
Throwback Attack: German nuclear plant cyberattack is a wake-up call
In 2016, Gundremmingen nuclear power plant was one of the few reported cyberattacks on a nuclear power plant in Europe
Home | Facilities | View All

In 2016, Gundremmingen nuclear power plant was one of the few reported cyberattacks on a nuclear power plant in Europe

Honda was hit by a ransomware called SNAKE ransomware, an industrial control system-specific malicious malware.

An ethical hacker drops a DDoS attack on a children’s hospital, threatening critical infrastructure and the patients.

Nuclear power plants are one of the most efficient ways to produce energy. At the same time, they can be dangerous because of the potential devastation from a meltdown or explosion. Either scenario would result […]

As society has delved deeper into the fourth — and soon to be fifth — industrial revolution, technology has become more woven into our everyday lives. Once upon a time, smart technology was found only […]

Gartner estimates that by 2023, 75% of organizations will restructure risk and security governance to address converged information technology (IT), operational technology (OT), Internet of Things (IoT) and physical security needs – an increase from fewer […]

Founded in 1964, Priefert Manufacturing is one of the largest farm, ranch and rodeo equipment manufacturers in the world. With a huge range of equipment in locations that span several acres in the U.S., it is […]

On May 5, 2022, The U.S. Department of Transportation’s Pipeline and Hazardous Materials Safety Administration (PHMSA) issued a Notice of Probable Violation (NOPV) and Proposed Compliance Order to Colonial Pipeline Company for close to $1 […]

Researchers are pushing to outpace hackers and develop stronger protections that keep data safe from malicious agents who would steal information by eavesdropping on smart devices. Much of the work done to prevent these “side-channel […]

Current methods of defending critical energy infrastructure from multistage, cyber-physical threats remain largely dependent upon human intervention and compartmentalized monitoring with an emphasis on prevention. But how can electric power utilities quickly and effectively respond […]

When the city of Oldsmar, Florida, held a press conference in February 2021 to disclose what they called “an unlawful intrusion into the city’s water treatment system,” it raised alarm bells not only in the […]

As the manufacturing industry adopts digitized operations and the industrial internet of things (IIoT), sensitive data and online systems become increasingly vulnerable to theft and manipulation. SecureAmerica Institute (SAI) partners at The University of Texas at […]

While governments and organizations are attacked daily, some attacks leave little, if any, damage. It really depends on the sophistication level of the threat actor, which varies with each hack. However, there can be a […]

In April 2020, Israel suffered a cyberattack on their water facilities were lucky enough to avoid the consequences. The threat actors attempted to hack into the industrial control systems (ICS) of five Israeli Water Authority […]

Industrial Internet of Things (IIoT) systems and Industry 4.0 have been touted as the key to next-generation productivity. In a rapidly digitizing business environment, taking advantage of the most efficient and powerful technologies is a […]

The world has been full of threats in the past couple of years. We have seen potential wars, actual invasions, a worldwide pandemic and so much more. It is hard to keep track of it […]

Communication is vital to managing every part of a business. In each communication within your company and between your company and external entities, you’re exchanging information. Some of that information might be simple pleasantries or […]

The FBI’s Internet Crime Complaint Center (IC3) has released their 2021 Internet Crime Report. A key focus of the Internet Crime Report is on ransomware. Ransomware is a form of malware that encrypts data on […]
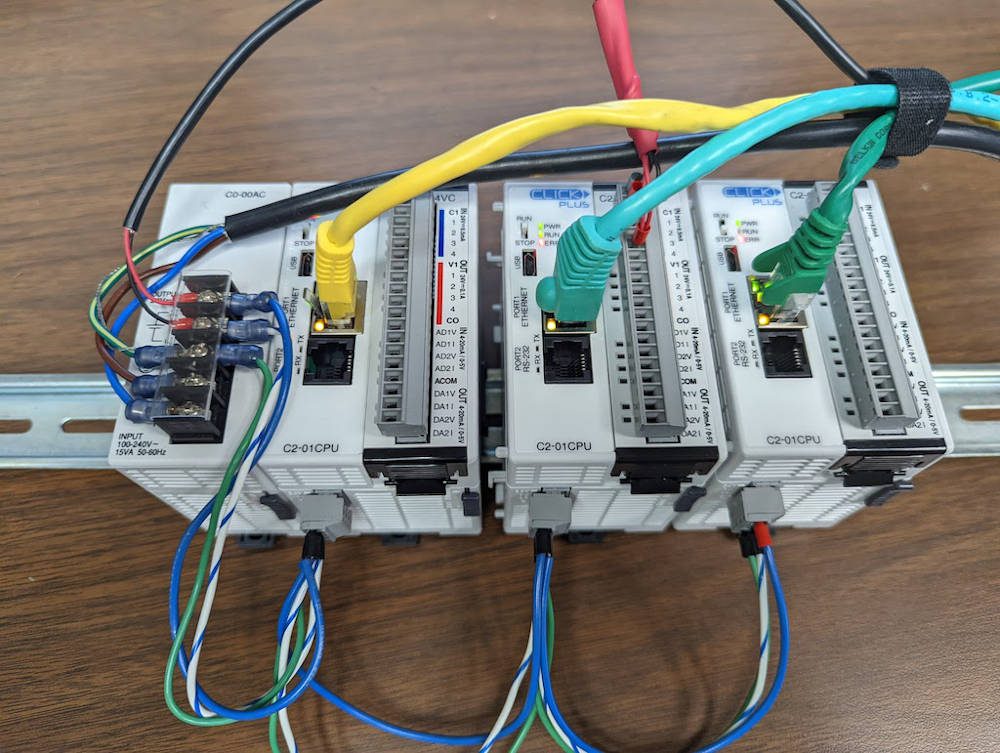
Southwest Research Institute has developed technology to help government and industry detect cyber threats to industrial networks used in critical infrastructure and manufacturing systems. SwRI funded the research to address emerging cyber threats in the […]

While much of cybersecurity focuses on protecting information technology (IT) systems, data and intellectual property, digital transformation has changed the game. As more systems are connected to the internet through the Industrial Internet of Things […]

Automation is the use of equipment to automate systems and production processes to reduce work. While factory automation and robotic innovations are thriving in the U.S., the country has fallen behind in utilizing automation for manufacturing. […]

In the midst of the Cold War, the Central Intelligence Agency (CIA) launched a trojan horse code, dubbed a logic bomb, on the Soviet Union. This attack would go down in history as one of […]

Energy infrastructure is a large sector. It has evolved in the past 200 years and is still evolving. From mechanical to electronics to sophisticated control system technologies, it has helped improved the usage and efficiency […]

Industrial robots generate billions of data points that can be used to measure and optimize robot performance, provide predictive maintenance and to drive advanced analytics. Digitalization of the industrial sector is certainly on the increase […]

Any software that is purchased today will include a lot of code created by third parties, whether they are open-source communities — like the Apache Foundation — or for-profit companies — like Microsoft. Today’s industrial […]

On March 21, President Biden released a statement discussing the United States’ cybersecurity concerns over potential Russian cyberattacks. Russia began its invasion to claim Ukraine a month ago, setting the world on high alert for […]

Every year, the UK government conducts its “Cyber Security Breaches Survey” to help organizations understand the cyber security threat landscape, including the impact of breaches and how breaches occur in the first place. Regarding how […]

As the current conflict between Russia and Ukraine worsens, U.S. agencies have advised that there could be Russian malware originally designed to target Ukraine that leaks to other countries, including the U.S. and NATO allies. […]

The threat of the Russian invasion of the Ukraine has been at the forefront after years of tension between the two and months of clear warnings. As of today, explosions erupted and President Vladimir V. […]

Every year brings new data breach victims. According to the data presented by the Atlas VPN team, the volume of publicly reported data compromises in the United States reached a record-high of 1,862 in 2021, […]

OT cybersecurity governance: Who has authority? Who is accountable? These are perhaps the two most important questions in reducing cyber risk to operations. There are “big G” governance questions such as: Who should set the […]

CISA released two alerts on threats to critical infrastructure operations. The first was an alert about a series of attacks on water and wastewater systems over the past year, primarily relating to ransomware but also […]

