
Determining the impact of AI on cybersecurity and sustainability
During a panel discussion at ARC Forum, experts from Honeywell talked about the impact of AI on cybersecurity and sustainability.

During a panel discussion at ARC Forum, experts from Honeywell talked about the impact of AI on cybersecurity and sustainability.

In this episode of Bridging the Gap, we discuss the strengths and weaknesses of AI and how it’s being used in automation and cybersecurity.

In the second episode of Bridging the Gap, we covered AI implementation in industrial automation and cybersecurity spaces.

AI has become integral to everything from supply chain optimization to cybersecurity, but that doesn’t mean its adoption has been seamless.

Concerns about network security due to the risks from VPNs can be mitigated through the use of zero-trust architecture.

Despite their benefits, smart factories can expose people, technology, physical processes and intellectual property to attack.

Moty Kanias of Nanolock talks about how increasing connectivity has streamlined many work processes but also opened up new vulnerabilities.

Ethernet with TSN can provide several performance benefits, such as greater transparency and increased productivity, and enhance security.

According to a Future Market Insights study,- ESOMAR-certified market research and consulting firm- the Industrial Cybersecurity Market is anticipated to record a CAGR of 7.7% during the forecast period ranging from 2022-2032. The global industrial […]

ColdLock ransomware hits several key critical infrastructure assets in Taiwan, including state-run petrochemical company CPC.
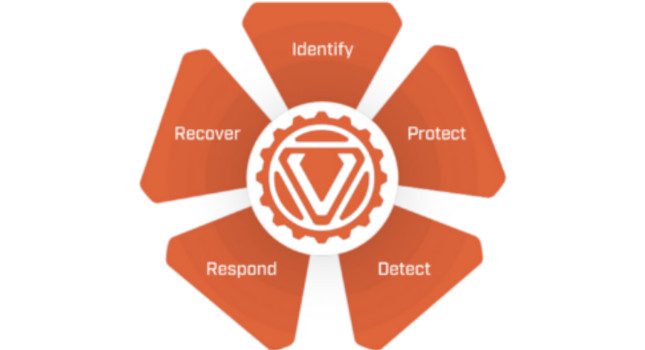
People may have heard “NIST CSF” thrown around by colleagues or leadership in relation to how security policies and procedures should be set up. The NIST CSF is one of several cybersecurity frameworks (along with […]

When establishing and testing a brand new cybersecurity program, it can be difficult to know exactly which steps are reasonable to take and when to take them. In this blog, we will talk about when […]

As society has progressed into a more technological era, an increase in cyberattacks has logically followed suit. Any technology connected to the internet — or even capable of a Bluetooth connection — is susceptible to […]

Defining Awareness First, what is a cybersecurity awareness program? It is a structured approach to managing an organization’s human risk. You can gauge and measure the maturity of an awareness program by using the Security […]

On March 14, 2022, a massive DDoS (Distributed Denial of Service) attack hit Israel, affecting many government websites. For those who may not know what a DDoS attack is, in a DoS cyberattack, “the perpetrator […]

Major Trends in ICS Cybersecurity ICS cyberattacks involving cyber criminals, hacktivists, and nation states are on the rise Most organizations recognize risks to their ICS and are taking numerous initiatives to address these risks The […]

On Monday, March 21, 2022, the Biden White House released a statement advising U.S. private sector organizations to strengthen their cybersecurity practices, citing intelligence reports indicating that Russia is looking at options for cyberattacks against […]

The U.S. Department of Defense (DoD) remains committed to safeguarding sensitive national security information by protecting the defense industrial base (DIB) from increasingly frequent and complex cyberattacks. The agency recently released its CMMC 2.0 framework […]

The U.S. market expects to see at least 100 electric vehicle (EV) models by the end of 2022, up from the roughly 62 models currently available. This momentum was witnessed in all of the EV-related […]

The certification issued by an ISASecure Accredited Certification Body is the highest global recognition for cybersecurity-related products and demonstrates that the applicable ISA/IEC 62443 requirements have been met throughout the whole lifecycle. Why obtain the […]

ISASecure certification is a third-party conformity assessment scheme based on the ISA/IEC 62443 series of standards aimed at cybersecurity certification of industrial automation and control systems (IACS), such as distributed control systems (DCS) and supervisory […]

IEC 62443 is the international reference standard for industrial cybersecurity of components and systems developed in conformity with ISA/IEC requirements. IEC 62443 family of standards The most relevant parts of IEC 62443, for the development […]

Amid continuing disruption to the global supply chain, industrial organizations are seeking ways to stabilize their operations in order to preserve their competitive advantage. One of the most efficient ways to achieve resilient industrial operations […]

