
Artificial Intelligence in Cybersecurity: Video Series, Lesley Carhart, Dragos
Recently, Industrial Cybersecurity Pulse sat down with Lesley Carhart to discuss the proliferation of AI in cybersecurity.
Home | IIoT & Cloud | View All

Recently, Industrial Cybersecurity Pulse sat down with Lesley Carhart to discuss the proliferation of AI in cybersecurity.

While cloud and on-prem infrastructure deployments differ greatly, many cloud attacks are similar to traditional on-prem attacks.

The Securing the IIoT eBook includes stories on how to mitigate cloud security threat and accelerating smart manufacturing.

OPSWAT’s web application security report highlights the disparity between infrastructure upgrades, spending and security improvements.

Sung Kim of iBase-t talked with ICSP about how to protect MES from threat actors and what role zero trust plays in it.

There have been plenty of industry discussions around the need for IT/OT convergence. This is crucial to industry 4.0.

AT&T Cybersecurity released their 2023 Edge Ecosystem report about changes within the edge space and how it’s impacting industry sectors.

An airport in Bristol, England, incurred a ransomware attack, showing the vulnerabilities in the transportation sector.

Road testing to improve self-driving security is expensive and time-consuming, but CCI researchers developed a virtual option.

With industry 4.0, factories are becoming more connected. However, more connections in smart factories also mean more cyber risks.
ICS/OT manufacturing ecosystems were considered safe because they were closed-loop systems. Manufacturers realize that they’re vulnerable.

What caught our readers’ attention in 2022? Here are the top 10 Industrial Cybersecurity Pulse articles or the past year.
In this webcast, Matt Ziegler will discuss why it is important to understand what assets are on your XIoT network and how you can do so.

Gary Kneeland of Claroty discussed “Industrial Networks and the Extended Internet of Things (XIoT)” at Rockwell’s Automation Fair.

The Internet of Things (IoT) was evolving as a concept even before it was defined, with household objects quietly sprouting the ability to connect to the internet. Many of these devices have enriched lives to […]

Insider attacks on industrial and manufacturing targets are escalating. Where are these attacks coming from, and why are they on the rise?

Federated learning is a collaborative method for training a machine-learning model that keeps sensitive user data private.

IIoT connects the edge devices in OT networks directly to the Internet to enhance operational efficiencies.

With billions of connected devices, there’s need for a strong global baseline for IoT security in consumer products.

Recently, we have developed a higher level of digital dependence, which has called for an increase in cyber resilience.

Power companies, chemical plants, hospitals and critical infrastructure rely on cloud-based services to monitor and control vital processes. This means cloud-managed facilities and industrial control systems (ICS) face omnipresent threats. Rapidly advancing technology, changing work […]
Edge computing makes it possible to process data closer to where it was created, but as it becomes more prevalent, it’s having a major impact on communications, especially when it comes to Industrial Internet of Things (IIoT) security.
How can you address cybersecurity threats on the edge and develop the best edge security strategy for your organization

Securing operational technology (OT) networks requires a great deal of thought when designing and implementing security. Industrial networks contain a complex mix of specialized protocols and devices, including proprietary protocols developed for specific families of […]

According to Gartner, by 2025 cyberattackers will be able to weaponize operational technology (OT) environments to harm or kill humans, but this timeline is accelerating quickly. How might this happen? An example of this kind […]

A new and more reliable method to defend vulnerable data on the stack, a major memory region responsible for storing computer program data for processes, has been developed by an international Penn State-led team. Such […]

Whether you’re still adjusting to the work-from-home revolution brought on by COVID-19, looking to build a remote team to make better use of the talent pool, or just thinking of updating your accounting software, cloud […]

As we head into the Industry 4.0 era — where connected Internet of Things (IoT) devices and automation will reshape industries — our world is already highly connected. According to Statista, there are more than […]

Engineering researchers have developed a new approach for implementing ransomware detection techniques, allowing them to detect a broad range of ransomware far more quickly than previous systems. Ransomware is a type of malware. When a […]