Almost one year ago, on Feb. 8, 2021, public officials from the city of Oldsmar, Florida, held a press conference to disclose what they called “an unlawful intrusion into the city’s water treatment system.” An […]
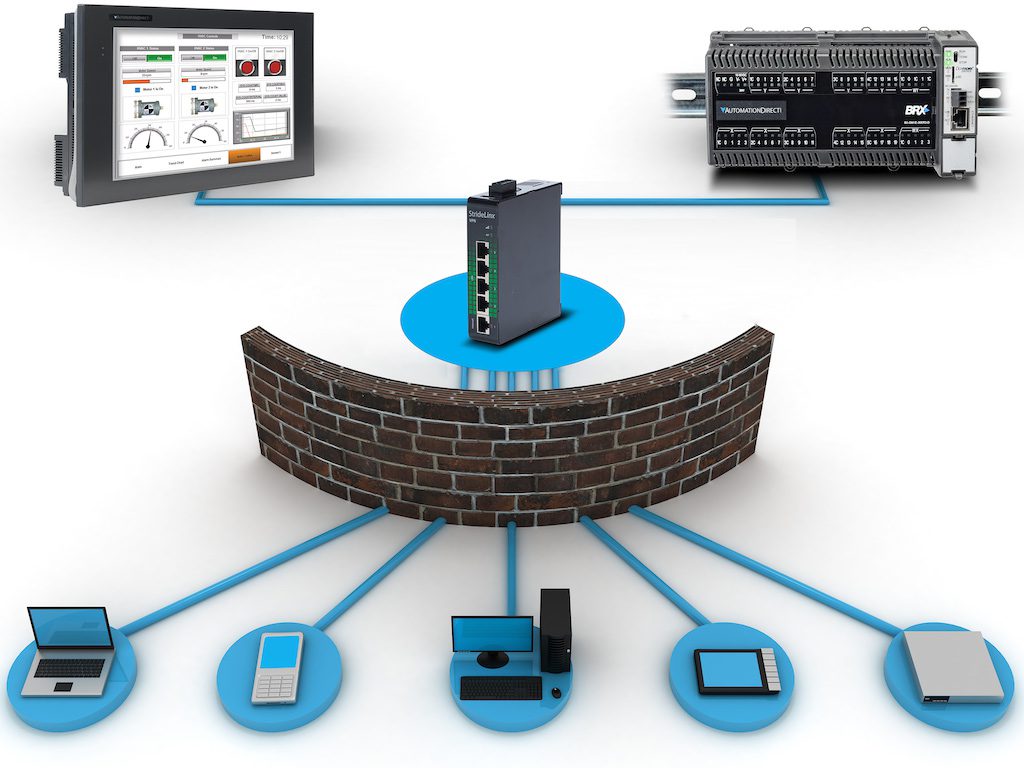
Industrial cybersecurity leaders – including the C-suite, CISOs, security teams, and operational leaders – are realizing the potential financial, operational and safety impact of cyber events. Attempting to get their hands around securing this challenging […]
Industrial automation project designers have rightfully maintained a primary focus on delivering correct and reliable equipment functionality. However, now that most intelligent automation devices include wired or wireless connectivity, and end users are increasingly looking […]
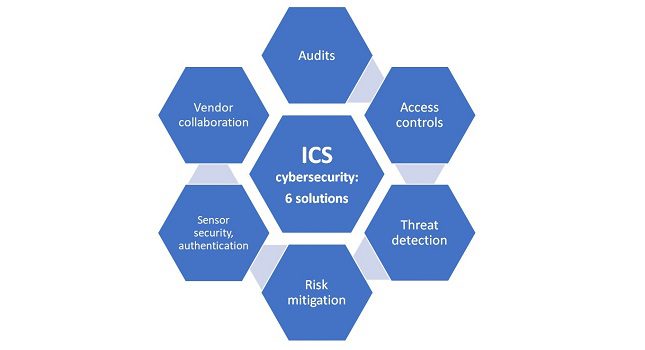
Learning Objectives Examine six ways to approach industrial cybersecurity. Look at internal and external industrial cybersecurity threats, without silos. Learn that legacy process sensors lack cybersecurity protection. With significant security risks and attacks against industrial […]

When companies or governments are attacked, they call in the experts. But what happens when a leading cybersecurity firm is hit? Threat actors are always evolving their tactics and finding new targets. In 2020, FireEye […]

Port and maritime operations are critical to the stability of the global supply chain and the global economy. When terminals cannot move cargo, the costs can escalate. When shipping giant Maersk fell victim to NotPetya […]

Business disruption that results from ransomware attacks is costly on many levels. Downtime, mitigation expenses and reputational costs can run anywhere from hundreds of thousands of dollars to shutting a business down for good. Recent […]
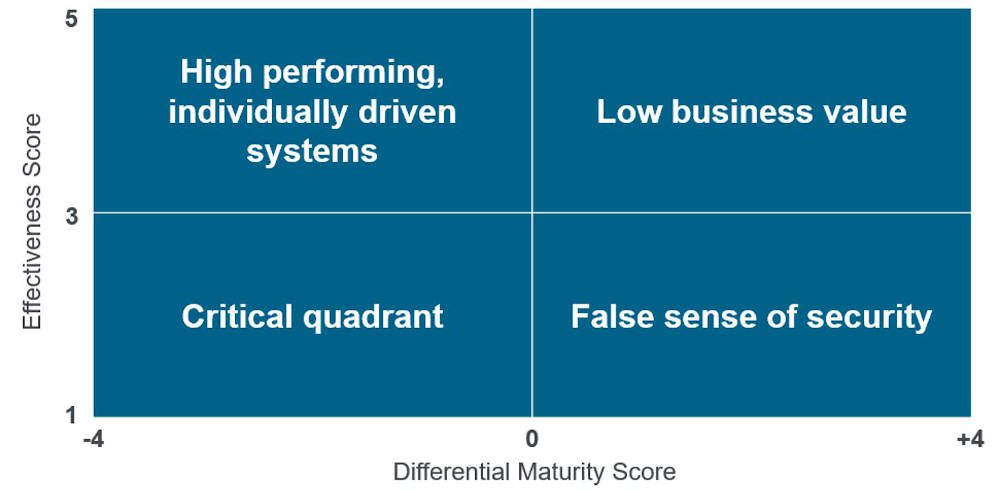
Many articles focused on cybersecurity stress how important it is to secure an industrial control system (ICS) and share ways to implement this security. In this article, the assumption is this advice has already been […]
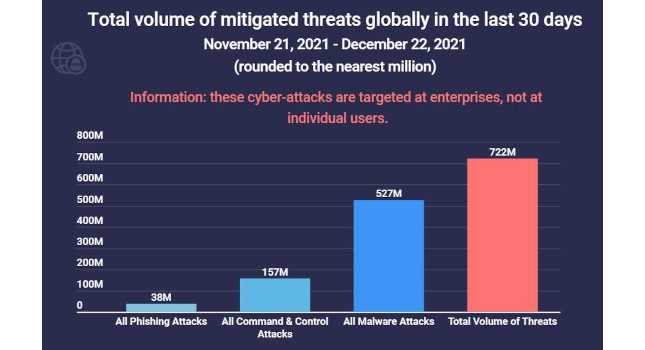
According to data compiled and analyzed by Atlas VPN, threat actors attacked businesses more than 722 million times during the last 30 days worldwide. More than 73% of these hacking attempts were malware attacks. Atlas VPN […]

