When most people think of cyber threat, they think of information technology systems (IT). But in today’s increasingly interconnected environment, if you’re only protecting IT, you’re not protected at all. This expanded threat landscape and accelerated digital transformation was the focus of Day 1 of Fortinet’s Operational Technology Symposium, an online event held on Aug, 24, 2021. The goal of the Manufacturing Day was to provide advice and best practices on how to secure the future of industrial controls.
Opening Keynote: Operational Resilience in The Face of An Increasing Cyber Threat
Dale Peterson, CEO of Digital Bond, kicked off the event with his opening keynote, Operational Resilience in the Face of an Increasing Cyber Threat. Peterson began by discussing the Colonial Pipeline attack and how it acted as a sort of Rorschach test for cybersecurity professionals. The general response was about how people need to use two-factor authentication for remote access and that private industry needed to take a stronger hand by adding more controls to their systems. But Peterson suggested it’s more important to focus on the consequence side of the risk equation, or the effects of the attack.
“Colonial should leave you to ask one question: Can I manufacture and deliver products to customers if my IT network is compromised?” Peterson said.
While the Colonial attack apparently never got to the operational technology (OT) network, it still shut down the company’s capability to deliver products, which is a huge and expensive problem. Peterson said security experts should assume their networks are compromised and work on their recovery time objective (RTO).
“How long is it before I can get back up and running? Are you confident you can achieve it?” Peterson said. “The right people need to be asking this question.”
OT consequences should be added to an organization’s risk matrix. As Peterson said, “OT is not a special little flower.” Many executives overestimate what a cyber event means to a company and then rush to add more controls. Peterson said the goal should be to determine what makes a high-consequence event. Is a power plant outage a high-consequence event? On the Eastern seaboard, probably not. They can buy power from elsewhere if the plant goes down. In Maui, where there is only one power plant, it could be a major problem.
When trying to convince executives of the need for more cybersecurity, Peterson suggested stressing consequence reduction is more efficient than risk reduction. Adding additional controls and risk reduction is hard to quantify; working with consequences gives you hard numbers and allows you to speak a language executives understand.
Digital and Security Trends in the Manufacturing Sector
 Peterson was followed by Richard Kerslake, general manager of industrial controls and robots at Intel Corporation, who spoke about digital and security trends in the manufacturing sector. Much of his discussion was focused on the challenge of onboarding new technology.
Peterson was followed by Richard Kerslake, general manager of industrial controls and robots at Intel Corporation, who spoke about digital and security trends in the manufacturing sector. Much of his discussion was focused on the challenge of onboarding new technology.
Kerslake asked how long it takes to manually onboard 10,000 gateways, sensors or devices. The answer is more than two man-years, or about 20 minutes per device.
The manufacturing sector is becoming more interconnected with the Internet of Things (IoT), making security critical. Configuring credentials, or onboarding, is a slow and tedious process, and there has never been an industry standard for automated secure device onboarding.
Kerslake said the FIDO Alliance, a consortium of IoT experts looking to develop standards to simplify the onboarding process for manufacturers, is working to resolve that problem. The FIDO Alliance brings together the world’s leading tech companies to develop and promote the adoption of a standardized, simpler and more secure online experience that installs trust and confidence in a digital world. The consortium is backed by mega-companies like Amazon, Apple, Microsoft, Visa, Aetna, American Express and Google, and has a track record of successful collaboration. They assembled an IoT working group in summer 2019, and from 45 use cases, they were able to develop 19 derived requirements.
To learn more about Kerslake’s speech and the FIDO Alliance, check out our article on the project.
Case Studies: Securing Manufacturing’s Digital Infrastructure using Fortinet
Next up was Dee Kimata, director of cybersecurity offer management with Schneider Electric, to discuss implementing cybersecurity controls in a network segmentation space. She began by talking about cybersecurity requirements for manufacturing and said the key driver has been security standards. These standards present a framework to help mature a security posture year over year. Schneider uses the IEC 62443 framework. She said network segmentation is important. As we move forward with digitalization, data transfer must be secure, and companies must have the right segmentation to allow for that.
To solve some of Schneider’s problems, they leveraged a series of Fortinet products in standard architecture. They have Fortinet firewalls built into the Schneider reference architecture, and that structure allows for secure data transfer to support digital and cybersecurity solutions. The enterprise never connects directly to the distributed control system (DCS), but the required data can be transferred. She said network segmentation is required prior to implementing digital solutions to align to best practices.
Ultimately, she said, the journey of implementing OT security best practices is still ongoing. It’s a continuous journey and must improve year over year. The goal is to continue to implement controls and refine a strategy to meet your specific needs. Leveraging standards helps provide a roadmap or framework of where you need to go, while having a standard reference architecture helps provide context about how to standardize the approach to implementing solutions.
Manufacturers must optimize their operations. There are always going to be cybersecurity incidents and vulnerabilities. Companies must put themselves in a position to get information and remediate these issues, and collaborate with other organizations to get ahead of the issues.
