When establishing and testing a brand new cybersecurity program, it can be difficult to know exactly which steps are reasonable to take and when to take them. In this blog, we will talk about when to begin thinking about a penetration test, and considerations to make when you’ve decided it’s time to order one for your industrial control systems (ICS) and operational technology (OT) environments.
When is it time to pentest?
Building a cybersecurity program is a marathon, not a sprint. It can be exciting finally getting to the point of ordering a penetration test, but testing should be considered a late-stage maturity activity. In other words, system owners should make sure that they have the basic building blocks of a cybersecurity program in place before considering a penetration test.
Dragos Professional Services clients have typically gone through a process of architecture review and site assessment prior to ordering a network penetration test. This is done to ensure that the conceptual framework for network architecture is sound. When conducting an architecture review, it’s useful to ask for certain documents including network topology, incident response plans, recovery plans and firewall configurations. Our group then conducts interviews with client staff to better understand the makeup of the existing security program.
The follow-on site assessment explores the ground truth, which helps discover discrepancies between what is on paper and what is reality within the facility. Nothing helps expose the good, the bad and the ugly of security operations like walking through the facility where those operations take place. This exercise typically results in additional findings that should be remediated prior to any penetration testing.
Once these exercises have been completed and all the findings have been addressed, it’s time to think about testing the mitigations put in place after the last two rounds of exercises. Testing these mitigations should be a primary goal of the penetration test. Of course, there are other ways to get to the conclusion that it’s time to conduct a penetration test. However, if a system owner comes to the conclusion that it’s time to order a test, there are some things to consider when it comes to what kind of test to ask for.
Pentesting strategy
When it’s time to discuss a penetration test with a vendor, it helps to understand a few basic pentesting strategies. In terms of pentesting strategy, there are three broad approaches that are typically consulted:
When Dragos performs an industrial penetration test, we work around a set of limitations that help guide our approach to testing. One of these limitations is time. A standard Dragos pentest takes place in the span of a standard 40-hour work week. While most adversaries do not have this time limitation and can “dwell” for extended periods of time to gather information and research their target, pentesters do not have this advantage. Therefore, our goal is to simulate a breach in advanced stages. We call this an “assumed breach” test.
In an assumed breach test, system owners consider a scenario where their network has already been breached to some extent. This allows system owners to consider questions related to how far an attacker could get and how much damage they could do once they’ve managed to gain access to the owner’s network. We find that this approach delivers the most beneficial outcomes considering the limitation of time.
Whatever strategy a system owner decides on, they should also carefully consider the vendor they choose and how much experience their chosen vendor has in ICS penetration testing specifically. Special considerations should be made in ICS environments with respect to network availability that not all penetration testing providers will respect, or even be aware of.
How an OT pentest differs
No two penetration tests are the same. Different goals, different strategies and different network placement all contribute to unique penetration testing experiences. It’s possible that readers of this post may have experience with IT pentests that reflects this fact, however, there are dramatic differences between IT and OT penetration tests.
Because OT penetration tests need to take additional precautions to prioritize availability during pentests against production ICS networks, certain tools and techniques are considered high-risk, and accordingly are not used because of the stability risk they pose to our clients. We do recognize that this creates a trade-off between a thorough test and a sanitary test. One way that we deal with this trade-off is by checking exploitability before committing to using the exploit.
This method allows us to use a “defanged” exploit, or an exploit that both reduces the risk of using the “fanged” (full exploit technique) method, and also allows us to continue testing. This is not something that is often seen in IT penetration testing, but it is something we get a great deal of use out of in ICS pentesting.
The following graphic provides a simplified overview of the penetration testing process conducted by Dragos. To view the process in more detail, see our infographic, Anatomy of a Penetration Test, here.
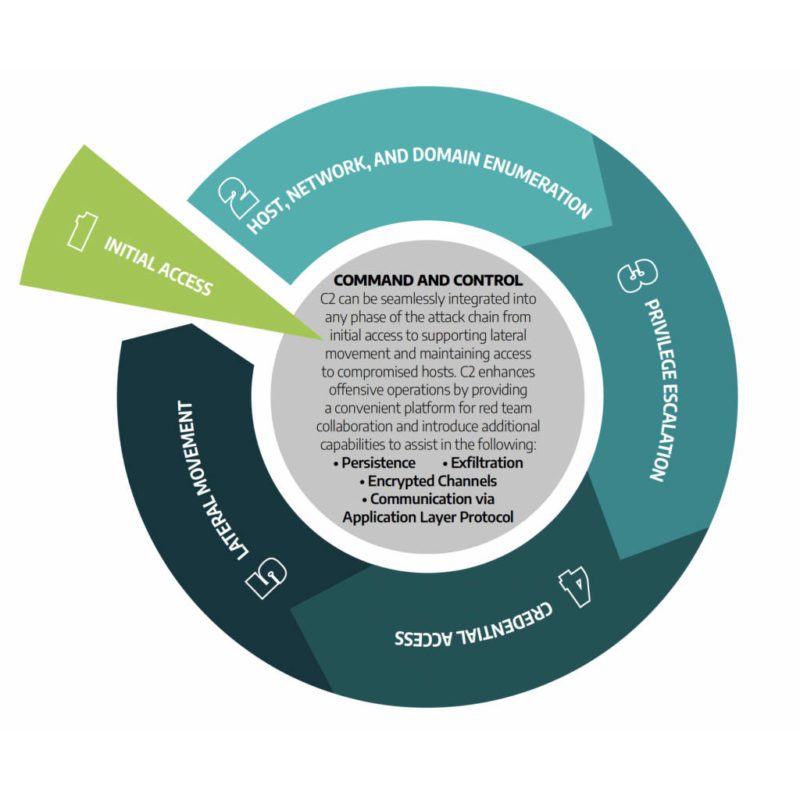
Impacts and outcomes
Another area where IT pentesting differs from ICS pentesting is in the outcomes we hope to achieve. After a penetration test, clients can expect to have a realistic picture of what a breach against their networks would look like.
They can know how successful a professional team of hackers would be against the protections and mitigations built into the network. Having this information can be used to directly inform changes and security improvements, which may not be obvious from on-paper exercises alone.
Not only does a penetration test help illuminate what pathways an attacker may take if they achieve network access, but clients can also expect to understand what sorts of impacts may result from network compromise, as well. When it comes to impacts, we want to identify pathways that create impacts to ICS operations such as:
- Loss of view
- Loss of control
- Loss of confidence
- Impairing process control
- Inhibiting response function
All of the above can pose obstacles to operational continuity and are often not outcomes clients would expect to see on an exclusive test of their IT systems.
In summary
Penetration testing can significantly improve the security posture of a growing cybersecurity program, and there are many things to consider. Maturity is an investment, and ensuring a cybersecurity investment through testing is highly rewarding and illuminating to system owners who are prepared.
Original content can be found at Dragos.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