When an organization does not take advantage of potential synergies between information technology (IT) and operational technology (OT), it might be leaving plant floor systems open to attack. In many organizations, the lines of communication […]
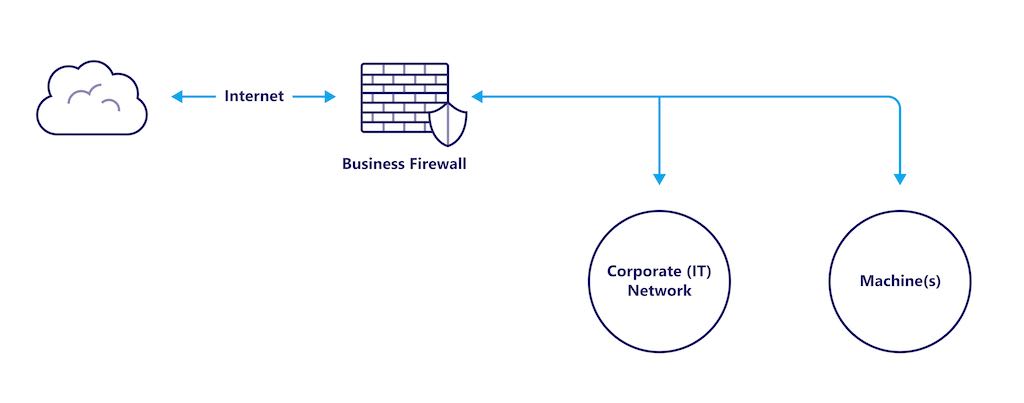
As I started delving into cybersecurity, I realized I didn’t know what I didn’t know. My mental image consisted of dark rooms, high caffeine beverages and green computer screens. I even didn’t understand where to […]
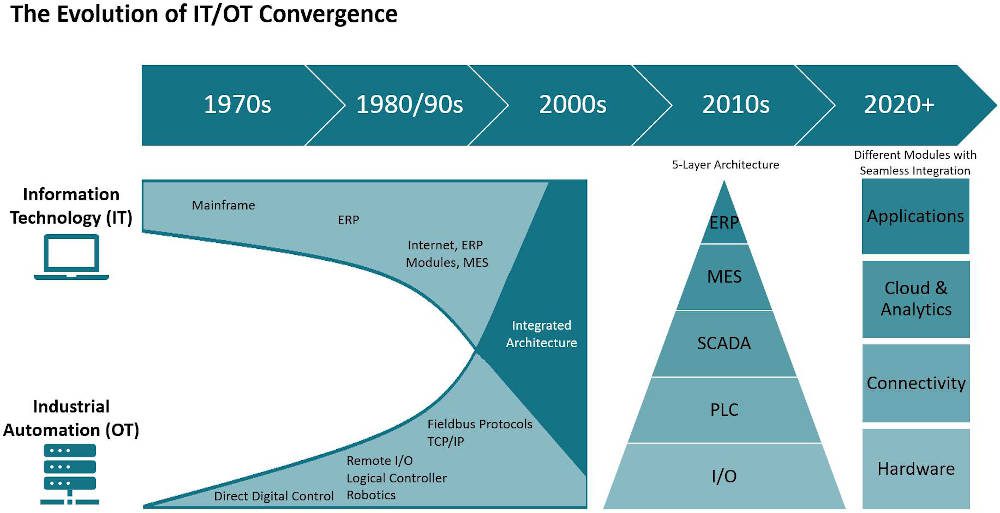
The technologies that make up a company’s industrial operations today are evolving faster than ever. Competing platforms leapfrog each other for market dominance and user preference, while start-ups flush with cash from investors shake up […]

NovaSource Power Services (NSPS) is the insight and operations and management (O&M) services partner for owners of renewable assets ready to fuel smart growth. They manage the largest solar projects in the world, and deliver […]
Until recent decades, operational technology (OT), which involves the monitoring and controlling of physical machinery and equipment, was manually managed by human workers. As information technology (IT) relies on computers for operation, its integration into […]
The holidays may be a time for celebration, but families aren’t the only ones who see these festive occasions as the most wonderful time of the year. Hackers know that due to low staffing levels […]

As people count down the days until Thanksgiving, it’s the perfect time to take a look at what happened around this time last year in Baltimore. A year and a half after the Robinhood ransomware […]

The North American Electric Reliability Corporation (NERC) maintains the critical infrastructure protection (CIP) security standards. These protocols coordinate security practices for major electricity providers across both the United States and Canada. Among them is NERC […]

Critical infrastructure is increasingly under attack with major hits on oil pipelines, water treatment facilities and the food and beverage sector all occurring within the last year. Regardless of where the attackers enter from — […]

Threat actors are always on the lookout for pain points — manufacturing systems that can’t afford to go offline, critical infrastructure that can cause disruptions to everyday life or risks to human safety and, unfortunately, […]
The energy market has had rapid increases in demand that cannot be fulfilled with carbon-based fuels. It requires companies to use renewable energies such as solar and wind to keep up. What’s needed is an […]
Cybersecurity in the industrial sector is changing, and the need to look toward the future is ever present, but it is also essential to examine the past and learn from it. Now, threat actors are […]
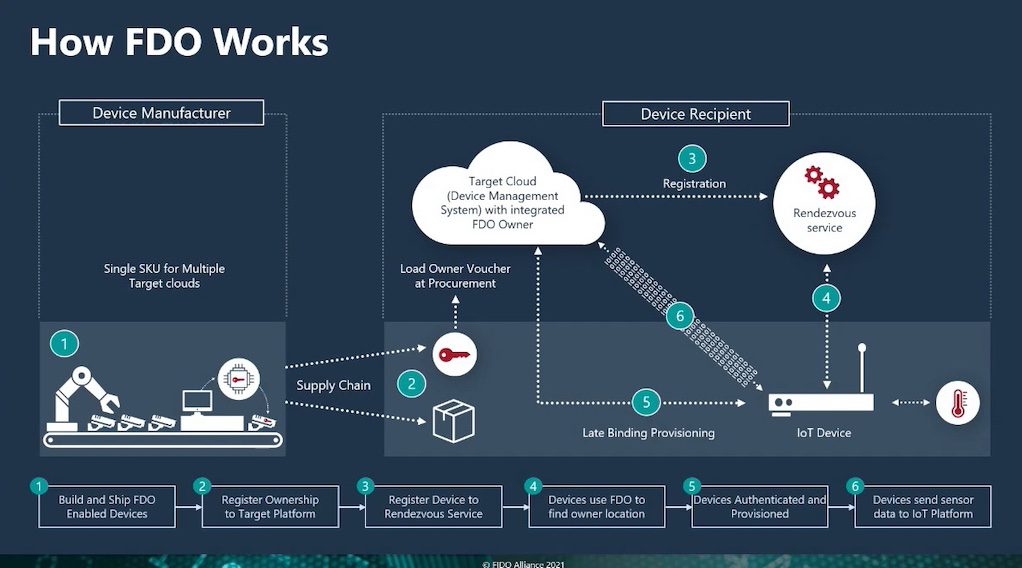
The manufacturing sector is becoming more interconnected as the Internet of Things (IoT) allows data to be transferred from many devices. IoT device security is critical, and configuring credentials, a process called onboarding, is a […]

Cybersecurity insurance is an increasingly important weapon in the risk management arsenal of today’s enterprises. Unknown just a decade ago, these popular policies now offer organizations a crucial hedge against risks that defy routine assessment, […]

When people think of Rye Brook, New York, an idyllic hamlet in Westchester Country sometimes known as Tree City USA, they don’t generally picture international intrigue. That’s best left to its more cosmopolitan neighbor, Manhattan, […]
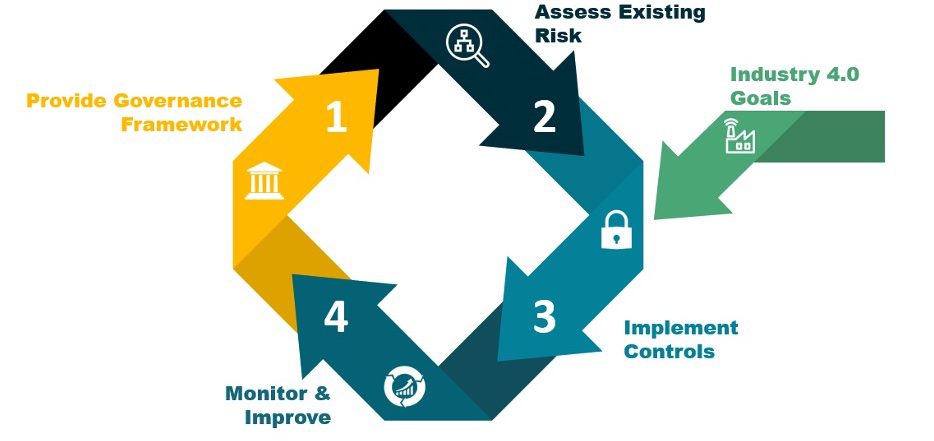
Learning Objectives Cybersecurity attacks against manufacturers and other industrial sites are growing every year. When developing a cybersecurity plan, is best to look at it through the lens of business risk reduction and enabling innovation. […]
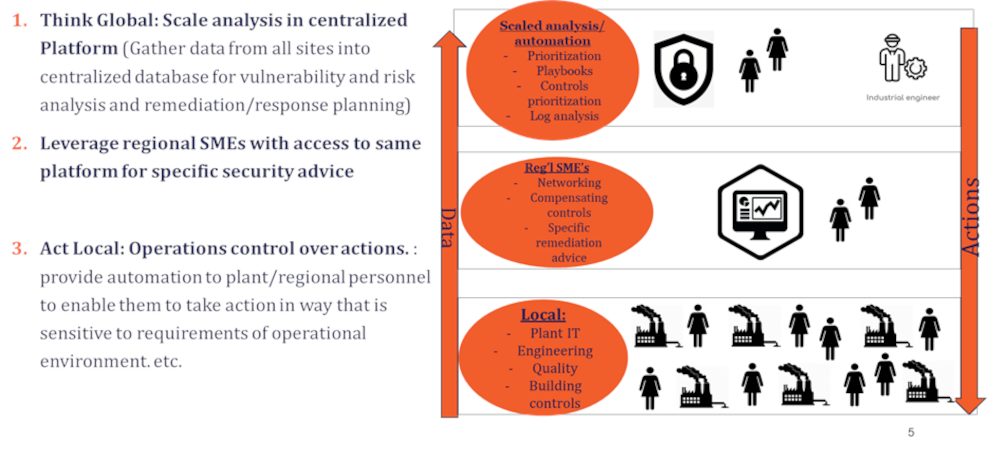
On May 27, the United States Department of Homeland Security (DHS) announced its initial regulatory response to the Colonial Pipeline ransomware attack. As the Security Directive highlighted, this is only the first step in what is likely […]

