When an organization does not take advantage of potential synergies between information technology (IT) and operational technology (OT), it might be leaving plant floor systems open to attack. In many organizations, the lines of communication between these two groups are often nonexistent or strained, with each side ignoring the other or believing they are an obstacle to work around. Bridging this gap can improve performance on the floor and reduce risks to operations. A systems integrator is a natural facilitator to help make that happen (see Figure 1).
IT/OT disconnect
This disconnect between IT and OT can arise for multiple reasons: lack of communication, lack of trust between members of the two groups or even a feeling of turf protection. Other factors that create further separation are different technology maturities, technical skill gaps and the use of different toolsets and hardware. A few examples where disconnects between IT and OT organizations can occur include:
- Response time and uptime requirements for systems in their respective areas
- Networking design and infrastructure design challenges
- Patch and antivirus management of server and client operating systems
- Identification and management of cybersecurity risks.
At the heart of IT/OT convergence is the recognition of the connected computing nature of OT devices and how the unique characteristics of OT systems require solutions that may differ from those appropriate in the IT space. At the same time, the solutions chosen must address all the cybersecurity concerns IT groups have been addressing.

Operating on bad assumptions about what will work in the OT environment based on IT experience could lead to production or even safety risks. For example, an IT policy that requires screen lockout after a period of inactivity could impede an OT operator’s ability to respond to an upset and will likely be ignored. In this example, physical security may be the better solution. It is likely an organization’s IT experts have tools, techniques and knowledge that could improve operations if they can understand the OT environment and its challenges.
The system integrator lives in both camps. They can speak the language, make the introductions, find or be the go-between and facilitate co-participation in several activities to build trust and educate the participants. In short, they know how to shrink the gap between IT and OT. One way is by working together on activities that require input from both teams, fostering a mutual understanding between IT and OT (see Figure 2).

Potential activities that can be used to facilitate trust and knowledge include:
Development of requirements: These efforts can focus on the design of an OT network, the definition of IT/OT interface or the development of cybersecurity requirements for control systems. Discussions about risk and how it drives requirements for backups, network segmentation, workstation hardening, change control, documentation and auditing can raise the level of awareness and understanding for all participants. System integrators live in this world — they can explain to IT why patching can be difficult or help OT understand how (and why) to harden a workstation rather than rely on an air gap. It may be best to sit down with IT and OT and discuss these topics, ensuring each group understands the requirements and pressures the other faces. We have led a session like this at a major food manufacturer where IT wanted to move a critical manufacturing server to a remote data center and considered four-hour response time to be very good. This was not acceptable to the production supervisor.

One thing can lead to another: Setup and maintenance of servers is an area where IT and OT teams can help each other. The knowledge, techniques and tools of the IT team can help ensure systems are secure and set up according to best practices. Recently, at a refinery, we encouraged a controls manager to open conversations up with the local IT manager about setting up a Windows Server to ensure it was hardened and secure within the context of the overall network. With that effort complete, the controls manager realized IT also could help harden the plant floor workstations and host a backup solution for disaster recovery.
Network and infrastructure design: The plant network creates natural touch points between IT and OT groups and is another area where these teams and personnel should and need to work together (see Figure 3). This is obvious when looking at shared infrastructure such as firewalls and interconnections between networks. It may be less obvious when designing remote access techniques, authentication methods and strategies for encryption among other topics. These are areas where technology more familiar to IT teams can be used to improve the security and resiliency of OT systems and assets. Recently, at a cogeneration plant, the operations team was seeking to replace an existing balance of plant (BOP) plant floor network with a modern solution. A suitable programmable logic controller (PLC) original equipment manufacturer (OEM) ring topology was designed by the integrator, but only reusing a single existing upstream connection. Bringing IT into the process allowed them to suggest a design using existing virtual local area networks (VLANs) and resilient paths to two separate areas that integrated into their own resiliency architecture. In this case, successful collaboration between the teams brought the design above the original requirements.
Response planning: Incident response is a great area for discussion about shared responsibilities and planning, especially with the recent examples of ransomware shutting down operations. Even if the ransomware does not impact the operations networks, there may be actions that need to be taken to isolate the operations networks or even shut them down. The response to an incident is likely to be an “all-hands-on-deck” event, so planning the roles, responsibilities and potential actions in advance as a shared team can be a great way for all participants to understand how their part impacts the whole. We are doing this with a large steel manufacturer, bringing IT and OT experts together to improve the incident response and disaster recovery response to a potential ransomware attack.
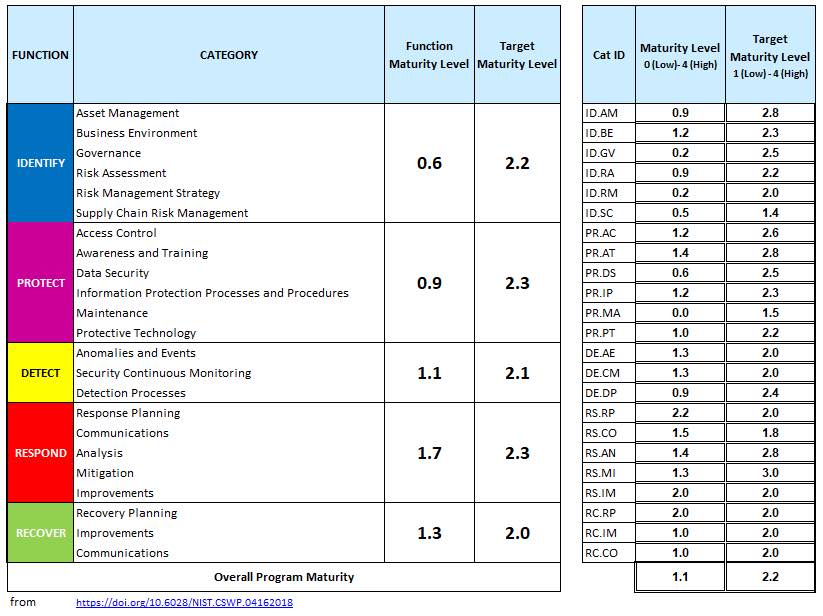
Risk assessment: Most in the OT space are starting to recognize control systems are no longer off-the-grid from threats such as malicious programs and unauthorized access. When assessing OT cyber maturity, it is useful to involve IT for several reasons. IT organizations often have more experience with tools such as NISTs Cybersecurity Framework and can help in adapting those tools to the OT space while keeping criteria and basis for risk tolerance consistent between groups (see Figure 4). When comparing and presenting assessment results to executives, companies want to make sure the discussion stays focused on what areas need improvement. Finally, having IT and OT resources assess each other’s scope should result in significant learning for both groups. Nothing could be more confusing to senior executives than presenting two assessments that look nothing alike in terms of results yet represent the same company.
Cybersecurity testing: Perhaps the best way to help integrate these teams is during acceptance testing of the control systems, especially the testing of the cybersecurity requirements. This activity should give the IT team a chance to review what those requirements are and how to test them using tools they may be very familiar with — Wireshark, Nessus or even the discovery and penetration tools they choose to bring, which may be new or unfamiliar to those on the OT side.
Looking ahead
These represent some of the opportunities for tasks and projects that will help facilitate understanding between the IT and OT organizations. There is so much knowledge each of these groups could take from each other and if they are working together, the solutions they can deliver will lead to more productivity and better security for critical systems. A system integrator is a key resource for helping bridge the gap and provide a space that allows the two groups to develop a long-term relationship.
Applied Control Engineering is a member of the Control System Integrators Association (CSIA).
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








