Learning Objectives
- Industrial wireless site surveys can change over time and may need revisiting.
- Consider cybersecurity of industrial wireless networks.
- Collaboration of IT/OT teams helps with industrial wireless reliability.
Since the IEEE 802.11 “Wi-Fi” standard debuted in 1997, most modern industrial enterprises today have some, if not most, of their operations running over industrial wireless LANs (iWLANs). In effect, these are the communications backbones of Industry 4.0 production and logistic models and the Industrial Internet of Things (IIoT) concepts and technologies they employ.
(Haven’t set up industrial wireless, yet? See this August Control Engineering article: “What industrial wireless network should I use?”)
Unlike Wi-Fi for home, office, and public spaces, iWLAN applications have loftier performance requirements, which may include low-latency, deterministic, ultra-reliable, highly secure, and/or accommodate complex radio frequency (RF) environments. After all, production output, damage to machinery or equipment, and even environment, health, and safety (EHS) concerns may be at stake. If an application involves roaming vehicles or robots (see related articles in this issue), the iWLAN’s complexity is much greater.
All of that’s a tall order, which is why iWLANs require a clear understanding of an application’s requirements and then careful RF engineering to meet those requirements.
Four best practices for iWLAN use
Although entire books are available on the RF engineering needed for proper iWLAN deployments, these four best practices can provide industrial enterprises with a broad framework to ensure they get the most out of iWLAN investments over time.
1. Site survey for industrial wireless
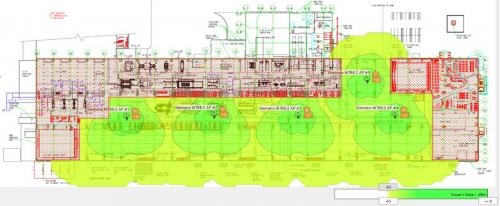
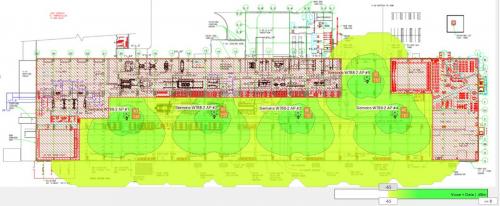
Industrial environments typically have diverse sources of RF interference, reflections, and absorption that can cause varying degrees of attenuation and irregular radio-wave patterns. Among them: Nearby office WLANs, adjacent iWLANs, and RFID systems; metal machinery, ductwork, racks and doors; and thick concrete walls, liquids and even people. That’s why a thorough site survey is critical for successfully deploying and operating an iWLAN.
A site survey’s goal is to ensure adequate signal coverage for the target facility and application via the optimal placement of wireless access points (APs), correct channel selections and the best signal-to-noise ratios (SNRs) possible between APs and client devices.
To conduct a site survey, you’ll need the facility’s floor plan, the application’s data-rate requirements, and tools to measure SNR and detect other RF sources, such as wireless site survey software and an RF spectrum analyzer. If these tools are not available, experts with professional software and extensive site survey experience are available to assist in this stage of iWLAN design.
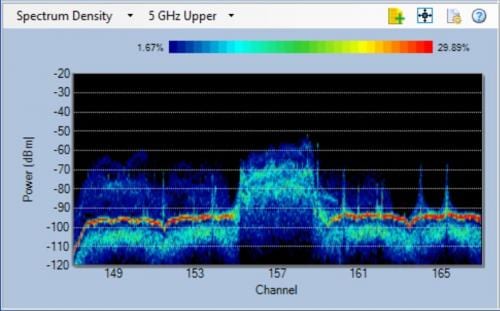
Next is a visual inspection of the facility to validate the floor plan because significant modifications may have been made to the original structure and note any possible attenuation sources that may be free-standing, such as inventory or equipment racks, machinery and stock. A spectrum analysis also should be performed with appropriate tools.
At this point, preliminary AP locations can be determined, outfitted, and tested. Elevated locations, such as building columns (indoor) or posts (outdoor), rafters, and ceilings, are ideal. AP devices with multiple and omni-directional antennas can provide optimal RF coverage and are best connected with POE (power-over-Ethernet) cabling.
Initially, in configuring APs and client devices, just get them “talking” to each other. They should be placed so their radio waves create cells of coverage that lightly overlap to ensure no signal gaps or channel overlaps.
After a radio connection is established, enable higher-level features, such as security and roaming capabilities, one at a time, so each can be troubleshooted, if needed, as they’re added. Same goes for tweaking connections, such as adjusting transmit power or roaming strategies. And don’t forget to document everything.
2. Lifecycle management for industrial wireless networks
Properly designing, engineering and configuring an iWLAN can be quite an undertaking. It often requires outside RF engineering expertise if not available inhouse. While it’s possible to set one up correctly using a do-it-yourself, learn-as-you-go approach, doing so can consume a lot of skilled information technology/operational technology (IT/OT) resources that might be needed elsewhere in the industrial enterprise and take much more time and effort than hiring experts for a short-term engagement.
Either way, once an iWLAN is up and working as planned, the tendency to “set-and-forget” wireless network operation can be a mistake. Like any piece of production machinery, the iWLAN becomes a valuable plant asset that needs to be managed over its lifecycle.
It’s a good idea to review the site survey, too. Why? Because over time, a facility’s floor layout can change substantially. For example, if a new machine or a metal rack is installed, or even a wall or partition, it can change the production environment’s RF characteristics, either a little or a lot. If it’s a lot, the iWLAN could stop working altogether. If it’s only a little, the iWLAN’s performance could be running sub-optimally and increase the risk of communication faults, leading to downtime or other costs.