Who is responsible for the security of technology and networks? That’s probably information technology (IT). But who is responsible for all the web-enabled, and therefore vulnerable, devices on the plant floor? Unfortunately, that’s still a […]

Ransomware attacks are a growing threat to critical infrastructure and private industry worldwide. While every business sector has felt the sting of ransomware, few have been harder hit of late than health care. In April […]

Connected capabilities offer a great deal of potential for building systems. Connected HVAC, lighting, alarms, fire protection and more are all key components of smart buildings currently in demand. These capabilities offer exciting opportunities for […]

Most cybersecurity frameworks say visibility is essential. Manufacturers need to know exactly which assets are in their environment

The concept and benefits of a software bill of materials (SBOM) are simple to understand. SBOMs are a list of all software in an application or cyber asset. Vendors need to create and maintain an […]

As the pace of cyberattacks on both the public and private sectors has continued to increase, it’s become clear that improved cybersecurity is in the national interest. Since the Biden administration assumed power in January […]

During the second Bush Administration, there was great concern about the rapid progress of the Iranian enrichment program, which would likely lead to the attainment of weapons-grade uranium. The center of that operation was, and […]

Given the proliferation of technology in industrial control systems, it’s high time for OT teams to own their cybersecurity practice

Building automation systems deploy thousands of smart devices across open networks, and the increased connectivity to the worldwide web, combined with unclear system ownership creates a large and vulnerable attack surface. In this article we will […]

A distributed denial of service (DDoS) attack is a malicious attempt to sabotage a network by overwhelming its ability to process legitimate traffic and requests. In turn, this activity denies the victim of a service, […]

Building automation systems have become a soft target for cyberattacks due to the large numbers of intelligent devices connected over open networks, sophisticated threats designed to attack control systems, as well as dependency on third-party […]

Ransomware attacks on the health care industry skyrocketed in the last year as bad actors looked to profit from the chaos brought on by the COVID-19 global pandemic. But health care and ransomware have a […]

The ISA Global Cybersecurity Alliance (ISAGCA), along with admeritia GmbH (admeritia), announced the release of the Top 20 Secure PLC Coding Practices document. The document aims to provide a list of coding practices for programmable […]

What are the top 10 cyber risk manufacturing questions board members should be asking? According to a cyber risk in advanced manufacturing study led by Deloitte’s Center for Industry Insights, nearly half of the executives […]

Building automation systems have become a soft target for cyberattack. This is due to the large number of intelligent devices, open network protocols and increased reliance on third-party vendors and service providers. Automated cybersecurity monitoring […]

IT/OT convergence isn’t just a concept, a catchy mnemonic, nor a convenient abbreviation jumble It’s a very real and significant challenge facing manufacturers. At the crux of the issue is how information technology (IT) and […]

Ransomware may be grabbing the headlines of late, but cyberattacks can hurt companies and communities in places far worse than their wallets. In 2015, details emerged from a cyberattack that caused “massive damage” to a […]

The wave of ransomware attacks on high-profile industrial manufacturers continues apace, as the world’s largest meat processor, JBS, was forced to shut down several plants in the United States earlier this week. JBS USA released […]

Industrial control system (ICS) security is growing in importance as cyber-attacks increasingly focus on physical processes for either ransom or to cause harm to critical production systems. Attacks such as the Oldsmar water treatment plant, […]

Trade disputes are not uncommon in a competitive marketplace, whether they’re between companies or economic superpowers. But in 2014, the U.S. Department of Justice (DOJ) charged five Chinese military hackers with taking their trade war […]

The Colonial Pipeline downtime created by the cybersecurity attack on the operators’ information technology (IT) systems underscores the need for resilient, redundant and responsible processes that enable operations to persist in the face of digital […]

Much of the attention that cybersecurity gets is on the IT or office network side of things, but recently people have begun paying more attention to operational technology (OT) systems that make up our critical […]

To pay or not to pay: It’s an essential and fraught question in regards to ransomware attacks. When multinational aluminum manufacturer Norsk Hydro was hit with a cyberattack in 2019, they chose not to pay […]

How a company responds to an incident is important. The wrong response could damage the company’s reputation or destroy it altogether. A proactive and timely response to an incident can result in great press and […]
The Department of Defense is rolling out the CMMC to help standardize cybersecurity processes for defense contractors and vendors

News that a ransomware attack shut down the pipeline that provides the East Coast with nearly half of its fuel sent shockwaves through the energy and cybersecurity communities earlier this week. Though a cyberattack has […]

Over the weekend, Colonial Pipeline, owner of 5,500 miles of pipeline carrying natural gas, gasoline, and diesel from Texas to New Jersey, shut down its operations in response to what it said was a ransomware […]

The vulnerability of U.S. critical national infrastructure was again thrown into sharp relief when a ransomware attack shut down a pipeline that provides the East Coast with nearly half of its diesel, gasoline and jet […]

A vulnerability is a weakness in a computing resource that can be exploited to cause harm. Mitigating vulnerability risk is accomplished through an effective vulnerability management program that includes vulnerability monitoring, vulnerability risk assessment, and vulnerability mitigation […]

The majority of cybersecurity efforts are focused on preventing outside bad actors from hacking into systems or installing destructive malware – and rightfully so. But there is also a sizable risk from disgruntled employees walking […]
Why are ransomware attacks on the rise versus traditional cyberattacks? Axis Communications’ Wayne Dorris offers his thoughts

Lessons can be learned from prior cybersecurity efforts, even older ones, as this 2007 demonstration showed. Are you aware of the eight ways to mitigate the Aurora vulnerability? In 2007, the Department of Homeland Security, […]

In 2017, auto manufacturer Renault-Nissan became one of many organizations around the world to fall victim to the WannaCry ransomware. While WannaCry was effectively halted within a few days of its discovery, it was one […]

Now that the dust has settled a bit around the cyber attack at the Oldsmar water facility in Florida, and everyone has made their sales pitch, this is a good time to highlight some of […]
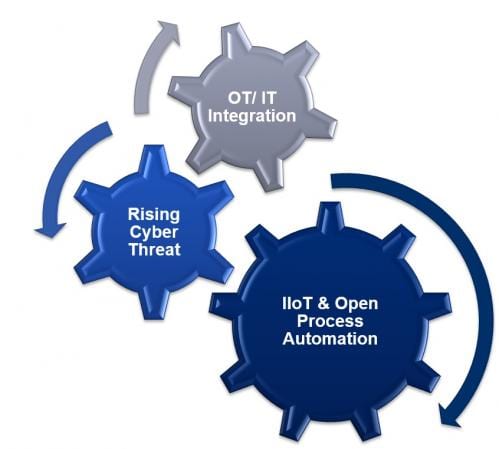
A combination of information technology (IT) and operations technology (OT) cybersecurity expertise is required to manage the influx of Industrial Internet of Things (IIoT) devices and increased IT/OT integration.

