
Throwback Attack: Ireland ransomware attack costs HSE $83 million
HSE has been described as one of the most significant digital assaults on a health care system in recent memory.

HSE has been described as one of the most significant digital assaults on a health care system in recent memory.

As nation-state attacks continue to rise, the energy sector must continue to security its assets from threat actors.

In 2012, the OilRig cyber espionage group began targeting the oil and gas industry and other critical infrastructure in the Middle East.
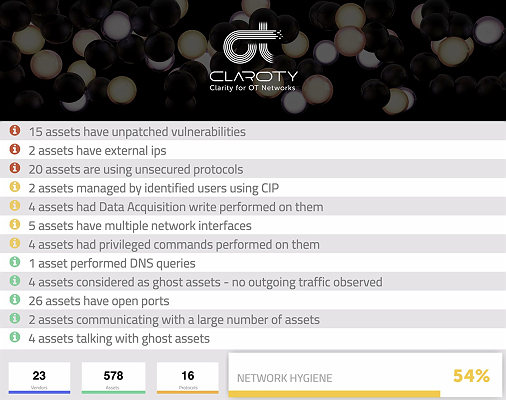
The Claroty Platform extracts critical data by monitoring all network communication, establishing a high-fidelity baseline model for rapid detection of anomalous behavior. Combining native OT knowledge with advanced models and algorithms, Claroty produces context-rich alerts […]

The top 5 from April 2023 covered the Biden administration’s National Cyber Strategy, cyber simulation training and the risks of connectivity.

From the first day of the 2023 RSA Conference, it was clear that the cybersecurity risks of ChatGPT would be a popular topic.

Annual phishing report highlights new phishing campaigns resulting from the rise of AI platforms urges organizations to adopt a zero trust.

The Davis-Besse nuclear plant fell victim to the Slammer worm, showing the consequences of cyberattacks on nuclear facilities.

The ICS Pulse Podcast talked to Ben Miller of Dragos about the Year in Review report and other cybersecurity trends in the industry.

To realize maximum value in industrial environments, seamless and transparent connectivity is needed from the plant floor to the cloud.

HSE has been described as one of the most significant digital assaults on a health care system in recent memory.

As nation-state attacks continue to rise, the energy sector must continue to security its assets from threat actors.

In 2012, the OilRig cyber espionage group began targeting the oil and gas industry and other critical infrastructure in the Middle East.

The Claroty Platform extracts critical data by monitoring all network communication, establishing a high-fidelity baseline model for rapid detection of anomalous behavior. Combining native OT knowledge with advanced models and algorithms, Claroty produces context-rich alerts […]

The top 5 from April 2023 covered the Biden administration’s National Cyber Strategy, cyber simulation training and the risks of connectivity.

From the first day of the 2023 RSA Conference, it was clear that the cybersecurity risks of ChatGPT would be a popular topic.

Annual phishing report highlights new phishing campaigns resulting from the rise of AI platforms urges organizations to adopt a zero trust.

The Davis-Besse nuclear plant fell victim to the Slammer worm, showing the consequences of cyberattacks on nuclear facilities.

The ICS Pulse Podcast talked to Ben Miller of Dragos about the Year in Review report and other cybersecurity trends in the industry.

To realize maximum value in industrial environments, seamless and transparent connectivity is needed from the plant floor to the cloud.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.