Whether you’re still adjusting to the work-from-home revolution brought on by COVID-19, looking to build a remote team to make better use of the talent pool or thinking of updating accounting software, cloud accounting tools […]
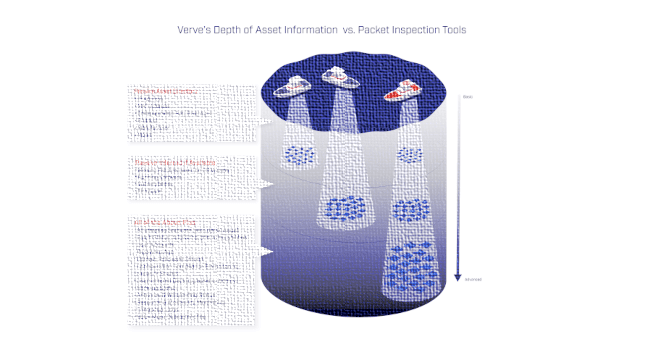
Patch management in an operational technology (OT)/industrial control system (ICS) setting is full of challenges. From proprietary hardware and software to a lack of staff, inadequate or non-existent testing equipment, and regulatory reporting and system […]

Last year brought some of the most significant cyberattacks in history – from the Kaseya supply chain ransomware attack to cyber-criminals attempting to poison the water supply in Florida, to the already infamous Log4Shell vulnerability. […]

Manufacturers are under pressure to provide remote access and real-time data streams, while hoping keeping their facilities secure. While many have jumped in with reckless abandon, those manufacturers slower to adopt should learn from the […]

As we think about Industrial Internet of Things (IIoT) attacks, we break them down into three broad categories. The first is what we refer to as collateral damage. The best example of this is the […]

Not long ago, a major water utilities firm in the UK revealed plans to move a significant part of their supervisory control and data acquisition (SCADA) system to the cloud. This is one of the […]

Many people nowadays work in industries that largely rely on cloud computing to stay on top of their daily tasks. Moreover, the system allows people to seamlessly integrate as many employees as needed into any […]

As manufacturers continue to adopt Industry 4.0 and IIoT technology, cybersecurity is becoming more and more critical with each passing day. Successfully protecting a network requires not only constant vigilance but strategies for securing an […]

Attackers are increasingly gaining footholds into corporate environments to conduct ransomware or data theft operations via Internet-connected smart devices. Whether they be printers, lockers, aquariums or conference rooms, these seemingly innocuous access points to corporate […]

As the Industrial Internet of Things (IIoT) and other data-centric concepts are realized in businesses and on factory floors all over the world, the practice of aligning operational technology (OT) and information technology (IT) is […]

Since the start of the COVID-19 pandemic, the pace of digital transformation has accelerated tremendously. Meanwhile, companies have also become increasingly aware that the next leaders in this new digital arena will be those who […]

The recent high-profile attacks against Colonial Pipeline and JBS Foods highlight that operational technology (OT) — the devices that drive gas flows and food processing, along with essentially all other machine-driven physical processes — does […]

The world of industrial control systems has been changing rapidly in recent years with digital convergence and the industrial internet of things placing almost everything on networks. While this can be good for productivity, it […]

When most people think of cyber threat, they think of information technology systems (IT). But in today’s increasingly interconnected environment, if you’re only protecting IT, you’re not protected at all. This expanded threat landscape and […]
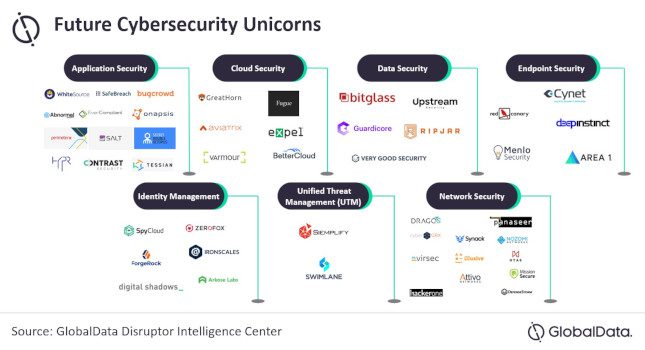
Right from the network and data security to identity management and unified threat management (UTM), startups are offering cybersecurity solutions to identify vulnerabilities, thwart attacks and secure networks. Against this backdrop, the unicorn prediction model […]

Industrial control systems are changing rapidly, but it might be time for a new type of ICS, says Albert Rooyakkers of Bedrock Automation

In 2020, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued 248 cybersecurity advisories for public consumption on the Cybersecurity and Infrastructure Security Agency’s (CISA) ICS-CERT portal. Verve analyzed all these advisories, regardless of whether […]
The recent shift toward edge computing has allowed for more efficient processing, but it’s also opened up new cybersecurity threats

