
The impact of AI on cybersecurity: Ethan Schmertzler, Dispel, ICS Pulse Podcast
Ethan Schmertzler of Dispel discusses how new advances in AI are impacting industrial cybersecurity and social engineering attacks.
Home | Strategies | Page 2

Ethan Schmertzler of Dispel discusses how new advances in AI are impacting industrial cybersecurity and social engineering attacks.
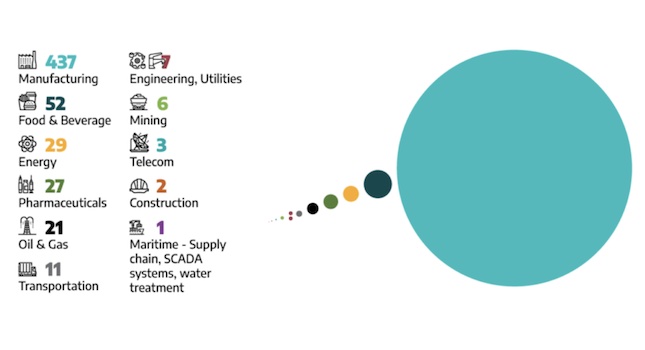
The Dragos 2023 OT Cybersecurity Year in Review has lessons and strategies, guiding you to a more secure industrial future.

Recently, the ICS Pulse talked to Leah Dodson of Nextlink Labs about the importance of communication in cybersecurity.

Understanding the value of government moves toward secure default configuration, insecure by design and secure by design.

Our top 5 pieces from November covered everything from the impact of large language models to increased holiday threats.

Our top 5 articles of October covered everything from avoiding scams to cyber-informed engineering to building stronger cyber habits.
Rockwell Automation and Dragos look at how executives and boards are addressing the state of manufacturing cybersecurity.

How can cybersecurity professionals emphasize the importance of OT cybersecurity to ICS boards and senior leadership?

Moty Kanias talks about why it’s essential to move toward cyber prevention and how AI is going to impact everything.

The top 5 from September 2023 covered how to cut through cybersecurity marketing and why security testing should be part of your strategy.

Ethan Schmertzler of Dispel discusses how new advances in AI are impacting industrial cybersecurity and social engineering attacks.

The Dragos 2023 OT Cybersecurity Year in Review has lessons and strategies, guiding you to a more secure industrial future.

Recently, the ICS Pulse talked to Leah Dodson of Nextlink Labs about the importance of communication in cybersecurity.

Understanding the value of government moves toward secure default configuration, insecure by design and secure by design.

Our top 5 pieces from November covered everything from the impact of large language models to increased holiday threats.

Our top 5 articles of October covered everything from avoiding scams to cyber-informed engineering to building stronger cyber habits.

Rockwell Automation and Dragos look at how executives and boards are addressing the state of manufacturing cybersecurity.

How can cybersecurity professionals emphasize the importance of OT cybersecurity to ICS boards and senior leadership?

Moty Kanias talks about why it’s essential to move toward cyber prevention and how AI is going to impact everything.

The top 5 from September 2023 covered how to cut through cybersecurity marketing and why security testing should be part of your strategy.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.