The Department of Homeland Security, via the National Cyber Awareness System (NACS), recently released a report on the extent that malicious actors are turning concern over the COVID-19 virus into opportunities to steal user data. The […]

As Black Friday and Cyber Monday approach, retailers are gearing up for what is predicted to be a holiday season worth around $214 billion in e-commerce sales. They are not alone in making special preparations: In […]

As a very young kid, I would ask my dad, “Dad, what do engineers do?” And the response was always, “They solve problems.” And then I’d ask, “What do designers do?” And he’d say, “They […]
Analyzing packet level data within a network has become a vital component in an organization’s security architecture. Packet level visibility provides essential information needed to protect against security breaches that affect business operations. When implementing […]

As society continues to modernize and advance at an ever-quickening pace, it is getting harder for business owners and executives to not know and understand how information technology (IT) impacts their business. Regardless of the […]

In industrial automation, serial-to-Ethernet converters/gateways and serial device servers are a widely used method for enabling remote communications and monitoring of devices that only support serial interfaces such as RS-232, RS-485, and RS-422, to name […]

As the USA prepared for a holiday weekend ahead of the Fourth of July, the ransomware group REvil was leveraging a vulnerability in Kaseya software to attack managed service providers (MSPs) and their downstream customers. […]
The closing months of 2020 saw a 45% increase in cyber-attacks targeted towards healthcare organizations. Healthcare providers of all types and sizes have been breached. A report by Black Book Market Research predicts that data […]

Ransomware groups are coming and going faster than ever. In June alone, we saw Avaddon release its decryption keys unprompted and disappear from sight, while members of CLOP were arrested in Ukraine. The move follows […]

Ransomware attacks have been surging, with hackers striking major pieces of critical infrastructure. But large companies are far from alone

Defending critical infrastructure environments requires 360-degree visibility into asset and network vulnerabilities, which is why a vulnerability assessment is so important. Vulnerability management teams often face difficulties in patching all of their systems on a […]

As national critical infrastructure and private industry alike have increasingly been targeted by hackers in recent years, it has become clear that nothing is safe from savvy and motivated threat actors. As a result, the […]

As we made an almost overnight move to a remote workforce as a result of the pandemic, we have increased data security risks and new risks for data exfiltration. The result of this is inevitable […]

While millions of Americans were celebrating the long Fourth of July holiday weekend, the notorious REvil cybercriminal gang was busy proving cyber threat never rests. Businesses around the globe are still reeling from what may […]

We’re seeing a change in cybercrime and the way cyberattacks are being performed. A recent set of attacks against critical infrastructure entities exposed a new approach to cybercrime and critical infrastructure hacks. Oil and gas […]

Hackers, with the backing of a foreign power, infiltrated the Pickett Gap water treatment facility in Tennessee with a remote viral attack. Thankfully, plant managers were able to avert the crisis and prevent thousands of […]

The Colonial Pipeline, Iranian Centrifuges, large financial companies and large companies in general, big cities – these are the notable targets of cyber attackers. Seen within this context, it is easy to assume your company […]

The impact of cybersecurity breaches on infrastructure control system owners/operators is more visible than ever before. Whether you work for an infrastructure owner/operator or are a consumer of an infrastructure service, the events of the […]

In February of this year, I had COVID-19 symptoms and tested positive. I thought I was reasonably “disconnected.” Turns out, I was not. You may think your manufacturing systems or industrial control systems are similarly […]

Let’s face facts: sooner or later the hackers will come for you. Don’t let yourself think that you don’t have anything that they want. Everyone has something of value. What can companies do to protect […]

The low-level risk assessment is a detailed analysis typically performed after a high-level risk assessment or, sometimes, conducted on specific plants in order to deeply assess the precise risk estimate of a cyber attack. In […]

Across a complete IEC 62443 risk assessment, the High Level Risk Assessment is performed to determine the potential consequences in the event that a plant/system is compromised by a cyber attack. High-level risk assessment helps […]

A risk-based approach to cybersecurity without basic cyber hygiene is a fool’s errand, leading to short-term prioritizations and a game of musical chairs where you hope you aren’t the one left standing when the music […]

Americans are losing billions due to internet crime each year. However, 2020 was a record year for the number of cybercrime victims and the combined financial losses caused by these malicious attacks. According to data […]
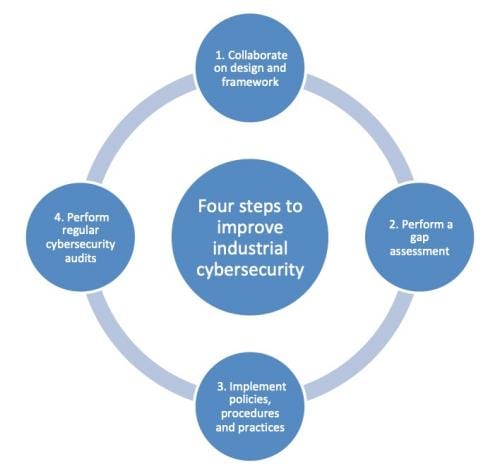
Catastrophic disaster can be the result of insecure industrial cybersecurity practices. See six common entry points for attacks, eight cybersecurity precautions for attacks by type, and four steps to improve.

