Mobility is changing the game in the industrial space. The adoption of mobile devices (cell phones) far exceeds tablets and desktops and is the preferred computing platform today. The younger workforce expects to leverage their mobile devices not just in their personal lives, but at work as well. Many industrial organizations are trying to adopt the bring your own device (BYOD) model. This model can increase industrial applications’ visibility and provide exciting new features. However, there are risks that come with adopting mobile devices. It’s important to understand the risks—and how to mitigate them with tried-and-true security practices.
Mobile devices and web browsers have matured enough for use in the industrial space. They have sensors and features designed to take advantage of technology such as GPS, accelerometers, camera, Bluetooth, and more. These features, if embraced, offer exciting opportunities in the industrial space.
For example, end users could use GPS to automatically navigate to a specific area of the supervisory control and data acquisition (SCADA) system. They could tag their location while changing setpoints, or when moving items in a warehouse, or when entering data. Companies could track personnel for safety reasons.
Many mobile devices have a camera to take pictures or to scan barcodes. End users could print barcodes and put them on each machine to bring up machine manuals, maintenance tickets, and procedures when they’re scanned. They also can track inventory movements through barcode scanning. If there are issues on the plant floor, end users can log the problems with pictures as references or for remote troubleshooting. Mobile devices can make data more accessible and also can provide remote access to a company’s applications.

Mobile devices are changing the way we acquire, view, store, analyze, and act on data and information. Vendors and end users have to adapt to this changing landscape.
Making the right security moves
First, end users need to embrace Wi-Fi to leverage mobility. End users have been hesitant to embrace Wi-Fi for many reasons. Security is the number one concern. Mitigate wireless risk in the following ways.
- Use encrypted communications.
- Ensure each operator has a separate login.
- Use strong passwords and change them often. Today, federated identity providers can provide password management with two-factor authentication (2FA) and single sign on (SSO).
- Turn on auditing to track all changes.
- Use role- and zone-based security to lock down the applications-based user identity and location, to avoid risk from unintended remote machine operation.
Operations technology (OT) and information technology (IT) also need to work together to provide a high level of security. OT needs to take advantage of the technology and run operations while IT can be an asset with management, maintenance, security and backups.

Vendors, especially for SCADA software, have to adapt to mobility as well. The biggest problem is most platforms in the industrial space are not designed to work with mobile devices. Many packages will only work on specific operating systems, which won’t run on Apple iOS and Google Android devices.
Many packages have gained mobile support by adapting one technology for another. For example, a desktop application framework could run on a server in a headless mode while piping an image to a mobile device. End users can view and interact with the data, but there are compromises. End users end up with piecework software whenever one technology is adapted to another. It also doesn’t provide the full functionality and is harder to maintain. It’s important the platform has native support for web and mobile devices through native apps. This is forcing software vendors to get with the times. Make sure the SCADA package has native support for this technology so users can take advantage of opportunities and avoid piecework software.

Protect data
Another concern with mobility is that sensitive information can leave the plant with the devices. It is important to understand how mobile applications work. In most cases, information is not necessarily leaving the plant. An operator may gain access to the application and information remotely, but that information may not reside on the device itself. Typically, these systems rely on a connection to a server in the plant. If the user is remote, the device also will rely on a virtual private network (VPN) connection to the plant. The mobile device cannot function without the connection to the server in the plant. Data is stored either in the server or in a structured query language (SQL) database on the premises.

Even with that, certain data can leave the plant if it can be exported or saved on the mobile device. The device also has sensitive information such as VPN connection information, cached credentials, the 2FA application and more. If the device is lost, it’s vital the industrial apps are wiped and plant access is terminated. Fortunately, this is standard practice today. For example, Apple has mobile device management (MDM), which allows a business to remotely wipe a phone or tablet if it’s lost or stolen. Also, VPN access and user credentials can be disabled so there is no external access to the plant. OT and IT can work together to identify the risks and put action plans in place. This is already standard practice in the IT space and needs to be brought into the industrial space.
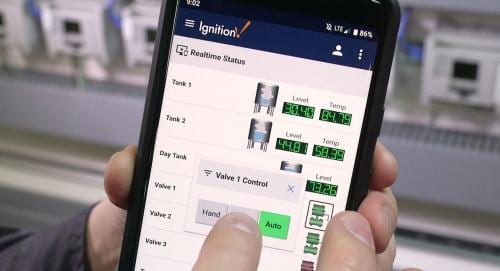
While mobility comes with changes and risks, the potential benefits far exceed the risks since they can be mitigated with best security practices. Embracing mobile technology will allow operations to provide more access to users in the organization. Users have mobile tools that allow them to view, store and analyze data like never before.
Travis Cox is co-director of sales engineering at Inductive Automation. Edited by Chris Vavra, production editor, Control Engineering, CFE Media, cvavra@cfemedia.com.
MORE ANSWERS
Keywords: mobile devices, cybersecurity
The adoption of mobile devices far exceeds tablets and desktops and is the preferred computing platform today.
Data security and information security are crucial when learning and understanding how mobile applications work.
The potential risks of mobile devices need to be considered in light of their potential benefits.
Consider this
What best practices and policies does your company have with mobile devices on the plant floor?
See additional facilities stories including:
Case study: Eight steps to managing building cyberphysical risks
Case study: Eight steps to managing building cyberphysical risks
When remote monitoring and control becomes essential for manufacturing operations
When remote monitoring and control becomes essential for manufacturing operations
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