In 2017, the NotPetya malware was wreaking havoc around the world. Though it likely began as a state-sponsored Russian cyberattack targeting Ukraine, its ramifications quickly spread far and wide, including to multinational corporations like Chicago-based […]

The proliferation of the Internet of Things (IoT) is making buildings more complex and dynamic, with hundreds of devices connecting to disparate systems to perform a wide range of functions like energy management, physical security […]

In 2007, the late Mike Assante blew up a 27-ton diesel generator with 30 lines of code, demonstrating to officials from the Department of Homeland Security the destructive potential of cyberattacks targeting critical infrastructure. Cyberattacks […]
Iran’s Natanz nuclear facility attack underscores the importance of protecting critical OT systems as well as IT systems
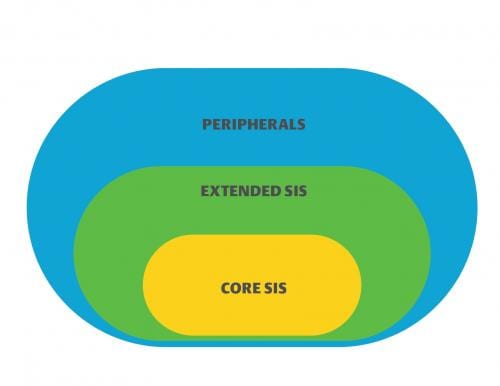
Choosing a safety instrumented system (SIS) architecture for defensible operation across the product lifecycle is one of the first decisions an organization must make; know these applicable standards.
The work from home trend is more than just a blip on the radar. What does that mean for industrial manufacturers and cybersecurity

The MITRE ATT&CK for ICS Matrix provides a common nomenclature that allows asset owners, security researchers and consultants, internal defenders and product vendors to better communicate about adversary techniques. Nothing in it is new to […]

Cyberattacks on industrial manufacturing and government facilities have been on the rise, but securing facilities takes more than just a shrewd and effective information technology (IT) department. There also needs to be buy-in from operational […]

When most people think of hackers, they picture grizzled, bearded adults sitting in darkened rooms spotlit by the glow of multiple monitors. Or perhaps hardened foreign operatives covertly working for government agencies. If the movie […]

Cybersecurity: Improving evaluation and certification methods, security audits, and testing provide a foundation for evaluating Industrial Internet of Things (IIoT) devices.

When it comes to industrial cybersecurity, there has long been a partition between the information technology (IT) and operational technology (OT) sides. The IT/OT divide isn’t exactly the Sharks versus the Jets, but it is […]

Organizations have distributed data and workloads across cloud environments and on-premises data centers. As a result, IT teams have to deploy, manage, and secure increasingly complex and hybrid networks. And even though many organizations have moved […]

Multinational brewery and beverage manufacturer Molson Coors was recently hit with a damaging cyberattack, but they’re far from the first adult beverage company to find themselves in hackers’ crosshairs. In August 2020, U.S. spirits and […]

Two leading methods exist for establishing mobile human-machine interface (HMI) connectivity; one providing more cybersecurity. See table comparison of remote access HMI connections.

Another major company has fallen victim to a cyberattack that has caused significant disruptions to its business operations. In an SEC filing, Chicago-based brewing and beverage company Molson Coors recently acknowledged they experienced a systems […]

The world we live in is not the same world we once knew. Unprecedented global events and new technological advances are forcing manufacturers to adapt and work in an ever-evolving, more remote business environment. Change […]

Cyberattacks in manufacturing are on the rise. So how should the industry respond to this increasing threat? It takes organization, buy-in and cybersecurity maturity. Awareness of the need for cybersecurity has been growing, as attacks […]

Mission Secure, an industrial control system (ICS) cybersecurity technology company, appointed John Adams as Chief Executive Officer (CEO). He will succeed David Drescher, who will remain with the board of directors. “A generational shift has […]

Most people would assume having security cameras at a facility provides peace of mind and offers additional protection. However, when everything from televisions to security cameras are connected to networks, they also can open up […]
This case study documents a cyber journey and cyberrisk mitigation strategy implemented on operational technology systems in the HDR office building

Manufacturing cybersecurity is less well known but can pose even greater financial, operational and safety risks than information technology (IT) security. The impact can be catastrophic – from disruptions to manufacturing lines, to power outages, […]

Anyone watching the news can see that cybersecurity management is becoming increasingly relevant for industrial companies. Recent analysis performed by insurance carriers indicates that the incidence of cyberattacks faced by manufacturing companies is 30 times […]

Industrial automation cybersecurity has a lot of confusion and questions. Learn about changing trends and effective best practices for operations technology (OT) providers.

The Industrial Internet of Things (IIoT) will have the strongest impact on operational technology/industrial control system (OT/ICS) cybersecurity.

The Cost of Insider Threats Report by IBM indicated the overall damage by negligent or malicious employees totaled $11.45 million. Whereas intentional insider criminals cause only 14% of the accidents, their damage adds up to […]

Cybersecurity is a relatively recent top concern for industrial enterprises. A number of high-profile security incidents like the hacking of a Florida water treatment plant, have brought the topic into public scrutiny, but the issue […]

Having comprehensive list of security-related patches by using operational technology (OT)-specific patching tools to gather complete software, vulnerability, and security patching information sounds simple. Information technology (IT) security professionals will tell users to scan it […]

IoT and intelligent management systems have revolutionized the capabilities of our buildings by enabling better automation and increasing efficiencies for better overall building health
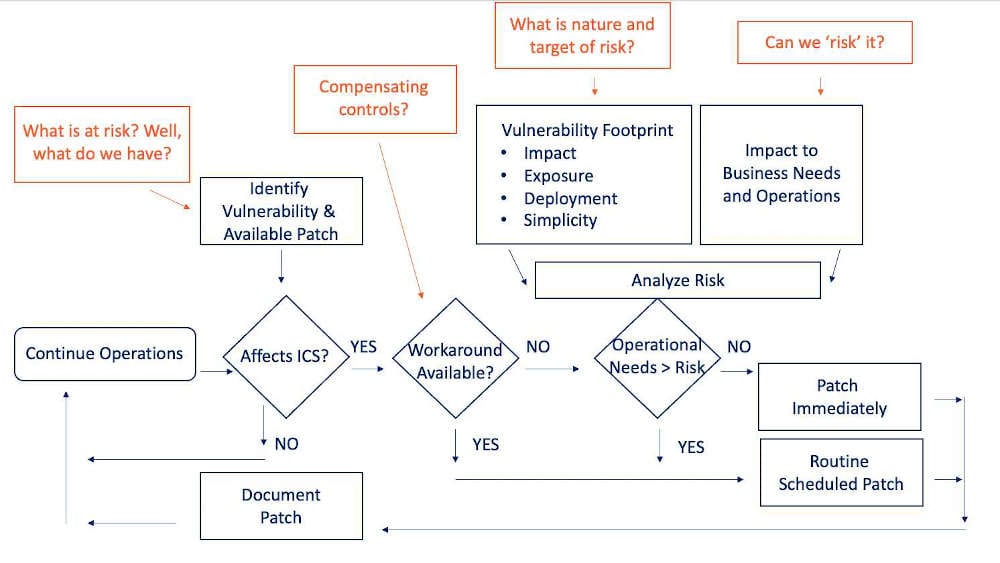
Most operational technology (OT) environments use scan-based patching tools, which are pretty standard but not overly insightful to show us what assets we have and how they are configured. What is really needed is robust […]

The COVID-19 pandemic is forcing companies to adjust their business practices and settle to a new normal. See four tips on how edge computing and the Industrial Internet of Things (IIoT) can help companies adjust.

For a robot to be safe, it must also be secure from cyberattacks in the age of Industrie 4.0 and the Industrial Internet of Things (IIoT). Everyone in the information technology (IT) and operations technology (OT) departments are responsible for ensuring this happens.

Hot on the heels of the high-profile SolarWinds attack comes the Oldsmar water treatment facility attack. This one is more targeted and focused on a specific – and very critical – piece of infrastructure. A […]
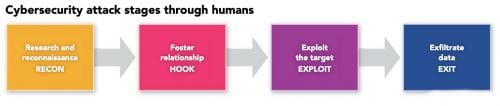
Cybersecurity education: Human hacking, the compromise of human assets, is often the first step in a cybersecurity breach, even if or when technical systems are secure. Help coworkers and those in your supply chain to avoid being the entry point for attack. Learn attack methods, five attack types and five prevention techniques.

