Manufacturers are under pressure to provide remote access and real-time data streams, while hoping keeping their facilities secure. While many have jumped in with reckless abandon, those manufacturers slower to adopt should learn from the unpleasant experiences some have faced. Manufacturers should take the time and delve deeper into the organization’s needs and goals while considering associated risks.
What are some of the needs and goals fueling the push for an Internet of Things (IoT) solution? Consider the definition of industrial IoT and how it was designed to be used. The Industrial Internet of Things (IIoT) was defined as the creation of an intricate network of various “things,” each having a specific purpose and ranging from process monitoring to the ability to alter a selection process. The IoT is a means of creating an accurate picture of an associated process or event within an organization. How should it be used, though?
Traditionally, the goal has been straightforward: Once in place, a successful IoT solution should allow for educated business decisions based on accurate process and product data streams and specific key performance indicators (KPIs). Again, very straightforward, but that was then. Today, whether fueled by untrained maintenance teams who are at the mercy of equipment suppliers who then require remote connections to provide support, or compulsive wants realized by a sometimes-desperate internal management team, the result is haphazard mandates by management on getting the information technology (IT) and operational technology (OT) departments to converge.
IoT system failures
IoT systems have collided with an onslaught of failed attempts, expensive mistakes and broken promises made by IoT product suppliers. Why have these failures occurred, and what could have been done to avoid them? To answer this, understand those being forced to converge — IT and OT.
The IT group is responsible for the secure operation of any IT asset. These assets range from office telephones and email systems to the PCs used within the plant, and they are judged based on the continuous operation of these systems and the PCs and servers they rely on. Any lapse in the normal operations of these items, albeit by hardware or software failure, is grounds for dismissal. Of course, this includes cybercrime. Should any system fail because of malware or ransomware, the responsible IT employee could lose their job.
The OT group consists of production and quality managers, engineers and those in maintenance. These departments are judged based on the safe, efficient and successful production of parts while meeting quality standards and production goals. Any lapse in normal production, albeit due to quality, quantity or safety, is grounds for dismissal. OT’s goal is to deliver quality parts with the greatest efficiency by minimizing downtime events while reducing defect flow out. They do this by performing a stringent validation process on all new production equipment. Then they rely on production and quality standards to ensure the validated system is never changed.
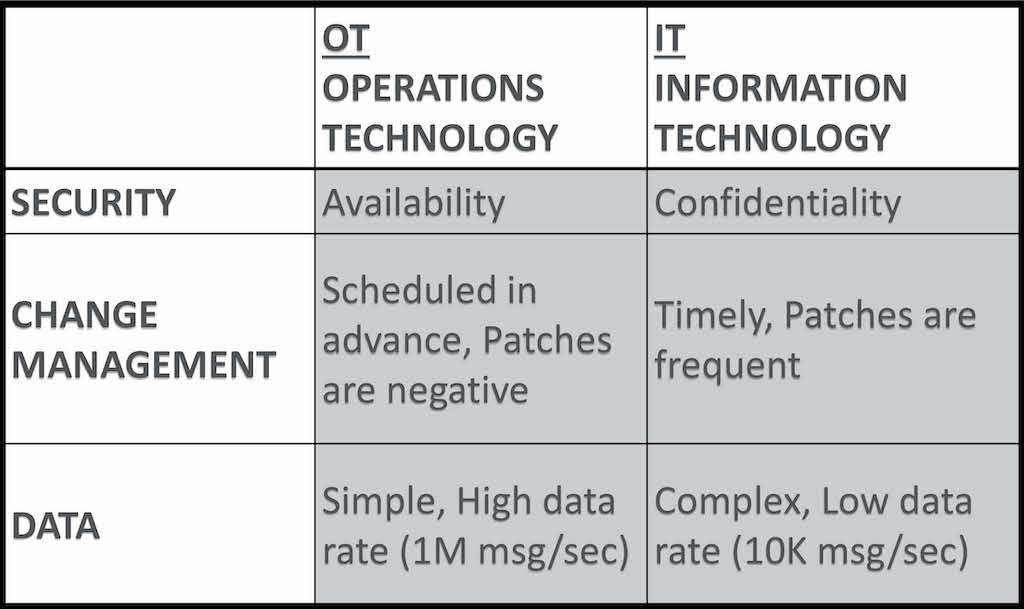
IT/OT philosophical distinctions
IT’s goal is ensuring the security of every IT-based asset, which requires constant updates to security systems and associated infrastructure, and OT’s goal is to maintain a constant process with limited variability to maximize production.