“Hey Alexa, what do you do with my data?” Smart objects are growing in popularity in both our homes and workplaces, but you may get more than you expect. While they make lives easier and […]
To protect against cyberattacks, companies need to bridge the gap between IT and OT and enlist the OT side in threat management

To accommodate remote work and improve efficiency, 85% of IT organizations are considering or already using the public cloud. However, with some of their most crucial data still located within the corporate perimeter, NetOps must come up […]
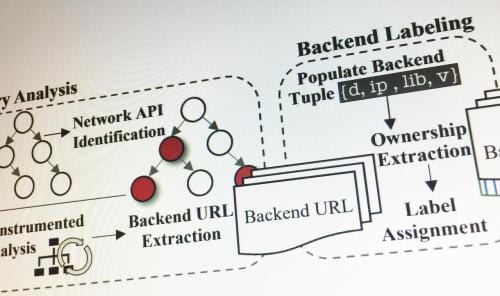
Cybersecurity researchers at Georgia Tech and Ohio State have discovered vulnerabilities in the backend systems that feed content and advertising to smartphone applications through a network of cloud-based servers that most users probably don’t even know exists.

As companies continue to adjust to the ever-evolving new normal in 2021, there will undoubtedly be additional shifts in work environments, internet usage, and the general status quo. With this in mind, Fortinet’s FortiGuard Labs’ Derek Manky […]

As much as the COVID-19 pandemic will be remembered for its chilling effect on business and economic activity, apparently it has had quite the opposite impact on industry’s zest for digital transformation and Industry 4.0 […]

Forward-looking organizations realize they need the same level of aggressiveness to protect assets as they have done for COVID-19 risk reduction. A three-pronged strategy on securing essential infrastructure is highlighted.
There are several preventive measures that can be taken to secure industrial processes against cyber attacks.

Cybersecurity strategy in digital plants is critical for companies that want to achieve smart manufacturing.

The Fourth Industrial Revolution has brought innovation and advanced technology, but it has also made these systems increasingly vulnerable. Industrial-grade cybersecurity is recommended.

The National Institute of Standards and Technology (NIST) has published a report to help organizations better understand and manage the cybersecurity and privacy risks associated with IoT devices throughout the devices’ lifecycles.

The Industrial Internet Consortium (IIC) has developed a white paper designed to bolster best practices related to the Industrial Internet of Things (IIoT) and data security.

Cybersecurity in the robotics field is still immature, but manufacturers are starting to realize the vulnerability that connected robots and automation equipment creates in their operations.

While traditional industrial networks are using Ethernet switches to prepare for the Industrial Internet of Things (IIoT) applications, there is a place for unmanaged switches, though they come with some risks.

Manufacturers are using the Industrial Internet of Things (IIoT) and Industrie 4.0 to make factories smarter, but they can’t lose sight of basic cybersecurity best practices.
Cybersecurity is a major concern during digital transformation and companies should be asking plenty of questions about how prepared everyone is.

Communication and understanding between the information technology (IT) and operations technology (OT) department needs to improve as cyber attacks become more prevalent.

An open, interoperable approach allows companies to get best-in-class solutions for hardware and software upgrades. See 10 reasons to upgrade process controls.

There is many opinions and beliefs on what an industrial control system (ICS) is and what the Industrial Internet of Things (IIoT) comprises, which makes a common understanding crucial.

Recently, Industrial Cybersecurity Pulse sat down with Lesley Carhart to discuss the proliferation of AI in cybersecurity.

While cloud and on-prem infrastructure deployments differ greatly, many cloud attacks are similar to traditional on-prem attacks.

The Securing the IIoT eBook includes stories on how to mitigate cloud security threat and accelerating smart manufacturing.

OPSWAT’s web application security report highlights the disparity between infrastructure upgrades, spending and security improvements.

Sung Kim of iBase-t talked with ICSP about how to protect MES from threat actors and what role zero trust plays in it.

There have been plenty of industry discussions around the need for IT/OT convergence. This is crucial to industry 4.0.

AT&T Cybersecurity released their 2023 Edge Ecosystem report about changes within the edge space and how it’s impacting industry sectors.

An airport in Bristol, England, incurred a ransomware attack, showing the vulnerabilities in the transportation sector.

Road testing to improve self-driving security is expensive and time-consuming, but CCI researchers developed a virtual option.