What does OSHA teach us about industrial cybersecurity? Clearly, high cybersecurity risk could increase risk of industrial accidents, but OSHA’s model can help in other ways. Prior to 1970, worker safety in industrial settings was […]

Protecting programmable logic controllers (PLC) and programmable automation controllers (PAC) from security threats should begin even before an attack is detected.
Learning Objectives Cybersecurity global standards from IEC, ISA Global Cybersecurity Alliance and UL help lower risk. Cybersecurity education and training. The Industrial Internet of Things (IIoT), connected devices and the vast amounts of generated data create industrial […]
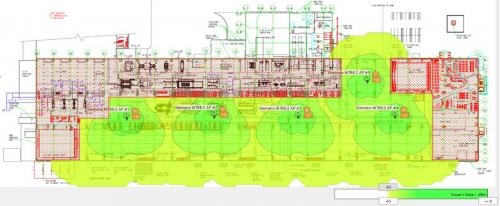
Deployments and optimal operation of industrial wireless local area networks (LANs) require attention to site survey, lifecycle management, cybersecurity and collaboration. Need to optimize existing industrial wireless networks?

When information and operational technology collaborate with business leaders, facility managers gain secure access to the data they need to achieve their sustainability goals

Learn the basic concepts and strategic planning needed to ensure resilient design of hospitals and health care facilities to reduce risk during natural disasters and man-made threats

Cybersecurity is an important aspect of project implementation, and will become critical as information and operations technologies converge.
What is a smart building, and how can engineers design integrated building systems?

Using mobile devices on the plant floor offers many potential benefits, but the right approach is a must because of safety and cybersecurity concerns.
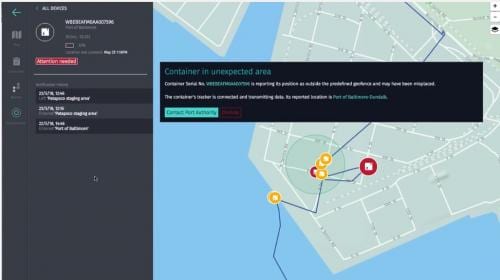
Digital representations of factories and industrial spaces lead to opportunities.

In 2016, Gundremmingen nuclear power plant was one of the few reported cyberattacks on a nuclear power plant in Europe

Honda was hit by a ransomware called SNAKE ransomware, an industrial control system-specific malicious malware.

An ethical hacker drops a DDoS attack on a children’s hospital, threatening critical infrastructure and the patients.

Nuclear power plants are one of the most efficient ways to produce energy. At the same time, they can be dangerous because of the potential devastation from a meltdown or explosion. Either scenario would result […]

As society has delved deeper into the fourth — and soon to be fifth — industrial revolution, technology has become more woven into our everyday lives. Once upon a time, smart technology was found only […]

Gartner estimates that by 2023, 75% of organizations will restructure risk and security governance to address converged information technology (IT), operational technology (OT), Internet of Things (IoT) and physical security needs – an increase from fewer […]

Founded in 1964, Priefert Manufacturing is one of the largest farm, ranch and rodeo equipment manufacturers in the world. With a huge range of equipment in locations that span several acres in the U.S., it is […]

On May 5, 2022, The U.S. Department of Transportation’s Pipeline and Hazardous Materials Safety Administration (PHMSA) issued a Notice of Probable Violation (NOPV) and Proposed Compliance Order to Colonial Pipeline Company for close to $1 […]

Researchers are pushing to outpace hackers and develop stronger protections that keep data safe from malicious agents who would steal information by eavesdropping on smart devices. Much of the work done to prevent these “side-channel […]

Current methods of defending critical energy infrastructure from multistage, cyber-physical threats remain largely dependent upon human intervention and compartmentalized monitoring with an emphasis on prevention. But how can electric power utilities quickly and effectively respond […]

When the city of Oldsmar, Florida, held a press conference in February 2021 to disclose what they called “an unlawful intrusion into the city’s water treatment system,” it raised alarm bells not only in the […]

As the manufacturing industry adopts digitized operations and the industrial internet of things (IIoT), sensitive data and online systems become increasingly vulnerable to theft and manipulation. SecureAmerica Institute (SAI) partners at The University of Texas at […]

While governments and organizations are attacked daily, some attacks leave little, if any, damage. It really depends on the sophistication level of the threat actor, which varies with each hack. However, there can be a […]

In April 2020, Israel suffered a cyberattack on their water facilities were lucky enough to avoid the consequences. The threat actors attempted to hack into the industrial control systems (ICS) of five Israeli Water Authority […]

Industrial Internet of Things (IIoT) systems and Industry 4.0 have been touted as the key to next-generation productivity. In a rapidly digitizing business environment, taking advantage of the most efficient and powerful technologies is a […]

The world has been full of threats in the past couple of years. We have seen potential wars, actual invasions, a worldwide pandemic and so much more. It is hard to keep track of it […]

Communication is vital to managing every part of a business. In each communication within your company and between your company and external entities, you’re exchanging information. Some of that information might be simple pleasantries or […]

The FBI’s Internet Crime Complaint Center (IC3) has released their 2021 Internet Crime Report. A key focus of the Internet Crime Report is on ransomware. Ransomware is a form of malware that encrypts data on […]

Southwest Research Institute has developed technology to help government and industry detect cyber threats to industrial networks used in critical infrastructure and manufacturing systems. SwRI funded the research to address emerging cyber threats in the […]

While much of cybersecurity focuses on protecting information technology (IT) systems, data and intellectual property, digital transformation has changed the game. As more systems are connected to the internet through the Industrial Internet of Things […]

Automation is the use of equipment to automate systems and production processes to reduce work. While factory automation and robotic innovations are thriving in the U.S., the country has fallen behind in utilizing automation for manufacturing. […]

In the midst of the Cold War, the Central Intelligence Agency (CIA) launched a trojan horse code, dubbed a logic bomb, on the Soviet Union. This attack would go down in history as one of […]

Energy infrastructure is a large sector. It has evolved in the past 200 years and is still evolving. From mechanical to electronics to sophisticated control system technologies, it has helped improved the usage and efficiency […]

Industrial robots generate billions of data points that can be used to measure and optimize robot performance, provide predictive maintenance and to drive advanced analytics. Digitalization of the industrial sector is certainly on the increase […]

Any software that is purchased today will include a lot of code created by third parties, whether they are open-source communities — like the Apache Foundation — or for-profit companies — like Microsoft. Today’s industrial […]

On March 21, President Biden released a statement discussing the United States’ cybersecurity concerns over potential Russian cyberattacks. Russia began its invasion to claim Ukraine a month ago, setting the world on high alert for […]

Every year, the UK government conducts its “Cyber Security Breaches Survey” to help organizations understand the cyber security threat landscape, including the impact of breaches and how breaches occur in the first place. Regarding how […]

As the current conflict between Russia and Ukraine worsens, U.S. agencies have advised that there could be Russian malware originally designed to target Ukraine that leaks to other countries, including the U.S. and NATO allies. […]

The threat of the Russian invasion of the Ukraine has been at the forefront after years of tension between the two and months of clear warnings. As of today, explosions erupted and President Vladimir V. […]

Every year brings new data breach victims. According to the data presented by the Atlas VPN team, the volume of publicly reported data compromises in the United States reached a record-high of 1,862 in 2021, […]

OT cybersecurity governance: Who has authority? Who is accountable? These are perhaps the two most important questions in reducing cyber risk to operations. There are “big G” governance questions such as: Who should set the […]

CISA released two alerts on threats to critical infrastructure operations. The first was an alert about a series of attacks on water and wastewater systems over the past year, primarily relating to ransomware but also […]

Almost one year ago, on Feb. 8, 2021, public officials from the city of Oldsmar, Florida, held a press conference to disclose what they called “an unlawful intrusion into the city’s water treatment system.” An […]

Industrial cybersecurity leaders – including the C-suite, CISOs, security teams, and operational leaders – are realizing the potential financial, operational and safety impact of cyber events. Attempting to get their hands around securing this challenging […]

Industrial automation project designers have rightfully maintained a primary focus on delivering correct and reliable equipment functionality. However, now that most intelligent automation devices include wired or wireless connectivity, and end users are increasingly looking […]

Learning Objectives Examine six ways to approach industrial cybersecurity. Look at internal and external industrial cybersecurity threats, without silos. Learn that legacy process sensors lack cybersecurity protection. With significant security risks and attacks against industrial […]

When companies or governments are attacked, they call in the experts. But what happens when a leading cybersecurity firm is hit? Threat actors are always evolving their tactics and finding new targets. In 2020, FireEye […]

