New study finds 60% increase in AI-driven phishing attacks

Annual ThreatLabz Phishing Report unveils rapidly evolving phishing landscape, underlining the need to adopt a zero-trust architecture.
Cybersecurity services market predicted to grow at 10.7% from 2023 to 2032

According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.
Use of AI/ML tools skyrocketed nearly 600% over the last year, putting enterprises at risk

ThreatLabz new AI report reveals enterprises are sharing 569 TB of data to AI/ML tools, stressing the need for better data security.
Malware Profile: VOLTZITE targets industrial organizations

In their 2023 year in review, Dragos identified a new threat group, VOLTZITE, that has been targeting industrial organizations since 2021.
Five findings in 2023’s ICS cybersecurity data

In 2019, 38% of respondents considered threats to ICS as “high,” and grew to 40% in 2021, 41% in 2022 and 44% in 2023
Operating for zero trust
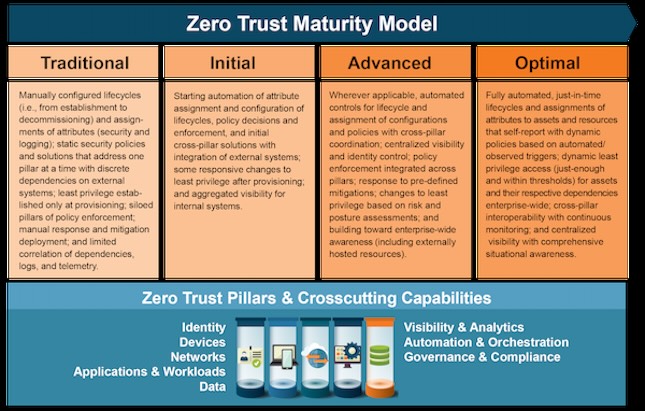
A zero trust mentality involves decisions across multiple pillars and organizational variables, informing the organization’s decisions.
The Ethical Considerations of AI in Cybersecurity: Ethan Schmertzler, Dispel, ICS Pulse Podcast

Manufacturers are using AI in cybersecurity to help with efficiency gains and cost reduction. But what are the ethical ramifications?
Developing and executing a fully informed OT threat hunt

Executing a threat hunt is a major topic in security operations discussions and becomes even more so when plans are made to traverse IT & OT.
Top 5 ICS Pulse Articles: February 2024

ICSP’s top 5 articles from February covered the benefits of AI and a major cybersecurity framework update from NIST.
Dragos Year in Review reports rise in geopolitically driven attacks, ransomware and threat groups

The Dragos Year in Review report shows a rise in geopolitically driven attacks, ransomware and threat groups in OT cybersecurity.