As part of the periodic site survey, an updated spectrum analysis should be performed as well. New internal systems or even neighboring buildings will be commissioned with Wi-Fi. These new systems which were not present in the original spectral analysis, may intrude on or increase the density of the wireless spectrum to the detriment of the existing wireless solutions. It’s worth remembering a spectrum analysis is only a snapshot in time, and therefore should be routinely monitored. If a new spectrum analysis reveals significant changes that affect the existing wireless systems, adjustments should be made (either to the new systems or existing systems) so all systems can co-exist and run optimally.
In addition to changes in floor layouts, available iWLAN and wireless technologies will inevitably evolve over time, just as IEEE 802.11 has evolved, and now 5G wireless is emerging. Plants using older Wi-Fi technology could be incurring opportunity costs, as newer wireless technologies can provide more capabilities, often at less cost.
3. Cybersecurity for industrial wireless
Industrial enterprises – especially critical infrastructure, such as power plants, oil and gas operations, transportation and others – are big targets for cyber threats. Consider ransomware. It can encrypt the code or data needed to operate machinery or a process and demand a payment to unencrypt it. More and more, its perpetrators are targeting big industrial operations because the payouts can be much larger than individuals or small-to-medium size businesses.
The good news is iWLAN hardware comes with built-in security features, such as firewalls, encryption, and device authentication. Add-on hardware can provide virtual private network (VPN) capabilities. In some components, these features will need to be configured in deployment, a step that can be overlooked and leave the iWLAN vulnerable to intrusion.
Other suggestions for iWLAN cybersecurity include:
- Restrict physical and virtual access. Servers, routers, APs (if not elevated and out of reach) and client devices should be caged and locked to prevent tampering. Each device connected to an iWLAN will have a media access control (MAC) address, access to which can and should be restricted.
- Hide the iWLAN’s SSID. All Wi-Fi routers have a service set identifier (SSID) that is typically broadcast, but this broadcast can be disabled, making it hard for hackers to find the network.
- Use authentication and the strongest encryption available. Wi-Fi protected access (WPA) and WPA2 authentication should be done with a pre-shared key or a radius server. Clients should be required to authenticate with a key phrase and also require an encryption method to be specified, which is more secure than open authentication or weak methods such as WEP. Strong encryption ciphers such as TKIP or AES also should be used.
- Segment and separate OT iWLANs from IT WLANs. On the OT side of an industrial enterprise, it’s good to segment the OT iWLAN into subnets, so if a hacker gets into one part of the iWLAN, the rest is safe from possible exploitation. Also, keeping the OT iWLAN separate from the IT WLAN can prevent intrusions from the latter into the former.
4. IT/OT collaboration.
To prosper in the Industry 4.0 era, industrial enterprises need a deep, cross-functional, and proactive collaboration between OT and IT teams that combines their respective know-how and experience to make today’s production and logistics environments fully digital. iWLANs are a perfect example. IT/OT teams need to understand the unique terminology and design requirements for all network environments, especially in context of the network as the strategic backbone of a fully digital industrial enterprise.
Years ago, OT’s control and SCADA systems networks were typically isolated physically from enterprise IT networks. But with the emerging Industry 4.0 and IIoT models, that gap has closed, especially as iWLANs have been deployed. Unfortunately, in many cases, connecting OT and IT networks created a gap in understanding between OT and IT teams, given each other’s different backgrounds and perspectives.
For example, the OT networks’ physical isolation from external intrusions may have left OT engineers unconcerned with cybersecurity, but now they must be. On the other hand, IT professionals may not have worried about how their enterprise WLANs (initially deployed for providing general Wi-Fi coverage) may have oversaturated the wireless spectrum and available channels. This unfavorably affects OT operations which depend on the reliability and uptime of their iWLANs.
What can be helpful in bridging the IT/OT understanding gap is to conduct an initial, facilitated workshop that brings both groups together to share their respective backgrounds and concerns relative to their particular responsibilities. This activity can include whiteboard exercises to identify specific opportunities for greater collaboration, such as joint wireless spectrum oversight of industrial networks and operations, and work out relevant action plans. A best practice in this area would then be to conduct periodic IT/OT team meetings at least semiannually, if not quarterly.
Improve reliability of existing industrial WLANs
Are your iWLANs operating as they should? These days, iWLANs are essential parts of the communication backbones for most Industry 4.0 enterprises. However, many may be operating in “set-and-forget” mode with outdated IEEE 802.11 technologies. Or perhaps their security features are less than ideal today and are creating vulnerabilities that should be identified and closed. Also, are your OT and IT teams working together to ensure your iWLANs are assets that are adequately segmented and operating in tip-top shape?
If any of these conditions describe your iWLAN environments, it may be time to refresh your existing site survey or conduct a new one altogether. It’s important to apply the lifecycle management practices to iWLANs same as you would with expensive, indispensable machinery.
Richard Kluth is network solutions consultant at Siemens Industry. Edited by Mark T. Hoske, content manager, Control Engineering, CFE Media and Technology, mhoske@cfemedia.com
KEYWORDS: Industrial wireless, wireless reliability
Industrial wireless site surveys can change over time and may need revisiting.
Consider cybersecurity of industrial wireless networks.
Collaboration of IT/OT teams helps with industrial wireless reliability.
CONSIDER THIS
Time to revisit wireless reliability is before there’s an outage. The attenuation map can change over time.
RELATED ARTICLES
Five home office network risks for businesses
https://www.industrialcybersecuritypulse.com/five-home-office-networ2k-risks-for-businesses/
Remote teams struggling to mitigate cybersecurity risks
https://www.industrialcybersecuritypulse.com/remote-teams-struggling-to-mitigate-cybersecurity-risks/
New ways to attack Industry 4.0
https://www.industrialcybersecuritypulse.com/new-ways-to-attack-industry-4-0/
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.