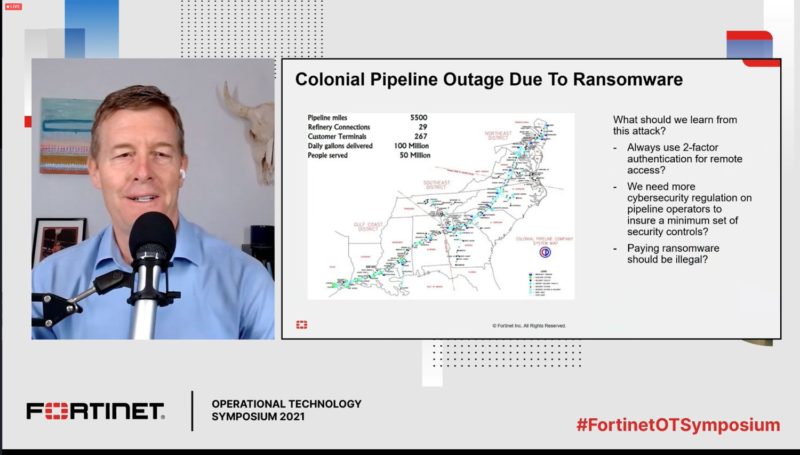
“Colonial should leave you to ask one question: Can I manufacture and deliver products to customers if my IT network is compromised?” Peterson said.
While the Colonial attack apparently never got to the operational technology (OT) network, it still shut down the company’s capability to deliver products, which is a huge and expensive problem. Peterson said security experts should assume their networks are compromised and work on their recovery time objective (RTO).
“How long is it before I can get back up and running? Are you confident you can achieve it?” Peterson said. “The right people need to be asking this question.”
OT consequences should be added to an organization’s risk matrix. As Peterson said, “OT is not a special little flower.” Many executives overestimate what a cyber event means to a company and then rush to add more controls. Peterson said the goal should be to determine what makes a high-consequence event. Is a power plant outage a high-consequence event? On the Eastern seaboard, probably not. They can buy power from elsewhere if the plant goes down. In Maui, where there is only one power plant, it could be a major problem.
When trying to convince executives of the need for more cybersecurity, Peterson suggested stressing consequence reduction is more efficient than risk reduction. Adding additional controls and risk reduction is hard to quantify; working with consequences gives you hard numbers and allows you to speak about cyber threat in a language executives understand.
For more information, check out our recap of Day 1 of Fortinet’s Operational Technology Symposium, Manufacturing Day.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.