Learning Objectives
- A cybersecurity risk assessment can help organizations determine where they need to invest additional measures.
- Companies should have a well-funded cybersecurity team that is disciplined and follows best practices consistently.
- Increased connectivity to business systems has raised cybersecurity protection needs for control systems.
Most process plant automation systems are engineered over a long period to ensure operations are repeatable, reliable, available and safe. However, increased connectivity to business systems has increased exposure of control systems to the internet. Organizations must now consider the cybersecurity implications so industrial automation and control systems remain secure and stable.
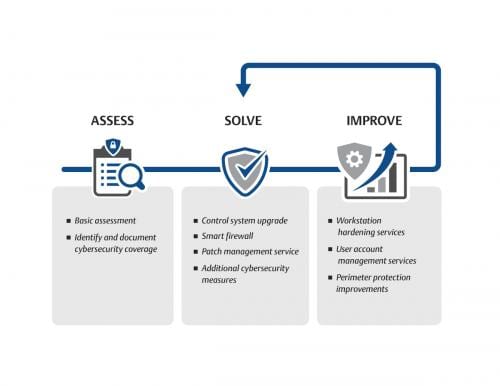
A good starting point is a cybersecurity risk assessment to evaluate gaps in currently implemented strategies and technologies, and to provide a roadmap for identifying, prioritizing, and eliminating vulnerabilities.
There are three common missteps operations technology (OT) teams should be aware of when performing or requesting assessments:
- Assuming their own team already knows and understands all the risks
- Pursuing “magic pill” solutions, and then not acting due to the considerable number of issues
- A lack of prioritization and limited funding.
Organizations that arm themselves against these potential roadblocks can reap the full benefits of a risk assessment. They can drive toward more cybersecure operations and providing the business justification most security-oriented projects lack and asset owners struggle with.
1. Identifying unknown cybersecurity risks, solutions
Cybersecurity is an evolving arms race that may seem overwhelming to an OT team, or even some cyber-experienced information technology (IT) teams. Learning that anti-virus software and a firewall is no longer sufficient protection can be intimidating.
A cyber risk assessment removes the need for an OT team to determine every potential cyber vulnerability in the plant. The assessment can help teams identify, document, prioritize and build a roadmap around the highest threat vulnerabilities. This roadmap provides a guide for creating solutions to quickly provide sufficient security.
Once the assessment is complete, resources created and shared by expert partners can expand knowledge of cybersecurity tactics and techniques directly related to the leading vulnerabilities. Automation providers (as well as other technology providers) typically offer a wide variety of security manuals, secure architecture guidelines, cybersecurity webinars, and continuing education to help OT teams learn, develop, and improve the strategies used to secure critical systems.
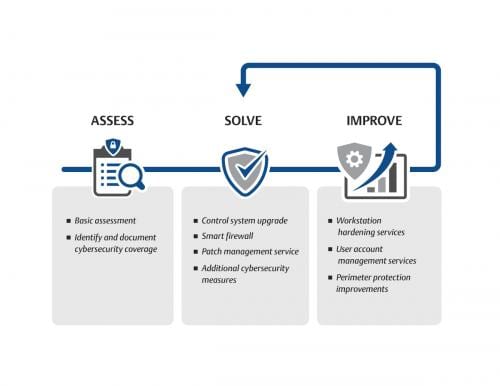
In addition, teams must not assume their operators know all there is to know about cybersecurity. Policies and procedures should be documented, shared, and regularly updated (Figure 1). Personnel need to be trained to operate under new guidelines established after an assessment. New policies will often upset tried-and-true methods operators have become accustomed to. Instead of relying on users’ inherent cybersecurity knowledge, the cybersecurity team should teach them how to perform actions under the new guidelines.
Once the new guidelines have been put in place, the cybersecurity team should evaluate their implementation for success and relevance. The best way to create secure systems and procedures is by periodically review implementations and ensure proper and appropriate practices are in place.
2. Technology alone cannot fix cybersecurity
For every known cybersecurity risk, there is at least one company with the latest and greatest solution, an all-in-one piece of astounding technology. However, when one cuts through the hype, it becomes clear they have varying levels of effectiveness. What’s more: few of these devices or software solutions are designed with control system technology in mind.
Even the best all-in-one solution is not a substitute for a cyber assessment. Regardless of the assessment’s results, a holistic approach supported by a roadmap will always be the best path forward. Technology solutions alone will never remove the need for understanding what’s important to each organization, along with a flexible strategy reflecting operational and business needs.
Though a hot new product might provide a quick fix to an existing or emergent vulnerability, if it interrupts one of the control system core functions, it is unlikely to deliver value over the lifecycle of the automation system, and the organization may face more serious difficulties.