Are you realizing the dichotomy? One requires constant change and the other mandates sameness (see Table 1). The tragedy is this difference often has been used by IoT product suppliers to describe the “issue” preventing convergence. This is the point where the savvy and wise manufacturer avoids falling prey to this erroneously marketed definition of the IT/OT convergence problem.
Despite IT and OT’s glaring philosophical difference, each is fundamentally correct and equally important. The act of forcing compromise undermines the reason for each group. Consider this: What plant manager would think it wise to ask IT to overlook stringent cybersecurity practices to further the needs of production or support needs of maintenance? Conversely, what IT manager would insist production endure hours of downtime to allow IT to perform security updates on plant floor PCs as often as they deem necessary? Unfortunately, these sorts of ill-gotten decisions are often unknowingly made, which is where the actual tragedy occurs.
Vector pathways and cybersecurity
Any avenue by which malicious code may be introduced to an otherwise secured system is termed a “vector” by IT administrators. Vectors are often defined as phishing emails and infected external devices such as unmanaged PCs or drives, unsecure external connections. Cybersecurity is ever-evolving as new threats arise, but most IT departments have a good handle on these potential vector pathways. Still, new IoT products and offerings are being marketed with reckless abandon, each promising the moon, but many come up short. Whether the product works as advertised should not be the primary concern, rather, how the product is being marketed for use.
Most IIoT products are marketed to OT versus IT and promise superior security in situations where connection to external or subscription-based cloud servers is required. This begs the question: Why would marketers focus on OT versus IT? Their answer is quite simple: They are convinced the actual “issue” preventing IT/OT convergence is the “mean ole IT department” with their overbearing security practices. This is where things begin to get a little scary. The recent push for 5G cellular connections has been to bypass IT security thus creating a new vector unknown to IT. These systems claim to be secure and are designed to overcome security “obstacles” placed by IT, while they instead provide an unsecured backdoor to the epicenter of the plant — manufacturing.
A high-level IT consultant once said, “All of the security in the world becomes meaningless if a single unsecured vector is allowed to exist.” Despite the goal of the product or system, if it relies on a cellular connection to someone else’s server, it likely isn’t being secured by the manufacturer’s IT group. Heightened security measures, although touted by suppliers, lack any type of shared responsibility should security fail and the user falls victim to a cybercrime.

Risk assessment for IT and OT
How can manufacturers handle these new vectors? The answer: Conduct a reasonable risk analysis involving IT and OT departments. Decide now what levels of risk are acceptable and what outcomes are tolerable, keeping in mind those on the outside are pushing these systems for reasons that may not take the users’ best interest at heart.
If cybersecurity countermeasures are not a top priority for the plant, perhaps a cellular-based cloud connection is acceptable. Go ahead, converge your OT and IT networks. On the other hand, if cybersecurity is a concern, elliTek’s stance, while disruptive, has proven to be sound: Avoid forcibly converging IT and OT; separate them with a hardened gateway strategy.
Attacks ranging from viruses to malware, phishing and ransomware, unfortunately, can happen as there is no system offering 100% security. We urge our IoT clients to prepare for the worst. Today’s IIoT systems require data must transfer and external connections must occur, but then planning to create an environment that reduces cyber threats while working to help isolate any mishaps is smart. Even cloud-based systems, while still unpopular throughout some industries, can be manageable when IT is involved. Collaboration across IT, OT and management makes a much more pleasant implementation of IoT and heightens the overall chances of success. If a product claims 100% security, walk away.
Securing IT and OT networks
As industrial plants race to connect their control systems, hackers are ramping up to the big cyber business known as ransomware. Those industrial users failing to consider the risks open themselves up to the potential of physical, real-world damage by way of malicious code, which may stem from the unseen, virtual domain. Many forget the adage, “An ounce of prevention is worth a pound of cure,” and when the “cure” is being measured in $4.4 million-worth of cryptocurrency, things can take a serious turn very quickly.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








