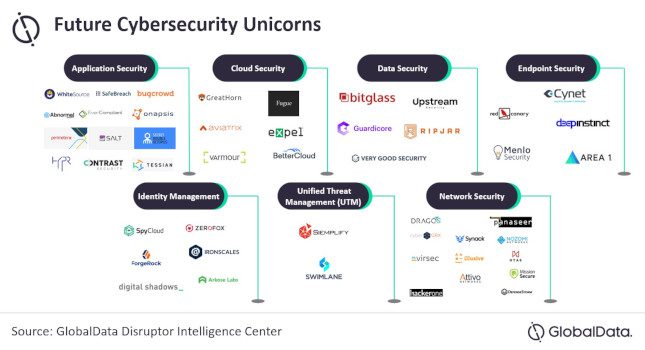
How cyberattacks take down critical infrastructure
The recent high-profile attacks against Colonial Pipeline and JBS Foods highlight that operational technology (OT) — the devices that drive gas flows and food processing, along with essentially all other machine-driven physical processes — does […]