
Tabletop Exercises: ICS Pulse Podcast Series, Dino Busalachi, Velta Technology
How do you get your organization cybersecurity prepared? Tabletop exercises are a great way to help build your incident response plan.
Home | Strategies | Page 5

How do you get your organization cybersecurity prepared? Tabletop exercises are a great way to help build your incident response plan.

Asset visibility is the foundation of most cybersecurity activities, but many companies struggle to understand their own infrastructure.

Analysts at GlobalData offer their views of what 2023 holds for cybersecurity, including zero-trust cybersecurity.

Your ICS equipment could be at risk of shutdown on March 14, 2023, with the Microsoft DCOM hardening patch.

Critical infrastructure cybersecurity insights Critical infrastructure is very important to society and maintaining the basic needs of human life in modern times. Because of this, there is a need for critical infrastructure cybersecurity to protect […]

Endpoint security is the process of identifying, detecting, protecting and responding to cybersecurity threats at the device level.

Cyber criminals are experts at finding ways into protected systems and exploiting the information they find.

As the world becomes more and more connected, managing and mitigating cybersecurity risk with a SOC is a step toward cyber cleanliness.
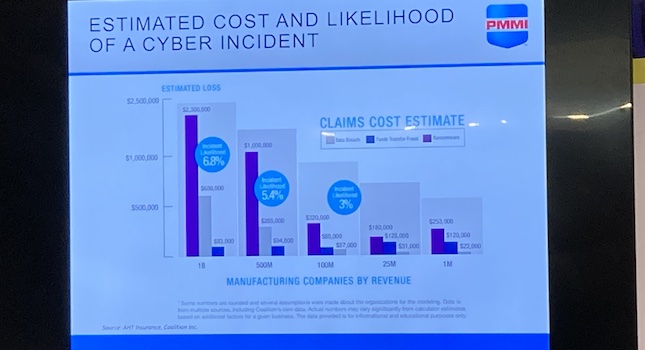
Defending and responding to cybersecurity breaches is an important part of gaining new and better security practices.

David Masson, Sam May and Bryan Bennett discuss the importance of having a business continuity plan in the event of a cyberattack.

How do you get your organization cybersecurity prepared? Tabletop exercises are a great way to help build your incident response plan.

Asset visibility is the foundation of most cybersecurity activities, but many companies struggle to understand their own infrastructure.

Analysts at GlobalData offer their views of what 2023 holds for cybersecurity, including zero-trust cybersecurity.

Your ICS equipment could be at risk of shutdown on March 14, 2023, with the Microsoft DCOM hardening patch.

Critical infrastructure cybersecurity insights Critical infrastructure is very important to society and maintaining the basic needs of human life in modern times. Because of this, there is a need for critical infrastructure cybersecurity to protect […]

Endpoint security is the process of identifying, detecting, protecting and responding to cybersecurity threats at the device level.

Cyber criminals are experts at finding ways into protected systems and exploiting the information they find.

As the world becomes more and more connected, managing and mitigating cybersecurity risk with a SOC is a step toward cyber cleanliness.

Defending and responding to cybersecurity breaches is an important part of gaining new and better security practices.

David Masson, Sam May and Bryan Bennett discuss the importance of having a business continuity plan in the event of a cyberattack.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.