With increasing attacks on critical infrastructure networks that have become more frequent and consequential, more effective operational cyber solutions are required that aggregate, analyze, and correlate various sources of data and across multiple platforms into a near-real time visualization that depicts potential threats. Organizations must look beyond their own perimeters to collaborate and assess the impact of a cyber attack on corporate partners, suppliers and vendors. With complex systems of interacting devices, networks, organizations and people to facilitate the productive sharing of information, this capability is becoming as much a benefit as a threat.
With the U.S. Environmental Protection Agency (EPA) leading the water sector’s critical infrastructure protection activities, utilities have had to transition from focusing mostly on physical security to including cybersecurity.
Government reports confirm the water and wastewater sector faces threats from foreign governments’ multi-stage intrusion campaigns and individual criminal organizations looking to threaten the security of these operational systems and related data. Managing industrial control system (ICS) cybersecurity is already a complex endeavor. It requires an interdisciplinary, risk-based approach, involving an organization’s leaders, engineers and legal teams. Segmentation and design will be critical as some organizations increase Industrial Internet of Things (IIoT) implementations.
Cybersecurity policies
Organizations should have policies and procedures that address environments for operational technology (OT) and information technology (IT). There should be alignment between those processes and how they are governed so they don’t operate in silos.
The largest risk to cybersecurity compliance starts with the internal staff, which is followed by not having clearly defined routes for escalation when a breach occurs. Other risks include a lack of strict adherence to change management processes and a lack of enforcement for access control procedures.
Continuous culture change strategies and awareness training of employees and executive management needs to be sustained to mitigate these risks.
The ICS culture has focused on major risk consequences including major failure of industrial systems that can lead to loss of life. The focus will continue to be maintaining the system’s reliability to avoid facility downtime and control system changes. Anything that can compromise reliability or safety or the efficiency and effectiveness of these operational systems is a greater factor in their overall deployment.
By implementing a new governance model that enables collaboration among key groups inside the organization, such as IT, engineering, operations, ICS and security, will allow the industry to raise awareness of the need for standardized risk management approaches for sourcing, procurement and vendor management.
Ongoing challenges include determining how best to mitigate risks with capital projects that include scopes that makes changes to the control system, suppliers providing on-site support with their external laptops, and purchasing of equipment that may need to meet new industry compliance requirements. Addressing these and other concerns, such as how far into the supply chain should reach extend – third tier suppliers (integrated circuits, digital storage), second tier suppliers (meters, sensors, software) or just first tier suppliers (major systems, communication systems, integration)?
Strengthening cybersecurity
No longer are network intrusion detection; firewalls; patch management; security, information, event and management (SIEM) software; and antivirus components sufficient as security measures for an organization to put in place. Awareness and machine state learning are needed.
Threat intelligence
These are challenging times for security managers, with corporate boards demanding awareness of cyber risks, faster processing of complex data and efficient managed services for an increasing number of intelligent devices. Security teams are in a better position of strength to defend their organizations against threats if they know what is coming in their directions. Tools and staff are vital, but they should be augmented with intelligence.
Risk and compliance
With new market opportunities, continuous economic challenges, regulatory requirements and an increased burden to improve risk management effectiveness, many organizations are recognizing the need to transform their internal audit and risk management functions. Organizations are exposed to greater compliance risk than ever. By leveraging this platform into the risk management auditing strategy, stakeholders have the ability to assess and achieve compliance.
Compliance programs are critical for monitoring and assuring that an organization can verify that business processes reflect documented policies and procedures. This provides objective insight and improves efficiency by driving frequent review of processes, evaluate risks and ensures compliance.
Cyber situational awareness
Continuous monitoring of the operational system data traffic by collecting real-time data will allow detection of unfamiliar activity through a machine learning, modeling ability. This provides owners and cybersecurity auditors detection capabilities and visibility regardless if it’s a cyber attack, an operational malfunction or incident. Big Data applications also can capture and analyze each packet of information flowing through the network in real time.
Packet protocol layers can be broken down to ascertain the destinations and details of every packet. By analyzing every packet, normal traffic patterns can be developed, giving detection of any potential deviations a greater probability of occurrence.
However, there are security challenges with Big Data environments. Mitigation includes security solutions that can keep up with the continuous evolution of non-relational databases, security measures for automated data transfers. This helps ensure a high occurrence of data validation for trust, origin and accuracy, measures against unethical behaviors related to data mining, access control encryption, and having a detailed audit process that can manage the enormous amount of data.

Organizations need to revise and update existing documents, how they perform vulnerability assessments and adjust security posture by including IIoT devices, data, and platforms. Solutions need to improve the combination of intrusion detection and mitigation techniques to protect against known and unknown attacks without relying on updates or patches. Poorly configured firewalls, improper network segmentation and vendor supply chain security need to be addressed before reworking an environment for IIoT upgrades.