Port and maritime operations are critical to the stability of the global supply chain and the global economy. When terminals cannot move cargo, the costs can escalate. When shipping giant Maersk fell victim to NotPetya […]

Business disruption that results from ransomware attacks is costly on many levels. Downtime, mitigation expenses and reputational costs can run anywhere from hundreds of thousands of dollars to shutting a business down for good. Recent […]

Many articles focused on cybersecurity stress how important it is to secure an industrial control system (ICS) and share ways to implement this security. In this article, the assumption is this advice has already been […]

According to data compiled and analyzed by Atlas VPN, threat actors attacked businesses more than 722 million times during the last 30 days worldwide. More than 73% of these hacking attempts were malware attacks. Atlas VPN […]

When an organization does not take advantage of potential synergies between information technology (IT) and operational technology (OT), it might be leaving plant floor systems open to attack. In many organizations, the lines of communication […]

As I started delving into cybersecurity, I realized I didn’t know what I didn’t know. My mental image consisted of dark rooms, high caffeine beverages and green computer screens. I even didn’t understand where to […]

The technologies that make up a company’s industrial operations today are evolving faster than ever. Competing platforms leapfrog each other for market dominance and user preference, while start-ups flush with cash from investors shake up […]

NovaSource Power Services (NSPS) is the insight and operations and management (O&M) services partner for owners of renewable assets ready to fuel smart growth. They manage the largest solar projects in the world, and deliver […]

Until recent decades, operational technology (OT), which involves the monitoring and controlling of physical machinery and equipment, was manually managed by human workers. As information technology (IT) relies on computers for operation, its integration into […]

The holidays may be a time for celebration, but families aren’t the only ones who see these festive occasions as the most wonderful time of the year. Hackers know that due to low staffing levels […]

As people count down the days until Thanksgiving, it’s the perfect time to take a look at what happened around this time last year in Baltimore. A year and a half after the Robinhood ransomware […]

The North American Electric Reliability Corporation (NERC) maintains the critical infrastructure protection (CIP) security standards. These protocols coordinate security practices for major electricity providers across both the United States and Canada. Among them is NERC […]

Critical infrastructure is increasingly under attack with major hits on oil pipelines, water treatment facilities and the food and beverage sector all occurring within the last year. Regardless of where the attackers enter from — […]

Threat actors are always on the lookout for pain points — manufacturing systems that can’t afford to go offline, critical infrastructure that can cause disruptions to everyday life or risks to human safety and, unfortunately, […]

The energy market has had rapid increases in demand that cannot be fulfilled with carbon-based fuels. It requires companies to use renewable energies such as solar and wind to keep up. What’s needed is an […]

Cybersecurity in the industrial sector is changing, and the need to look toward the future is ever present, but it is also essential to examine the past and learn from it. Now, threat actors are […]

The manufacturing sector is becoming more interconnected as the Internet of Things (IoT) allows data to be transferred from many devices. IoT device security is critical, and configuring credentials, a process called onboarding, is a […]

Cybersecurity insurance is an increasingly important weapon in the risk management arsenal of today’s enterprises. Unknown just a decade ago, these popular policies now offer organizations a crucial hedge against risks that defy routine assessment, […]

When people think of Rye Brook, New York, an idyllic hamlet in Westchester Country sometimes known as Tree City USA, they don’t generally picture international intrigue. That’s best left to its more cosmopolitan neighbor, Manhattan, […]

Learning Objectives Cybersecurity attacks against manufacturers and other industrial sites are growing every year. When developing a cybersecurity plan, is best to look at it through the lens of business risk reduction and enabling innovation. […]

On May 27, the United States Department of Homeland Security (DHS) announced its initial regulatory response to the Colonial Pipeline ransomware attack. As the Security Directive highlighted, this is only the first step in what is likely […]

Who is responsible for the security of technology and networks? That’s probably information technology (IT). But who is responsible for all the web-enabled, and therefore vulnerable, devices on the plant floor? Unfortunately, that’s still a […]

Ransomware attacks are a growing threat to critical infrastructure and private industry worldwide. While every business sector has felt the sting of ransomware, few have been harder hit of late than health care. In April […]

Connected capabilities offer a great deal of potential for building systems. Connected HVAC, lighting, alarms, fire protection and more are all key components of smart buildings currently in demand. These capabilities offer exciting opportunities for […]

Most cybersecurity frameworks say visibility is essential. Manufacturers need to know exactly which assets are in their environment

The concept and benefits of a software bill of materials (SBOM) are simple to understand. SBOMs are a list of all software in an application or cyber asset. Vendors need to create and maintain an […]

As the pace of cyberattacks on both the public and private sectors has continued to increase, it’s become clear that improved cybersecurity is in the national interest. Since the Biden administration assumed power in January […]

During the second Bush Administration, there was great concern about the rapid progress of the Iranian enrichment program, which would likely lead to the attainment of weapons-grade uranium. The center of that operation was, and […]

Given the proliferation of technology in industrial control systems, it’s high time for OT teams to own their cybersecurity practice

Building automation systems deploy thousands of smart devices across open networks, and the increased connectivity to the worldwide web, combined with unclear system ownership creates a large and vulnerable attack surface. In this article we will […]

A distributed denial of service (DDoS) attack is a malicious attempt to sabotage a network by overwhelming its ability to process legitimate traffic and requests. In turn, this activity denies the victim of a service, […]

Building automation systems have become a soft target for cyberattacks due to the large numbers of intelligent devices connected over open networks, sophisticated threats designed to attack control systems, as well as dependency on third-party […]

Ransomware attacks on the health care industry skyrocketed in the last year as bad actors looked to profit from the chaos brought on by the COVID-19 global pandemic. But health care and ransomware have a […]

The ISA Global Cybersecurity Alliance (ISAGCA), along with admeritia GmbH (admeritia), announced the release of the Top 20 Secure PLC Coding Practices document. The document aims to provide a list of coding practices for programmable […]

What are the top 10 cyber risk manufacturing questions board members should be asking? According to a cyber risk in advanced manufacturing study led by Deloitte’s Center for Industry Insights, nearly half of the executives […]

Building automation systems have become a soft target for cyberattack. This is due to the large number of intelligent devices, open network protocols and increased reliance on third-party vendors and service providers. Automated cybersecurity monitoring […]

IT/OT convergence isn’t just a concept, a catchy mnemonic, nor a convenient abbreviation jumble It’s a very real and significant challenge facing manufacturers. At the crux of the issue is how information technology (IT) and […]

Ransomware may be grabbing the headlines of late, but cyberattacks can hurt companies and communities in places far worse than their wallets. In 2015, details emerged from a cyberattack that caused “massive damage” to a […]

The wave of ransomware attacks on high-profile industrial manufacturers continues apace, as the world’s largest meat processor, JBS, was forced to shut down several plants in the United States earlier this week. JBS USA released […]

Industrial control system (ICS) security is growing in importance as cyber-attacks increasingly focus on physical processes for either ransom or to cause harm to critical production systems. Attacks such as the Oldsmar water treatment plant, […]

Trade disputes are not uncommon in a competitive marketplace, whether they’re between companies or economic superpowers. But in 2014, the U.S. Department of Justice (DOJ) charged five Chinese military hackers with taking their trade war […]

The Colonial Pipeline downtime created by the cybersecurity attack on the operators’ information technology (IT) systems underscores the need for resilient, redundant and responsible processes that enable operations to persist in the face of digital […]

Much of the attention that cybersecurity gets is on the IT or office network side of things, but recently people have begun paying more attention to operational technology (OT) systems that make up our critical […]

To pay or not to pay: It’s an essential and fraught question in regards to ransomware attacks. When multinational aluminum manufacturer Norsk Hydro was hit with a cyberattack in 2019, they chose not to pay […]

How a company responds to an incident is important. The wrong response could damage the company’s reputation or destroy it altogether. A proactive and timely response to an incident can result in great press and […]

The Department of Defense is rolling out the CMMC to help standardize cybersecurity processes for defense contractors and vendors

News that a ransomware attack shut down the pipeline that provides the East Coast with nearly half of its fuel sent shockwaves through the energy and cybersecurity communities earlier this week. Though a cyberattack has […]

Over the weekend, Colonial Pipeline, owner of 5,500 miles of pipeline carrying natural gas, gasoline, and diesel from Texas to New Jersey, shut down its operations in response to what it said was a ransomware […]

The vulnerability of U.S. critical national infrastructure was again thrown into sharp relief when a ransomware attack shut down a pipeline that provides the East Coast with nearly half of its diesel, gasoline and jet […]