Defense-in-Depth Security for Manufacturing
Carlos Sanchez, director of operational technology, Central USA at Fortinet, was next up to discuss the importance of defense in depth. With an increasingly connected OT environment, defense in depth is essential for manufacturers, Sanchez said.
Digital innovation is causing increased risk, and cyber threat actors seek to take advantage of the disruption. As the digital attack surface expands and the ecosystem gets more complex, the risk of OT infrastructure attacks is increasing.
This point was underscored by the attack on Merck, which resulted in a reported $1 billion loss. If companies are not producing, as Peterson said earlier, the financial implications can be great. But physical risk can also be great when threat actors level attacks on OT, or critical infrastructure, systems. These can impact the lives of employees and citizens. And because these systems cannot afford shutdowns, they are highly desirable targets for attackers.
So how can manufacturers mitigate cyber risk? Sanchez said they need visibility across the digital attack surface to protect against sophisticated threats. Defense in depth means adding multiple controls and layers of security around infrastructure. For example, there could be a policies layer, a physical layer, a perimeter layer, an internal network layer, a host layer, an app layer, etc.
For secure remote connectivity in the face of advanced persistent threat, companies need deep OT visibility, role-based access control, secure critical endpoints and centralized security management. Defense in depth requires multiple-point solutions, but using multiple vendors can create challenges. Segmentation is one of the most important security controls in any situation, as air gaps are disappearing. And companies need segmentation for both wired and wireless environments.
Sanchez ended by advising teams to, “Think like a bad guy. Security can’t be done by people who don’t think in a non-malicious way.” The risks are high, and air gap separation alone is no longer a successful strategy. Manufacturers must have stability and actionable intelligence to make smart decisions and face the growing threat head-on.
Closing Keynote: Manufacturing Is Both a Cybersecurity Target and a Vector
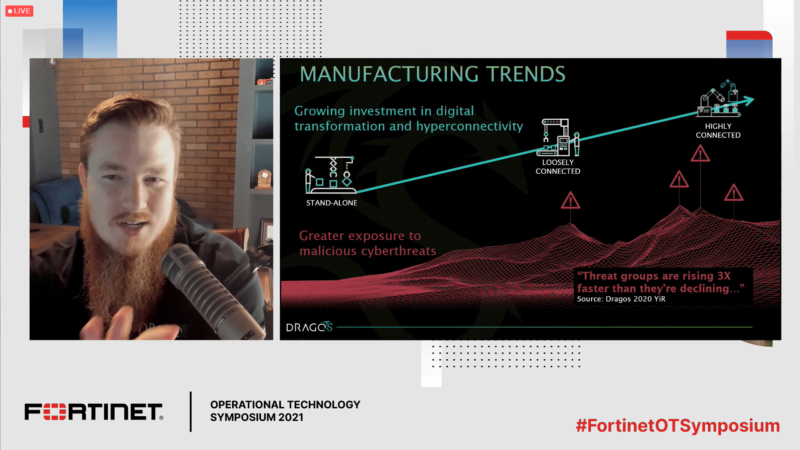 The three-hour program closed with a keynote from Robert M. Lee, CEO of Dragos, Inc., where he discussed how the manufacturing sector is both a target and a vector. According to Lee, the manufacturing environment is more digital and connected than ever before. This can be beneficial to businesses, to operations and to safety, but security can’t stand in the way of business profitability.
The three-hour program closed with a keynote from Robert M. Lee, CEO of Dragos, Inc., where he discussed how the manufacturing sector is both a target and a vector. According to Lee, the manufacturing environment is more digital and connected than ever before. This can be beneficial to businesses, to operations and to safety, but security can’t stand in the way of business profitability.
Companies now have greater exposure to cyber threats than ever before, as threat groups are rising three times faster than they’re declining.
Lee said OT leaders used to rely on air gaps to protect their systems, but most groups never truly had air gaps to begin with. There have always been routes open to original equipment manufacturers (OEMs), service providers and others. Networks have been connected in ways beyond our understanding for a long time, he said.
In today’s environment, we’re looking more for threats and are, of course, finding more. That, Lee said, is a sign of maturity. As we take a deeper look into OT networks, we’re finding issues that have been there for a while.
Lee’s main advice for securing ICS critical vulnerabilities in manufacturing was not to “gold plate” your response. He, instead, suggested doing four or five things really well. Don’t focus on malware, he said, but on the human threat problem. What matters are the operators behind the malware and how they’re using it.
The threat, he said, is much worse than you realize — for every reported case of ransomware, there are 20 behind the scenes, and a significant portion of those are in manufacturing — but there’s “no need to freak out.”
Everyone will get breached. Lee said even Dragos, as a security company, will get breached eventually. It’s all about how you respond to it. That’s what you get measured on. For a more comprehensive review of Lee’s closing keynote, please check out our article here.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.