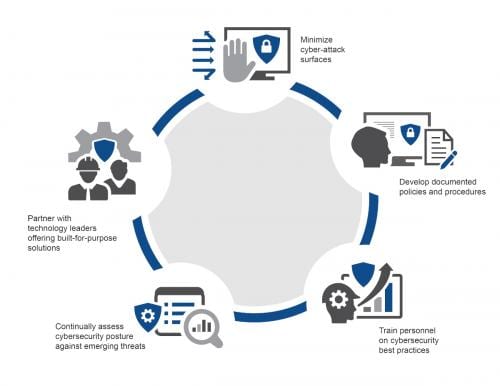
Automation vendors can provide selected cybersecurity solutions certified to work with their systems, and these are the solutions most suited for eliminating vulnerabilities discovered in a cyber risk assessment. Automation vendors develop and test layered cybersecurity solutions using third-party security technologies and accompanying architectures to ascertain which work best with their products. In addition, these approved products are constantly retested and reevaluated to ensure continuing successful operation. As a security posture is reassessed, automation vendors suppliers are also realigning their products to meet new needs.
Some third-party solutions are integrated into industrial control systems (ICSs) so they become part of the automation solution, which allows automation vendors to provide full support in an OT-centric context. In some cases, the third-party provider becomes a strategic partner for the control system supplier so the reference architecture does not impact the core values of the automation system (Figure 2).
Automation system support teams are already well-versed in the security technologies surrounding the control system. This means OT teams can rely on the automation vendor’s single support network to keep any potential downtime to a minimum.
3. Overwhelmed and underfunded cybersecurity departments
The simplest example of inaction is a small department handling information technology (IT) and OT on a limited budget. It is easy for such a team to become overwhelmed because there are so many vulnerabilities that need to be addressed and there’s never enough time, resources or overall funding.
Even large, well-funded organizations need to start with individual solutions and build toward a comprehensive defense-in-depth strategy. Not every problem needs to be fixed at once. A good cybersecurity risk assessment will create a prioritized roadmap to build the defense layers that will close gaps over time and at a reasonable cost.
Another important strategy is reliance on a trusted partner to perform or help with assessments. Partner organizations have strategies and tools to help make the case for cybersecurity enhancements to management, justifying the investment by examining information regarding the cost of cybersecurity breaches.
How to begin with a cyber risk assessment
Taking concrete steps in response to a cyber risk assessment is not as daunting as it may seem. While it is true new cybersecurity risks may appear in the future, these risks are not as well known or as likely to be exploited as old risks that are covered by security patches, hotfixes and upgrades.
An organization is more likely to be targeted using an old exploit they never patched than by a new, freshly discovered vulnerability simply because more attackers will have tools to attack older vulnerabilities in their arsenal. These are the vulnerabilities most likely to be discovered with an assessment and deterred by basic defense layers.
A defense-in-depth strategy starts with a good context definition so each protection layer can be properly designed and then prioritized against available resources. A cyber risk assessment helps build a good context definition appropriate for the organization’s unique needs.
Being proactive with a cyber risk assessment also can help OT teams ensure any security measures don’t impact operations. If OT waits too long to identify and pursue solutions suited to operations, IT may step in and provide its own solutions without understanding the operations’ team unique needs.
When risks are assessed and solutions are deployed appropriately, cybersecurity becomes a bridge between IT and OT that mutually benefits both groups. This is particularly valuable at a time when organizations are forced to operate leaner and remotely to ensure operations and business continuity.
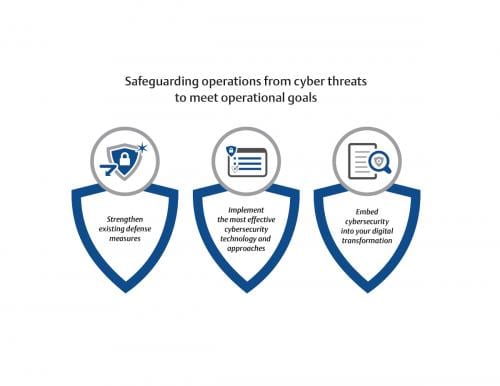
Invest in a cyber assessment to secure automation systems
Increased connectivity to business systems has raised cybersecurity protection needs for control systems. Starting with a cybersecurity assessment to identify where your organization is in its journey prepares personnel to write policies and procedures to better secure automation systems. The time invested in defining your specific context will help you establish defense layers to meet the today’s needs (Figure 3).
A comprehensive cyber risk assessment also will help build the roadmap that – as evidenced by recent events – is essential to preparing for the unexpected needs of the future.
Alexandre Peixoto, DeltaV product marketing manager; Rick Gorskie, global sales manager for cybersecurity, Emerson. Edited by Chris Vavra, associate editor, Control Engineering, CFE Media and Technology, cvavra@cfemedia.com.
MORE ANSWERS
Keywords: cybersecurity, control system, operations technology
A cybersecurity risk assessment can help organizations determine where they need to invest additional measures.
Companies should have a well-funded cybersecurity team that is disciplined and follows best practices consistently.
Increased connectivity to business systems has raised cybersecurity protection needs for control systems.
CONSIDER THIS
What cybersecurity challenges does your company face and how are they being addressed?
Original content can be found at Control Engineering.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.