With industry 4.0, factories are becoming more connected. However, more connections in smart factories also mean more cyber risks.

ICS/OT manufacturing ecosystems were considered safe because they were closed-loop systems. Manufacturers realize that they’re vulnerable.

What caught our readers’ attention in 2022? Here are the top 10 Industrial Cybersecurity Pulse articles or the past year.

In this webcast, Matt Ziegler will discuss why it is important to understand what assets are on your XIoT network and how you can do so.

Gary Kneeland of Claroty discussed “Industrial Networks and the Extended Internet of Things (XIoT)” at Rockwell’s Automation Fair.

The Internet of Things (IoT) was evolving as a concept even before it was defined, with household objects quietly sprouting the ability to connect to the internet. Many of these devices have enriched lives to […]

Insider attacks on industrial and manufacturing targets are escalating. Where are these attacks coming from, and why are they on the rise?

Federated learning is a collaborative method for training a machine-learning model that keeps sensitive user data private.

IIoT connects the edge devices in OT networks directly to the Internet to enhance operational efficiencies.

With billions of connected devices, there’s need for a strong global baseline for IoT security in consumer products.

Recently, we have developed a higher level of digital dependence, which has called for an increase in cyber resilience.

Power companies, chemical plants, hospitals and critical infrastructure rely on cloud-based services to monitor and control vital processes. This means cloud-managed facilities and industrial control systems (ICS) face omnipresent threats. Rapidly advancing technology, changing work […]

Edge computing makes it possible to process data closer to where it was created, but as it becomes more prevalent, it’s having a major impact on communications, especially when it comes to Industrial Internet of Things (IIoT) security.

How can you address cybersecurity threats on the edge and develop the best edge security strategy for your organization

Securing operational technology (OT) networks requires a great deal of thought when designing and implementing security. Industrial networks contain a complex mix of specialized protocols and devices, including proprietary protocols developed for specific families of […]

According to Gartner, by 2025 cyberattackers will be able to weaponize operational technology (OT) environments to harm or kill humans, but this timeline is accelerating quickly. How might this happen? An example of this kind […]

A new and more reliable method to defend vulnerable data on the stack, a major memory region responsible for storing computer program data for processes, has been developed by an international Penn State-led team. Such […]

Whether you’re still adjusting to the work-from-home revolution brought on by COVID-19, looking to build a remote team to make better use of the talent pool, or just thinking of updating your accounting software, cloud […]

As we head into the Industry 4.0 era — where connected Internet of Things (IoT) devices and automation will reshape industries — our world is already highly connected. According to Statista, there are more than […]

Engineering researchers have developed a new approach for implementing ransomware detection techniques, allowing them to detect a broad range of ransomware far more quickly than previous systems. Ransomware is a type of malware. When a […]

Whether you’re still adjusting to the work-from-home revolution brought on by COVID-19, looking to build a remote team to make better use of the talent pool or thinking of updating accounting software, cloud accounting tools […]

Patch management in an operational technology (OT)/industrial control system (ICS) setting is full of challenges. From proprietary hardware and software to a lack of staff, inadequate or non-existent testing equipment, and regulatory reporting and system […]

Last year brought some of the most significant cyberattacks in history – from the Kaseya supply chain ransomware attack to cyber-criminals attempting to poison the water supply in Florida, to the already infamous Log4Shell vulnerability. […]

Manufacturers are under pressure to provide remote access and real-time data streams, while hoping keeping their facilities secure. While many have jumped in with reckless abandon, those manufacturers slower to adopt should learn from the […]

As we think about Industrial Internet of Things (IIoT) attacks, we break them down into three broad categories. The first is what we refer to as collateral damage. The best example of this is the […]

Not long ago, a major water utilities firm in the UK revealed plans to move a significant part of their supervisory control and data acquisition (SCADA) system to the cloud. This is one of the […]

Many people nowadays work in industries that largely rely on cloud computing to stay on top of their daily tasks. Moreover, the system allows people to seamlessly integrate as many employees as needed into any […]

As manufacturers continue to adopt Industry 4.0 and IIoT technology, cybersecurity is becoming more and more critical with each passing day. Successfully protecting a network requires not only constant vigilance but strategies for securing an […]

Attackers are increasingly gaining footholds into corporate environments to conduct ransomware or data theft operations via Internet-connected smart devices. Whether they be printers, lockers, aquariums or conference rooms, these seemingly innocuous access points to corporate […]