A vulnerability is a weakness in a computing resource that can be exploited to cause harm. Mitigating vulnerability risk is accomplished through an effective vulnerability management program that includes vulnerability monitoring, vulnerability risk assessment, and vulnerability mitigation […]

The majority of cybersecurity efforts are focused on preventing outside bad actors from hacking into systems or installing destructive malware – and rightfully so. But there is also a sizable risk from disgruntled employees walking […]

Why are ransomware attacks on the rise versus traditional cyberattacks? Axis Communications’ Wayne Dorris offers his thoughts

Lessons can be learned from prior cybersecurity efforts, even older ones, as this 2007 demonstration showed. Are you aware of the eight ways to mitigate the Aurora vulnerability? In 2007, the Department of Homeland Security, […]

In 2017, auto manufacturer Renault-Nissan became one of many organizations around the world to fall victim to the WannaCry ransomware. While WannaCry was effectively halted within a few days of its discovery, it was one […]

Now that the dust has settled a bit around the cyber attack at the Oldsmar water facility in Florida, and everyone has made their sales pitch, this is a good time to highlight some of […]

A combination of information technology (IT) and operations technology (OT) cybersecurity expertise is required to manage the influx of Industrial Internet of Things (IIoT) devices and increased IT/OT integration.

In 2017, the NotPetya malware was wreaking havoc around the world. Though it likely began as a state-sponsored Russian cyberattack targeting Ukraine, its ramifications quickly spread far and wide, including to multinational corporations like Chicago-based […]

The proliferation of the Internet of Things (IoT) is making buildings more complex and dynamic, with hundreds of devices connecting to disparate systems to perform a wide range of functions like energy management, physical security […]

In 2007, the late Mike Assante blew up a 27-ton diesel generator with 30 lines of code, demonstrating to officials from the Department of Homeland Security the destructive potential of cyberattacks targeting critical infrastructure. Cyberattacks […]

Iran’s Natanz nuclear facility attack underscores the importance of protecting critical OT systems as well as IT systems

Choosing a safety instrumented system (SIS) architecture for defensible operation across the product lifecycle is one of the first decisions an organization must make; know these applicable standards.

The work from home trend is more than just a blip on the radar. What does that mean for industrial manufacturers and cybersecurity

The MITRE ATT&CK for ICS Matrix provides a common nomenclature that allows asset owners, security researchers and consultants, internal defenders and product vendors to better communicate about adversary techniques. Nothing in it is new to […]

Cyberattacks on industrial manufacturing and government facilities have been on the rise, but securing facilities takes more than just a shrewd and effective information technology (IT) department. There also needs to be buy-in from operational […]

When most people think of hackers, they picture grizzled, bearded adults sitting in darkened rooms spotlit by the glow of multiple monitors. Or perhaps hardened foreign operatives covertly working for government agencies. If the movie […]

Cybersecurity: Improving evaluation and certification methods, security audits, and testing provide a foundation for evaluating Industrial Internet of Things (IIoT) devices.

When it comes to industrial cybersecurity, there has long been a partition between the information technology (IT) and operational technology (OT) sides. The IT/OT divide isn’t exactly the Sharks versus the Jets, but it is […]

Organizations have distributed data and workloads across cloud environments and on-premises data centers. As a result, IT teams have to deploy, manage, and secure increasingly complex and hybrid networks. And even though many organizations have moved […]

Multinational brewery and beverage manufacturer Molson Coors was recently hit with a damaging cyberattack, but they’re far from the first adult beverage company to find themselves in hackers’ crosshairs. In August 2020, U.S. spirits and […]

Two leading methods exist for establishing mobile human-machine interface (HMI) connectivity; one providing more cybersecurity. See table comparison of remote access HMI connections.

Another major company has fallen victim to a cyberattack that has caused significant disruptions to its business operations. In an SEC filing, Chicago-based brewing and beverage company Molson Coors recently acknowledged they experienced a systems […]

The world we live in is not the same world we once knew. Unprecedented global events and new technological advances are forcing manufacturers to adapt and work in an ever-evolving, more remote business environment. Change […]

Cyberattacks in manufacturing are on the rise. So how should the industry respond to this increasing threat? It takes organization, buy-in and cybersecurity maturity. Awareness of the need for cybersecurity has been growing, as attacks […]

Mission Secure, an industrial control system (ICS) cybersecurity technology company, appointed John Adams as Chief Executive Officer (CEO). He will succeed David Drescher, who will remain with the board of directors. “A generational shift has […]

Most people would assume having security cameras at a facility provides peace of mind and offers additional protection. However, when everything from televisions to security cameras are connected to networks, they also can open up […]

This case study documents a cyber journey and cyberrisk mitigation strategy implemented on operational technology systems in the HDR office building

Manufacturing cybersecurity is less well known but can pose even greater financial, operational and safety risks than information technology (IT) security. The impact can be catastrophic – from disruptions to manufacturing lines, to power outages, […]

Anyone watching the news can see that cybersecurity management is becoming increasingly relevant for industrial companies. Recent analysis performed by insurance carriers indicates that the incidence of cyberattacks faced by manufacturing companies is 30 times […]

Industrial automation cybersecurity has a lot of confusion and questions. Learn about changing trends and effective best practices for operations technology (OT) providers.

The Industrial Internet of Things (IIoT) will have the strongest impact on operational technology/industrial control system (OT/ICS) cybersecurity.

The Cost of Insider Threats Report by IBM indicated the overall damage by negligent or malicious employees totaled $11.45 million. Whereas intentional insider criminals cause only 14% of the accidents, their damage adds up to […]

Cybersecurity is a relatively recent top concern for industrial enterprises. A number of high-profile security incidents like the hacking of a Florida water treatment plant, have brought the topic into public scrutiny, but the issue […]

Having comprehensive list of security-related patches by using operational technology (OT)-specific patching tools to gather complete software, vulnerability, and security patching information sounds simple. Information technology (IT) security professionals will tell users to scan it […]

IoT and intelligent management systems have revolutionized the capabilities of our buildings by enabling better automation and increasing efficiencies for better overall building health

Most operational technology (OT) environments use scan-based patching tools, which are pretty standard but not overly insightful to show us what assets we have and how they are configured. What is really needed is robust […]

The COVID-19 pandemic is forcing companies to adjust their business practices and settle to a new normal. See four tips on how edge computing and the Industrial Internet of Things (IIoT) can help companies adjust.

For a robot to be safe, it must also be secure from cyberattacks in the age of Industrie 4.0 and the Industrial Internet of Things (IIoT). Everyone in the information technology (IT) and operations technology (OT) departments are responsible for ensuring this happens.

Hot on the heels of the high-profile SolarWinds attack comes the Oldsmar water treatment facility attack. This one is more targeted and focused on a specific – and very critical – piece of infrastructure. A […]

Cybersecurity education: Human hacking, the compromise of human assets, is often the first step in a cybersecurity breach, even if or when technical systems are secure. Help coworkers and those in your supply chain to avoid being the entry point for attack. Learn attack methods, five attack types and five prevention techniques.

What does OSHA teach us about industrial cybersecurity? Clearly, high cybersecurity risk could increase risk of industrial accidents, but OSHA’s model can help in other ways. Prior to 1970, worker safety in industrial settings was […]

Protecting programmable logic controllers (PLC) and programmable automation controllers (PAC) from security threats should begin even before an attack is detected.

Learning Objectives Cybersecurity global standards from IEC, ISA Global Cybersecurity Alliance and UL help lower risk. Cybersecurity education and training. The Industrial Internet of Things (IIoT), connected devices and the vast amounts of generated data create industrial […]

Deployments and optimal operation of industrial wireless local area networks (LANs) require attention to site survey, lifecycle management, cybersecurity and collaboration. Need to optimize existing industrial wireless networks?

When information and operational technology collaborate with business leaders, facility managers gain secure access to the data they need to achieve their sustainability goals

Learn the basic concepts and strategic planning needed to ensure resilient design of hospitals and health care facilities to reduce risk during natural disasters and man-made threats

Cybersecurity is an important aspect of project implementation, and will become critical as information and operations technologies converge.

What is a smart building, and how can engineers design integrated building systems?

Using mobile devices on the plant floor offers many potential benefits, but the right approach is a must because of safety and cybersecurity concerns.

Digital representations of factories and industrial spaces lead to opportunities.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.