How to achieve remote automation success

The world we live in is not the same world we once knew. Unprecedented global events and new technological advances are forcing manufacturers to adapt and work in an ever-evolving, more remote business environment. Change […]
Evaluating 2021 cyber threat landscape trends

As companies continue to adjust to the ever-evolving new normal in 2021, there will undoubtedly be additional shifts in work environments, internet usage, and the general status quo. With this in mind, Fortinet’s FortiGuard Labs’ Derek Manky […]
Cybersecurity Maturity: CEO Interview Series, Pranav Patel, ResiliAnt

Cyberattacks in manufacturing are on the rise. So how should the industry respond to this increasing threat? It takes organization, buy-in and cybersecurity maturity. Awareness of the need for cybersecurity has been growing, as attacks […]
Industrial control system (ICS) cybersecurity advice, best practices
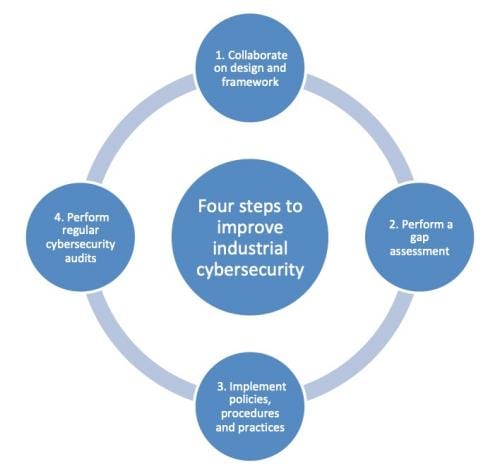
Catastrophic disaster can be the result of insecure industrial cybersecurity practices. See six common entry points for attacks, eight cybersecurity precautions for attacks by type, and four steps to improve.
Manufacturers need to prepare for cybersecurity threats

While industry sectors are starting to automate their processes to help increase productivity and efficiency and this requires greater connectivity, which also can expose systems to attack.
ICS cybersecurity company appoints CEO

Mission Secure, an industrial control system (ICS) cybersecurity technology company, appointed John Adams as Chief Executive Officer (CEO). He will succeed David Drescher, who will remain with the board of directors. “A generational shift has […]
The challenge of securing all network edges

Hybrid networks, multi-cloud, Internet of Things (IoT), remote work and digital innovations are all driving more distributed networks and a much more expansive attack surface. The network perimeter that used to be so clearly defined now extends […]
Understand the cyber-attack lifecycle

A cyber kill chain provides a model for understanding the lifecycle of a cyber attack and helps those involved with critical infrastructure improve cybersecurity policies, technologies, training, and industrial control system (ICS) design. Learn 8 steps of one model.
How to protect embedded systems in OT cybersecurity

Many wonder where to start when attempting to protect embedded systems in OT cybersecurity? Here are two pieces of information that can help guide you when understanding cybersecurity issues for embedded devices and the never-ending […]
Protecting the chip industry supply chain from cyberattacks

Intellectual property (IP) is the lifeblood of today’s globally integrated microelectronics supply chain. Protecting confidential information is vital to electronics companies around the world. The industry’s central role in ensuring the national security and economic […]