While industry sectors are starting to automate their processes to help increase productivity and efficiency and this requires greater connectivity, which also can expose systems to attack.

The industrial control system (ICS) security community and asset owners need to grow up in 2021. There is near hysteria whenever there is an actual, potential or mythical breach of an ICS, regardless of the […]

Bayshore Networks and GE Digital announced an expansion to their partnership to integrate their solutions to address the growing need to secure industrial and critical infrastructure networks. GE Digital’s OpShield technology will be integrated into […]

Four myths about networking and cybersecurity related to operations technology (OT) systems are highlighted as well as three pillars for securing industrial networks.

According to a Ponemon study, 82% of cybersecurity expenditures go toward post-hoc measures, such as detection, containment and recovery. Only 18% of budgets are invested in prevention – yet financial figures may not be the […]
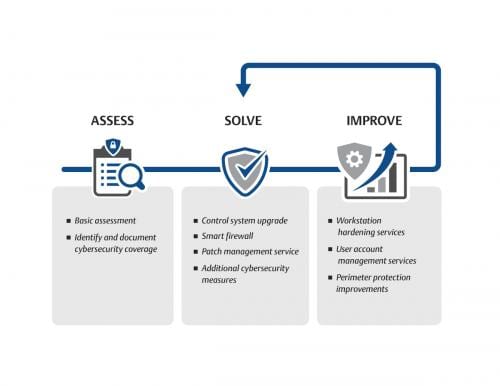
Simple strategies to achieve the most value from cyber risk assessments. Three strategies for operations technology (OT) teams to avoid while performing assessments are highlighted.
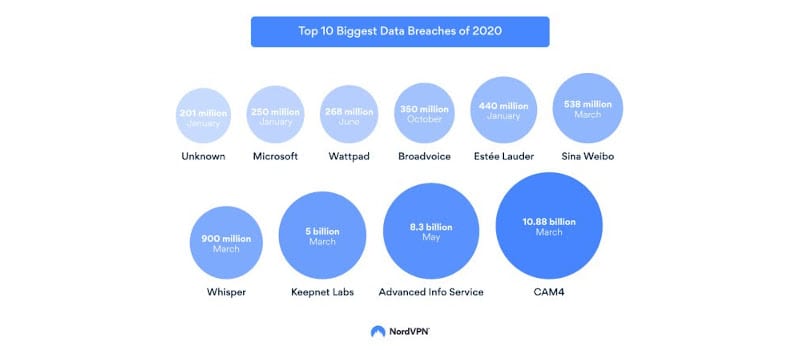
Hackers were as active as ever in 2020 by taking advantage of users’ vulnerabilities and the economic disruption amid the global COVID-19 pandemic. The number of cyberattacks is rising every year, and 2020 saw a […]

Many chief information security officers (CISOs) sacrificed cybersecurity as a major priority in an effort to enable employees to perform remote work when the COVID-19 pandemic hit. Much of the workforce plans on operating this […]

More workers are forced to work remotely due to COVID-19, but cybersecurity prevention and training is lagging behind.

Researchers at the U.S. Army Research Laboratory (ARL) and Towson University are developing a method on compressing network traffic as much as possible without losing the ability to detect and investigate malicious activity.

With increased connectivity between different devices, it’s critical to implement additional cybersecurity measures.

During a panel discussion at ARC Forum, experts from Honeywell talked about the impact of AI on cybersecurity and sustainability.

In this episode of Bridging the Gap, we discuss the strengths and weaknesses of AI and how it’s being used in automation and cybersecurity.

In the second episode of Bridging the Gap, we covered AI implementation in industrial automation and cybersecurity spaces.

AI has become integral to everything from supply chain optimization to cybersecurity, but that doesn’t mean its adoption has been seamless.

Concerns about network security due to the risks from VPNs can be mitigated through the use of zero-trust architecture.

Despite their benefits, smart factories can expose people, technology, physical processes and intellectual property to attack.

