
Cybersecurity services market predicted to grow at 10.7% from 2023 to 2032
According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.

According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.

ODVA, governing body for EtherNet/IP, DeviceNet and other protocols, stepped up cybersecurity with single-pair Ethernet (SPE) capabilities.

In 2019, 38% of respondents considered threats to ICS as “high,” and grew to 40% in 2021, 41% in 2022 and 44% in 2023
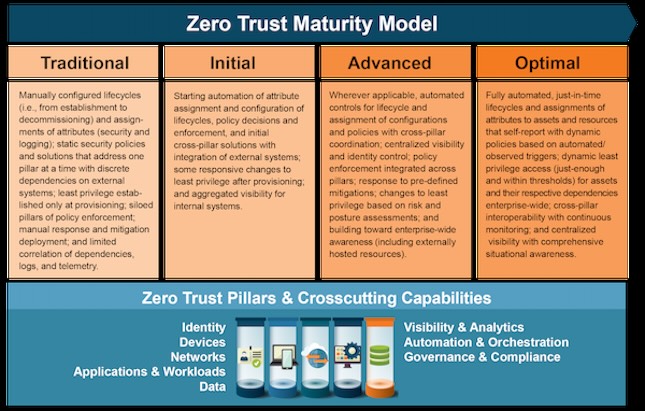
A zero trust mentality involves decisions across multiple pillars and organizational variables, informing the organization’s decisions.

Executing a threat hunt is a major topic in security operations discussions and becomes even more so when plans are made to traverse IT & OT.

On Oct. 31, 2023, version 14 of the MITRE ATT&CK framework was released. It’s designed to bolster cloud security with 18 new techniques.

Recently, Industrial Cybersecurity Pulse spoke with Leah Dodson of Nextlink Labs about integrating cybersecurity into products.
NIST releases version 2.0 of its cybersecurity framework, the first major update since its creation in 2014.

A big part safeguarding critical infrastructure from cyber threats revolves around cyber insurance and the cost to protect systems.

Industrial companies face a delicate balancing act between driving operational efficiency and defending against cyberattacks.

According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.

ODVA, governing body for EtherNet/IP, DeviceNet and other protocols, stepped up cybersecurity with single-pair Ethernet (SPE) capabilities.

In 2019, 38% of respondents considered threats to ICS as “high,” and grew to 40% in 2021, 41% in 2022 and 44% in 2023

A zero trust mentality involves decisions across multiple pillars and organizational variables, informing the organization’s decisions.

Executing a threat hunt is a major topic in security operations discussions and becomes even more so when plans are made to traverse IT & OT.

On Oct. 31, 2023, version 14 of the MITRE ATT&CK framework was released. It’s designed to bolster cloud security with 18 new techniques.

Recently, Industrial Cybersecurity Pulse spoke with Leah Dodson of Nextlink Labs about integrating cybersecurity into products.

NIST releases version 2.0 of its cybersecurity framework, the first major update since its creation in 2014.

A big part safeguarding critical infrastructure from cyber threats revolves around cyber insurance and the cost to protect systems.

Industrial companies face a delicate balancing act between driving operational efficiency and defending against cyberattacks.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.