As the Industrial Internet of Things (IIoT) and other data-centric concepts are realized in businesses and on factory floors all over the world, the practice of aligning operational technology (OT) and information technology (IT) is […]

Since the start of the COVID-19 pandemic, the pace of digital transformation has accelerated tremendously. Meanwhile, companies have also become increasingly aware that the next leaders in this new digital arena will be those who […]

The recent high-profile attacks against Colonial Pipeline and JBS Foods highlight that operational technology (OT) — the devices that drive gas flows and food processing, along with essentially all other machine-driven physical processes — does […]

The world of industrial control systems has been changing rapidly in recent years with digital convergence and the industrial internet of things placing almost everything on networks. While this can be good for productivity, it […]

When most people think of cyber threat, they think of information technology systems (IT). But in today’s increasingly interconnected environment, if you’re only protecting IT, you’re not protected at all. This expanded threat landscape and […]

Right from the network and data security to identity management and unified threat management (UTM), startups are offering cybersecurity solutions to identify vulnerabilities, thwart attacks and secure networks. Against this backdrop, the unicorn prediction model […]

Industrial control systems are changing rapidly, but it might be time for a new type of ICS, says Albert Rooyakkers of Bedrock Automation

In 2020, the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) issued 248 cybersecurity advisories for public consumption on the Cybersecurity and Infrastructure Security Agency’s (CISA) ICS-CERT portal. Verve analyzed all these advisories, regardless of whether […]

The recent shift toward edge computing has allowed for more efficient processing, but it’s also opened up new cybersecurity threats

“Hey Alexa, what do you do with my data?” Smart objects are growing in popularity in both our homes and workplaces, but you may get more than you expect. While they make lives easier and […]

To protect against cyberattacks, companies need to bridge the gap between IT and OT and enlist the OT side in threat management

To accommodate remote work and improve efficiency, 85% of IT organizations are considering or already using the public cloud. However, with some of their most crucial data still located within the corporate perimeter, NetOps must come up […]

Cybersecurity researchers at Georgia Tech and Ohio State have discovered vulnerabilities in the backend systems that feed content and advertising to smartphone applications through a network of cloud-based servers that most users probably don’t even know exists.

As companies continue to adjust to the ever-evolving new normal in 2021, there will undoubtedly be additional shifts in work environments, internet usage, and the general status quo. With this in mind, Fortinet’s FortiGuard Labs’ Derek Manky […]

As much as the COVID-19 pandemic will be remembered for its chilling effect on business and economic activity, apparently it has had quite the opposite impact on industry’s zest for digital transformation and Industry 4.0 […]

Forward-looking organizations realize they need the same level of aggressiveness to protect assets as they have done for COVID-19 risk reduction. A three-pronged strategy on securing essential infrastructure is highlighted.

There are several preventive measures that can be taken to secure industrial processes against cyber attacks.

Cybersecurity strategy in digital plants is critical for companies that want to achieve smart manufacturing.

The Fourth Industrial Revolution has brought innovation and advanced technology, but it has also made these systems increasingly vulnerable. Industrial-grade cybersecurity is recommended.

The National Institute of Standards and Technology (NIST) has published a report to help organizations better understand and manage the cybersecurity and privacy risks associated with IoT devices throughout the devices’ lifecycles.

The Industrial Internet Consortium (IIC) has developed a white paper designed to bolster best practices related to the Industrial Internet of Things (IIoT) and data security.

Cybersecurity in the robotics field is still immature, but manufacturers are starting to realize the vulnerability that connected robots and automation equipment creates in their operations.

While traditional industrial networks are using Ethernet switches to prepare for the Industrial Internet of Things (IIoT) applications, there is a place for unmanaged switches, though they come with some risks.

Manufacturers are using the Industrial Internet of Things (IIoT) and Industrie 4.0 to make factories smarter, but they can’t lose sight of basic cybersecurity best practices.

Cybersecurity is a major concern during digital transformation and companies should be asking plenty of questions about how prepared everyone is.

Communication and understanding between the information technology (IT) and operations technology (OT) department needs to improve as cyber attacks become more prevalent.

An open, interoperable approach allows companies to get best-in-class solutions for hardware and software upgrades. See 10 reasons to upgrade process controls.

There is many opinions and beliefs on what an industrial control system (ICS) is and what the Industrial Internet of Things (IIoT) comprises, which makes a common understanding crucial.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.