Designing and maintaining the integrity of the IIoT system requires thorough understanding of the communications standards used among various IIoT components to maintain safe and efficient operations. In this cyber-physical layer, it can be difficult to spot communications errors, cybersecurity threats, and poor network health problems. Obvious symptoms include sluggish visualization updates, unexplained device failures, and failures of IIoT components.
A robust and healthy IIoT network is key to preventing these failures. Developing secure end-to-end IIoT solutions require a holistic approach that involves various levels of applications and combines critical security features across the device, communications, cloud and lifecycle layers (policy enforcement, regular auditing and vendor control).
Cybersecurity attack vectors
All facets of the cybersecurity industry must work together to improve end customers’ cybersecurity processes. The industry needs to understand how resources and organizational structure grow over time to result in a stronger security posture. The industrial sector acknowledges a lot still needs to be done with standards, collaboration and awareness.
Typical IIoT infrastructure vectors include:
- Physical attack on the device,
- Attacking through the network, server or through a cloud architecture.
IIoT system configuration consists of the:
- IIoT device: Part of a system in which devices talk to related devices to communicate usable data
- The gateway: Serves as the connection point between device and utilized platform. Gateway provides a place to preprocess the data locally at the edge before sending it to the cloud or on-premise platform. When data is aggregated, summarized and analyzed at the edge, it reduces the amount of data that needs to be transmitted. Gateways can also be a protection point by having features such as tamper detection, encryption, hardware random generators and crypto engines.
- Network: Continuous monitoring of network status via software is simple and should be configured to self-optimize.
- Server or cloud: Use digital certificates when accessing cloud services as the use an asymmetric, encryption based, authentication system based to authenticate a transaction and encrypt the channel from device to cloud before authentication.
With the IIoT attack surface so large and inclusive of various operating systems, development languages and network protocols, standardization and recommended architectures are likely to be developed that are aligned with the supervisory control and data acquisiton (SCADA) systems. Improving the evaluation and certification methods, security audits and testing would lay the foundation for a unified standard to evaluate IIoT devices.
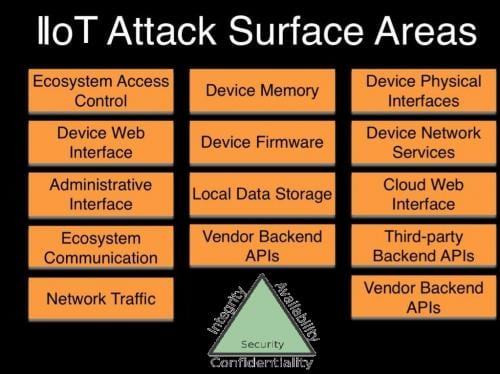
To facilitate IIoT platform security, end users and large original equipment manufacturers (OEMs) will adopt accepted communication protocols and security standards, require approved and validated libraries or internally build them, provide continuous software updates and be part of an end user’s security strategy.
OT and IT security collaboration
How do you prioritize, transmit and merge IIoT security threats with other OT and IT security threats to respond to and mitigate risks with device-layer and communication-layer devices? Both have several questions worth considering.
Device-layer considerations include:
- Do equipment vendors provide rootkit malware protection?
- Is the device vulnerable during installation?
- Are devices regularly tested for malicious rootkits?
- Does the IIoT architecture enable remote firmware testing?
Communication-layer considerations include:
- Which data elements need encryption and to what level?
- Does the organization have the correct culture to address IIoT security risks?
- Can you patch devices remotely?
- Does the IIoT architecture limit the damage of unauthorized intrusions?
- Can third-party testing play a role?
- How to protect against “edge” vulnerabilities.
Apply additional site or industry-specific questions to these lists.
Anil Gosine is a global program manager at MG Strategy+, a CFE Media content partner. Edited by Mark T. Hoske, content manager, Control Engineering, CFE Media, mhoske@cfemedia.com.
KEYWORDS: Cybersecurity, utilities, IIoT
Cybersecurity at utilities and other areas needs to improve as Industrial Internet of Things (IIoT) expands.
Stronger cybersecurity also means attention to threat intelligence, risk and compliance.
OT and IT collaboration can help cybersecurity.
Consider this
Have you revised and updated cybersecurity policies, procedures and how vulnerability assessments are performed in context of IIoT?
See additional IT/OT stories including:Mitigating OT cybersecurity risks, enforcing best practices
Mitigating OT cybersecurity risks, enforcing best practices
Five steps to improve OT, ICS cybersecurity awareness in manufacturing
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








