
The role of CVEs and SBOMS in protecting MES: ICS Pulse Podcast, Sung Kim, iBase-t
In a rapidly digitizing world, the importance of cybersecurity in safeguarding MES is becoming increasingly crucial.
Home | Strategies | Page 4

In a rapidly digitizing world, the importance of cybersecurity in safeguarding MES is becoming increasingly crucial.

The top 5 articles from June 2023 covered zero-trust architecture, protecting MES and driving Industry 4.0 through IT/OT convergence.
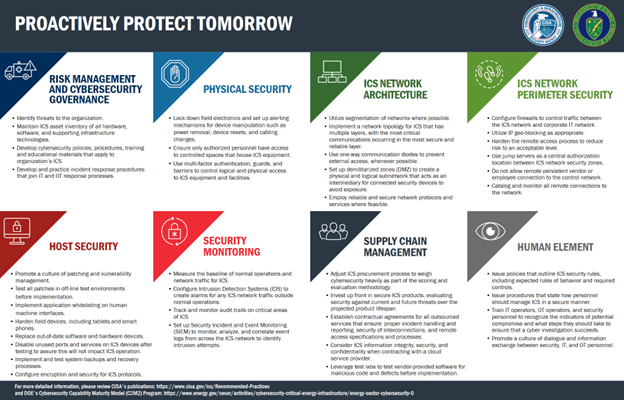
Analysis of the ICS advisory supports the development of appropriate strategies for their environments based on real-world risks.

A company’s ability to protect OT and critical infrastructure will be determined by how well it can cultivate cybersecurity talent.

Unscheduled and unplanned downtime on the plant floor can have significant consequences for manufacturing organizations.

Each new internet-connected device carries with it the burden of joining your network in accordance with latest cybersecurity practices.

Critical infrastructure is under attack. ICSP talked to Victor Atkins of 1898 and Co. about protecting critical infrastructure.

By identifying vulnerable suppliers and mitigating supply chain risk, a company can take proactive steps to protect their cybersecurity.

Manufacturing is the most targeted industry in the world for cyberattacks, and midsized manufacturers must have appropriate protections.
Learn how to prevent ransomware in OT/ICS industrial environments with 5 key steps to reduce the risk of an attack.

In a rapidly digitizing world, the importance of cybersecurity in safeguarding MES is becoming increasingly crucial.

The top 5 articles from June 2023 covered zero-trust architecture, protecting MES and driving Industry 4.0 through IT/OT convergence.

Analysis of the ICS advisory supports the development of appropriate strategies for their environments based on real-world risks.

A company’s ability to protect OT and critical infrastructure will be determined by how well it can cultivate cybersecurity talent.

Unscheduled and unplanned downtime on the plant floor can have significant consequences for manufacturing organizations.

Each new internet-connected device carries with it the burden of joining your network in accordance with latest cybersecurity practices.

Critical infrastructure is under attack. ICSP talked to Victor Atkins of 1898 and Co. about protecting critical infrastructure.

By identifying vulnerable suppliers and mitigating supply chain risk, a company can take proactive steps to protect their cybersecurity.

Manufacturing is the most targeted industry in the world for cyberattacks, and midsized manufacturers must have appropriate protections.

Learn how to prevent ransomware in OT/ICS industrial environments with 5 key steps to reduce the risk of an attack.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.