Moty Kanias of Nanolock talks about how increasing connectivity has streamlined many work processes but also opened up new vulnerabilities.

Ethernet with TSN can provide several performance benefits, such as greater transparency and increased productivity, and enhance security.

According to a Future Market Insights study,- ESOMAR-certified market research and consulting firm- the Industrial Cybersecurity Market is anticipated to record a CAGR of 7.7% during the forecast period ranging from 2022-2032. The global industrial […]

ColdLock ransomware hits several key critical infrastructure assets in Taiwan, including state-run petrochemical company CPC.

People may have heard “NIST CSF” thrown around by colleagues or leadership in relation to how security policies and procedures should be set up. The NIST CSF is one of several cybersecurity frameworks (along with […]

When establishing and testing a brand new cybersecurity program, it can be difficult to know exactly which steps are reasonable to take and when to take them. In this blog, we will talk about when […]

As society has progressed into a more technological era, an increase in cyberattacks has logically followed suit. Any technology connected to the internet — or even capable of a Bluetooth connection — is susceptible to […]

Defining Awareness First, what is a cybersecurity awareness program? It is a structured approach to managing an organization’s human risk. You can gauge and measure the maturity of an awareness program by using the Security […]

On March 14, 2022, a massive DDoS (Distributed Denial of Service) attack hit Israel, affecting many government websites. For those who may not know what a DDoS attack is, in a DoS cyberattack, “the perpetrator […]

Major Trends in ICS Cybersecurity ICS cyberattacks involving cyber criminals, hacktivists, and nation states are on the rise Most organizations recognize risks to their ICS and are taking numerous initiatives to address these risks The […]

On Monday, March 21, 2022, the Biden White House released a statement advising U.S. private sector organizations to strengthen their cybersecurity practices, citing intelligence reports indicating that Russia is looking at options for cyberattacks against […]

The U.S. Department of Defense (DoD) remains committed to safeguarding sensitive national security information by protecting the defense industrial base (DIB) from increasingly frequent and complex cyberattacks. The agency recently released its CMMC 2.0 framework […]

The U.S. market expects to see at least 100 electric vehicle (EV) models by the end of 2022, up from the roughly 62 models currently available. This momentum was witnessed in all of the EV-related […]

The certification issued by an ISASecure Accredited Certification Body is the highest global recognition for cybersecurity-related products and demonstrates that the applicable ISA/IEC 62443 requirements have been met throughout the whole lifecycle. Why obtain the […]

ISASecure certification is a third-party conformity assessment scheme based on the ISA/IEC 62443 series of standards aimed at cybersecurity certification of industrial automation and control systems (IACS), such as distributed control systems (DCS) and supervisory […]

IEC 62443 is the international reference standard for industrial cybersecurity of components and systems developed in conformity with ISA/IEC requirements. IEC 62443 family of standards The most relevant parts of IEC 62443, for the development […]

Amid continuing disruption to the global supply chain, industrial organizations are seeking ways to stabilize their operations in order to preserve their competitive advantage. One of the most efficient ways to achieve resilient industrial operations […]

The Department of Homeland Security, via the National Cyber Awareness System (NACS), recently released a report on the extent that malicious actors are turning concern over the COVID-19 virus into opportunities to steal user data. The […]

As Black Friday and Cyber Monday approach, retailers are gearing up for what is predicted to be a holiday season worth around $214 billion in e-commerce sales. They are not alone in making special preparations: In […]

As a very young kid, I would ask my dad, “Dad, what do engineers do?” And the response was always, “They solve problems.” And then I’d ask, “What do designers do?” And he’d say, “They […]

Analyzing packet level data within a network has become a vital component in an organization’s security architecture. Packet level visibility provides essential information needed to protect against security breaches that affect business operations. When implementing […]

As society continues to modernize and advance at an ever-quickening pace, it is getting harder for business owners and executives to not know and understand how information technology (IT) impacts their business. Regardless of the […]

In industrial automation, serial-to-Ethernet converters/gateways and serial device servers are a widely used method for enabling remote communications and monitoring of devices that only support serial interfaces such as RS-232, RS-485, and RS-422, to name […]

As the USA prepared for a holiday weekend ahead of the Fourth of July, the ransomware group REvil was leveraging a vulnerability in Kaseya software to attack managed service providers (MSPs) and their downstream customers. […]

The closing months of 2020 saw a 45% increase in cyber-attacks targeted towards healthcare organizations. Healthcare providers of all types and sizes have been breached. A report by Black Book Market Research predicts that data […]

