Learning Objectives
- ICS cybersecurity threats are increasing.
- Industrial networked devices, engineering workstation, remote sites may be sources of cybersecurity vulnerabilities.
- Standards and best practices, consistently applied, can decrease cybersecurity risk.
It’s no secret information technology (IT) infrastructure and operational technology (OT) networks are converging, creating conditions that require industrial control systems (ICS) to become part of an overall cybersecurity program. It will be incumbent upon business leaders and decision makers to avoid ICS vulnerabilities by understanding this collision and how to best extend core security controls, governance processes, and the technology stack to cover OT as well as it does IT.
One foundational place to begin is vulnerability management.
The disappearing landscape of air-gapped critical OT systems, where these systems are sheltered from internet connectivity, demonstrates this approach isn’t conducive to 21st-century business. Connectivity is oxygen for businesses, including industrial control systems and the processes they manage. While this is a positive, the tradeoff is the potential attack surface available to threat actors, both profit-driven cybercriminals and state actors, gets larger.
Therefore, organizations must prioritize vulnerability management in order to strategically lessen their overall exposure, in addition to other security best practices such as network segmentation and the security of remote connections to OT networks. The first step is understanding the vulnerability landscape as it relates to OT and identify noteworthy trends in order to best prioritize patching and updating vulnerable systems.
Cybersecurity management system
The ISA/IEC 62443 series of standards provides a methodology for an organization to establish an OT security program. [ISA is the International Society of Automation. IEC stands for International Electrotechnical Commission.] The cybersecurity management system (CSMS) overviews the elements required for an organization to evaluate its current risks, how to address them, and keep its CSMS updated. Organizations often try to dive headfirst into the specifics of their ICS systems, trying to extrapolate every detail.
While larger organizations sometimes have personnel to implement such a resource intensive methodology, most organizations struggle to deal with the expanding attack surface, which requires a risk assessment methodology that prioritizes remediating the highest risks. The CSMS provides this methodology by focusing organizations to build a risk analysis founded on business rationale and risk identification that considers not only financial loss but also health, safety, environmental, and any other consequences if the ICS environment was impacted by a cybersecurity attack.
In August 2020, Claroty published a review of industrial control system vulnerabilities publicly disclosed during the first half of 2020. The vulnerabilities identified were reported to the Industrial Control System Cybersecurity Emergency Response Team (ICS-CERT) or published by the National Vulnerability Database (NVD).
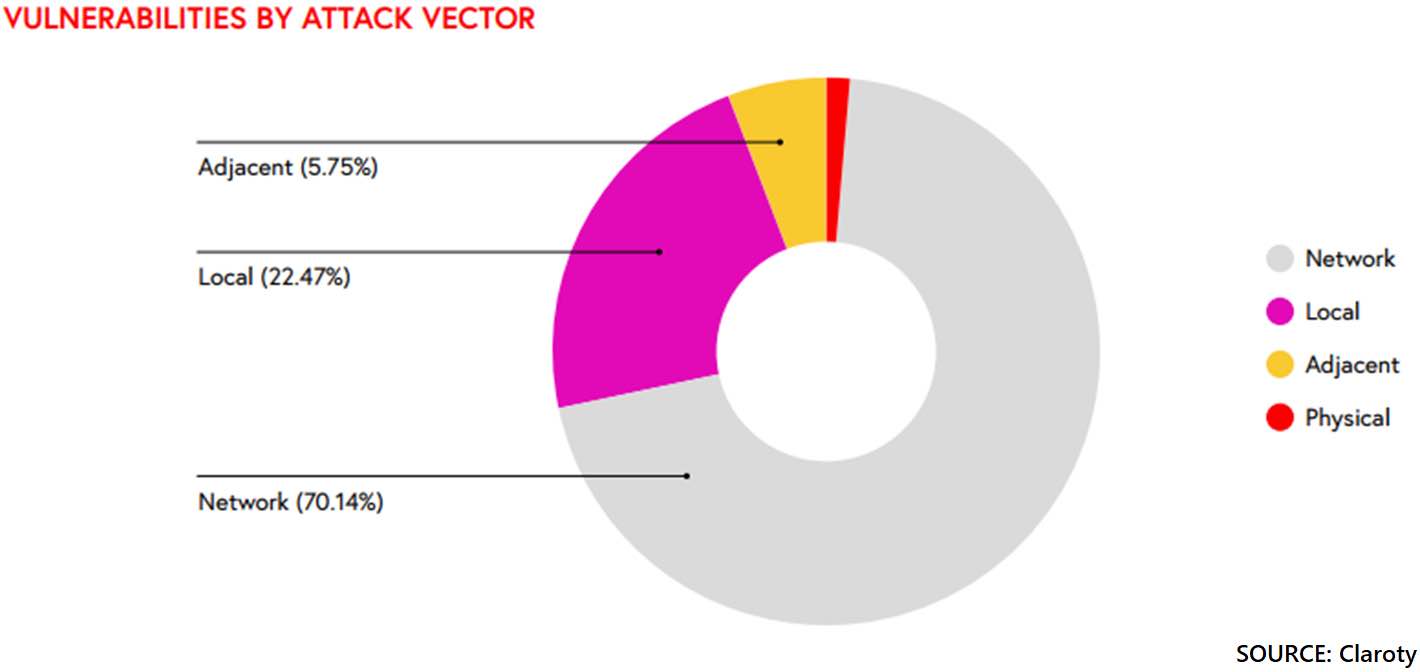
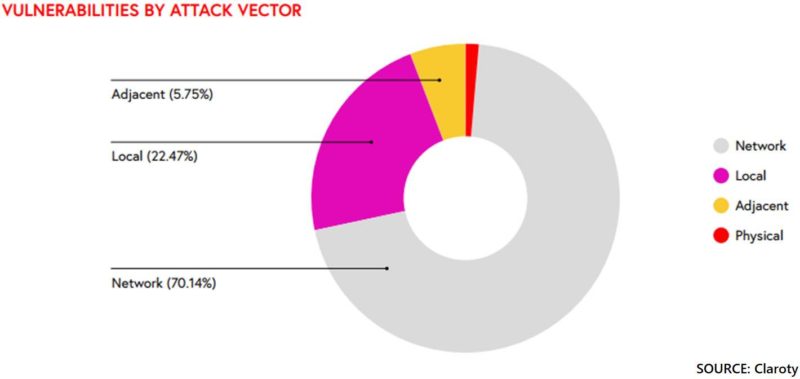
