The FBI’s Internet Crime Complaint Center (IC3) has released their 2021 Internet Crime Report. A key focus of the Internet Crime Report is on ransomware. Ransomware is a form of malware that encrypts data on a computer, making it unusable unless a ransom is paid. If the ransom is not paid, the victim’s data remains unavailable. In 2021, the IC3 received over 3,700 ransomware complaints.
In June 2021, the IC3 began tracking ransomware incidents from members of the 16 critical infrastructure sectors. The report defines critical infrastructure as a sector whose “assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on our security, national economy, public health or safety, or any combination thereof.”
In 2021, the IC3 received 649 complaints that indicated organizations belonging to a critical infrastructure sector were victims of a ransomware attack. Fourteen of the 16 critical infrastructure sectors reported at least one member that was a target of a ransomware attack. The report states that, “Of the known ransomware variants reported to IC3, the three top variants that victimized a member of a critical infrastructure sector were CONTI, LockBit and REvil/Sodinokibi.”
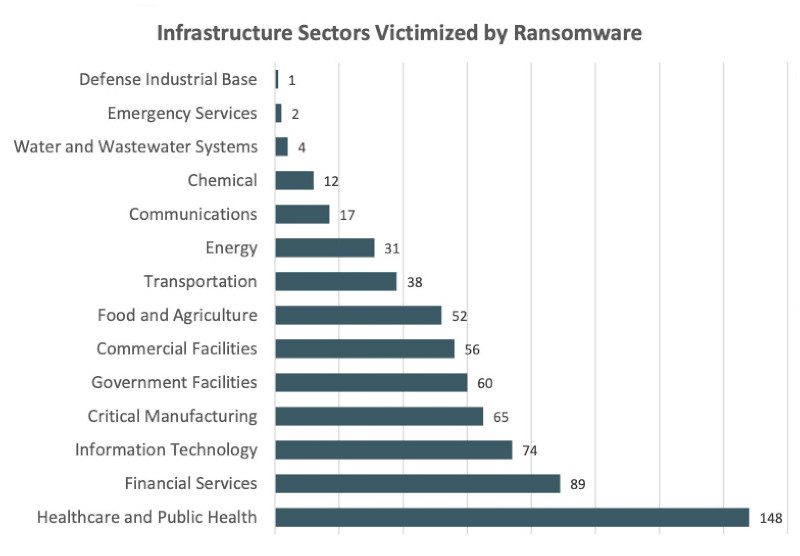
The IC3 expects an increase in critical infrastructure victimization in 2022.
To prevent a successful ransomware attack, the FBI recommends that organizations take four steps:
- Update operating systems and software
- Implement user training and phishing exercises to raise awareness
- Secure and monitor Remote Desktop Protocol (RDP)
- Make an offline backup of your data
A caveat to the first suggestion: Because updating every piece of software isn’t always feasible in OT environments, the recommendation is to implement a more holistic vulnerability management approach which patches those critical assets that can be patched, but also creates detailed risk mitigation plans for high-risk assets that are unpatchable.
Not only back up data offline, but also create and test a response and recovery plan. After testing the plan, use that information to determine whether enough data was backed up, have the right points in time available for a recovery, whether the communication plan was effective and how long it took to recover from the simulated ransomware attack.
NIST’s Profile for Ransomware Risk Management is a useful resource with plenty of tips on preparing and protecting yourself from a ransomware attack.
-This originally appeared on Industrial Defender’s website. Industrial Defender is a CFE Media content partner.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