Ransomware groups are coming and going faster than ever. In June alone, we saw Avaddon release its decryption keys unprompted and disappear from sight, while members of CLOP were arrested in Ukraine. The move follows […]

Ransomware attacks have been surging, with hackers striking major pieces of critical infrastructure. But large companies are far from alone

Defending critical infrastructure environments requires 360-degree visibility into asset and network vulnerabilities, which is why a vulnerability assessment is so important. Vulnerability management teams often face difficulties in patching all of their systems on a […]

As national critical infrastructure and private industry alike have increasingly been targeted by hackers in recent years, it has become clear that nothing is safe from savvy and motivated threat actors. As a result, the […]

As we made an almost overnight move to a remote workforce as a result of the pandemic, we have increased data security risks and new risks for data exfiltration. The result of this is inevitable […]

While millions of Americans were celebrating the long Fourth of July holiday weekend, the notorious REvil cybercriminal gang was busy proving cyber threat never rests. Businesses around the globe are still reeling from what may […]

We’re seeing a change in cybercrime and the way cyberattacks are being performed. A recent set of attacks against critical infrastructure entities exposed a new approach to cybercrime and critical infrastructure hacks. Oil and gas […]

Hackers, with the backing of a foreign power, infiltrated the Pickett Gap water treatment facility in Tennessee with a remote viral attack. Thankfully, plant managers were able to avert the crisis and prevent thousands of […]

The Colonial Pipeline, Iranian Centrifuges, large financial companies and large companies in general, big cities – these are the notable targets of cyber attackers. Seen within this context, it is easy to assume your company […]

The impact of cybersecurity breaches on infrastructure control system owners/operators is more visible than ever before. Whether you work for an infrastructure owner/operator or are a consumer of an infrastructure service, the events of the […]

In February of this year, I had COVID-19 symptoms and tested positive. I thought I was reasonably “disconnected.” Turns out, I was not. You may think your manufacturing systems or industrial control systems are similarly […]

Let’s face facts: sooner or later the hackers will come for you. Don’t let yourself think that you don’t have anything that they want. Everyone has something of value. What can companies do to protect […]

The low-level risk assessment is a detailed analysis typically performed after a high-level risk assessment or, sometimes, conducted on specific plants in order to deeply assess the precise risk estimate of a cyber attack. In […]

Across a complete IEC 62443 risk assessment, the High Level Risk Assessment is performed to determine the potential consequences in the event that a plant/system is compromised by a cyber attack. High-level risk assessment helps […]

A risk-based approach to cybersecurity without basic cyber hygiene is a fool’s errand, leading to short-term prioritizations and a game of musical chairs where you hope you aren’t the one left standing when the music […]

Americans are losing billions due to internet crime each year. However, 2020 was a record year for the number of cybercrime victims and the combined financial losses caused by these malicious attacks. According to data […]

Catastrophic disaster can be the result of insecure industrial cybersecurity practices. See six common entry points for attacks, eight cybersecurity precautions for attacks by type, and four steps to improve.

While industry sectors are starting to automate their processes to help increase productivity and efficiency and this requires greater connectivity, which also can expose systems to attack.

The industrial control system (ICS) security community and asset owners need to grow up in 2021. There is near hysteria whenever there is an actual, potential or mythical breach of an ICS, regardless of the […]

Bayshore Networks and GE Digital announced an expansion to their partnership to integrate their solutions to address the growing need to secure industrial and critical infrastructure networks. GE Digital’s OpShield technology will be integrated into […]

Four myths about networking and cybersecurity related to operations technology (OT) systems are highlighted as well as three pillars for securing industrial networks.

According to a Ponemon study, 82% of cybersecurity expenditures go toward post-hoc measures, such as detection, containment and recovery. Only 18% of budgets are invested in prevention – yet financial figures may not be the […]

Simple strategies to achieve the most value from cyber risk assessments. Three strategies for operations technology (OT) teams to avoid while performing assessments are highlighted.

Hackers were as active as ever in 2020 by taking advantage of users’ vulnerabilities and the economic disruption amid the global COVID-19 pandemic. The number of cyberattacks is rising every year, and 2020 saw a […]

Many chief information security officers (CISOs) sacrificed cybersecurity as a major priority in an effort to enable employees to perform remote work when the COVID-19 pandemic hit. Much of the workforce plans on operating this […]

More workers are forced to work remotely due to COVID-19, but cybersecurity prevention and training is lagging behind.

Researchers at the U.S. Army Research Laboratory (ARL) and Towson University are developing a method on compressing network traffic as much as possible without losing the ability to detect and investigate malicious activity.

With increased connectivity between different devices, it’s critical to implement additional cybersecurity measures.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.