The report revealed more than 70% of the 365 vulnerabilities affecting ICS products sold by more than 50 vendors were remotely exploitable. This puts industrial equipment in the crosshairs of an exponentially larger set of potential attackers, ones already adept at targeting internet-facing IT infrastructure. Vulnerable ICS devices exposed online threaten the safety and reliability of industrial processes and could be attractive to hackers because of lax patching and inadequate software or firmware mechanisms available to devices.
Remote areas behind in software patches
Since many devices are operating remotely in difficult-to-reach locations, or where downtime may not be an option, a large number of them may be several patching cycles behind where they should be.
Shodan, a search engine for internet-connected devices, has a specific search engine for ICS devices and has unveiled a staggering number of devices publicly available around the globe. Numbers as of Nov. 23, 2020, indicate roughly 4,000 EtherNet/IP devices and more than 13,000 Modbus devices are internet connected. These devices, which are inherently insecure, along with research showing the remote exploitability of most vulnerabilities, give a good indication of the risk landscape many organizations face today.
Organizations should also understand what product types are most vulnerable. The Claroty report said engineering workstations (EWS) and programmable logic controllers (PLCs) make up the majority of vulnerabilities uncovered and disclosed during the first half of 2020. This is problematic because these product types play such crucial roles in industrial operations and therefore, as connectivity grows, also may appeal to attackers scanning for vulnerabilities.
Engineering workstations: 58% of vulnerabilities
EWS applications – accounting for 58% of reported vulnerabilities found by Claroty researchers – should be prioritized in any OT, or converged IT/OT, environment because of their connectivity to the IT network, as well as their access to the shop floor and devices such as programmable logic controllers (PLCs) that control physical processes within OT networks. An adversary capable of accessing an EWS gains a network foothold, critical in many modern advanced attacks where lateral movement and process manipulation or interruption via denial-of-service attacks or ransomware, for example, is the endgame.
Remote code execution attacks are a severe threat to OT networks, and account for a large number of the high-severity ICS vulnerabilities published by the NVD and ICS-CERT. Remote code execution attacks, combined with denial-of-service attacks, account for more than 80% of the vulnerability impacts possible if any of the flaws discovered were exploited.
It’s also important to note how these vulnerabilities impact critical infrastructure sectors. Energy, critical manufacturing, and water and wastewater infrastructures were the most impacted by vulnerabilities listed in ICS-CERT advisories during the first six months of 2020; the water and wastewater sector alone experienced a 122% increase in vulnerabilities acknowledged by ICS-CERT; critical manufacturing and energy also were up 87.3 and 58.9%, respectively.
ICS vulnerabilities up 10% in first half 2020
Unfortunately, the number of ICS vulnerabilities disclosed during the first half of 2020 is trending in the wrong direction, up by 10% overall compared to the first half of 2019. Claroty researchers point out, however, this isn’t necessarily an indication of increased attacker activity targeting ICS devices and OT networks. Instead, it could be an indication of more scrutiny on these devices by legitimate researchers and heightened awareness of the risks posed by these flaws should they be attacked.
Progress in cybersecurity standards and practices give a roadmap for securing their industrial infrastructure. Once an organization has established a CSMS and has performed a risk analysis, a high-level risk assessment can be performed to understand the impacts to the organization. High-risk areas can then be detailed, starting with a full asset inventory and organizing assets into zones. Zones are a logical or physical grouping of assets requiring the same security requirements and conduit a logical grouping of communication devices providing security over its channel.
It should be noted asset inventories are often underestimated endeavors and, if performed manually, become labor intensive and get outdated quickly. It’s recommended that passive scanning tools designed for ICS environments be leveraged to minimize error, manual labor, and inventory maintenance, enabling the much-needed personnel to focus on higher-value efforts. Once the asset inventory is completed, a vulnerability assessment must be performed, allowing organizations to start identifying and prioritizing risk.
Cybersecurity: Security levels 0-4
The ISA/IEC 62443 series defines a set of security levels (SL) ranging from 0 to 4 defined as follows.
- SL 0 – No specific requirement or security protection necessary,
- SL 1 – Protection against casual or coincidental violation,
- SL 2 – Protection against intentional violation using simple means with low resources, generic skills and low motivation
- SL 3 – Protection against intentional violation using sophisticated means with moderate resources, IACS specific skills and moderate motivation, and
- SL 4 – Protection against intentional violation using sophisticated means with extended resources, IACS specific skills and high motivation.
Cybersecurity foundational requirements, 1-7
Each zone should be assigned a Target SL (SL-T) in which the Achieved SL (SL-A) and Capability SL (SL-C) – an output of the risk assessment – can be compared for each zone to understand the required compensating countermeasures. To ensure methods of reaching the SL-T are clear, the series contains seven foundational requirements (FR) which are
- FR 1 – Identification and authentication control (IAC),
- FR 2 – Use control (UC),
- FR 3 – System integrity (SI),
- FR 4 – Data confidentiality (DC),
- FR 5 – Restricted data flow (RDF),
- FR 6 – Timely response to events (TRE), and
- FR 7 – Resource availability (RA).
Leveraging the ISA/IEC62443-3-3 standard, an organization is able to understand the full spectrum of compensating countermeasures and controls required for them to meet their SL-T. ISA has more about the ISA/IEC62443 series of cybersecurity standards at www.isa.org/isa99.
Respond to increased cybersecurity threats
Research indicates threats to the OT landscape are not slowing down. Threat actors have every reason, whether it be for monetary gain or state sponsored government efforts, to attack the ICS environment, which has never been more connected than now. It is critical an organization follow a standard such as the ISA/IEC62443 series CSMS which defines a program that understands risk based on business rationale and mitigates risk in a prioritized fashion. The standard provides well-defined foundational requirements every organization should have. It also allows flexibility based on the SL assigned.
Organizations also should follow a number of critical best practices to secure internet-facing ICS devices, primarily to ensure patch levels are current in order to stem the threat posed by software and firmware vulnerabilities. Devices should also be password-protected, and granular controls should be in place governing who can access devices. Remote access connections should be monitored and secured by technologies appropriate to OT networks rather than an IT-friendly virtual private network (VPN). Organizations should also inventory available assets, segment networks, monitor for threats, and periodically review and update vulnerability management and risk management practices. Establishing a strong ICS cybersecurity posture is not simple, but it is possible with standard frameworks and toolsets.
Isaac Guevara is ICS network design specialist at Grantek, and Chen Fradkin is security researcher at Claroty.
CONSIDER THIS
Are multiple experts assessing and addressing ICS cybersecurity vulnerabilities in your organization?
ONLINE source
ISA/IEC62443 series of cybersecurity standards.
RELATED ARTICLES
Five steps to improve OT, ICS awareness in manufacturing cybersecurity
https://www.industrialcybersecuritypulse.com/five-steps-to-improve-ot-ics-cybersecurity-awareness-in-manufacturing/
IIoT’s growing impact on ICS cybersecurity
https://www.industrialcybersecuritypulse.com/iiots-growing-impact-on-ics-cybersecurity/
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.