Ransomware attacks have skyrocketed in recent years. There is no sign of slowing down despite the increase in spending and risk awareness. Cybersecurity personnel often feel burned-out and relatively ineffective. They are constantly firefighting, and the reason is clear – they are dealing with a complex system in modern enterprises with many uncontrolled and unknown variables. It requires a different approach to problem-solving.
Cybersecurity teams are now desperately searching for their next shiny tech-tool that can allow them to tackle these fast-surfacing challenges effectively. Is there one? The tech vendors would say, “yes.” In fact, we’d gladly sell them one too. Is that the right answer, though?
As people often say, “What got you here won’t get you there.” In many organizations, cybersecurity decisions have either been made or heavily influenced by network engineering teams. With the emergence of chief information security officers (CISO), the scope has expanded to include broader information technology (IT) operational processes involving applications and IT endpoints; they have improved security processes with the implementation of SIEM and SOAR. CISO organizations have brought strategic excellence in cybersecurity by assessing technical needs, running tech procurement processes, and implementing architected solutions.
Whether businesses have gained full value from their technical investments is yet to be determined. Furthermore, the value of tech-focused, siloed approach is also questionable when we know that 86% of cyber-incidents involved human-factors such as errors and misuses, and about 70% of incidents originated from internal actors and partner organizations. Hence, organizations now must focus on operational excellence and expand the scope of cybersecurity to cover all business processes as opposed to only IT-centric processes.
The following table covers general observations on the current state of cybersecurity and gaps. The assessment framework considers (1) technology or breadth of controls, (2) processes and (3) leadership.
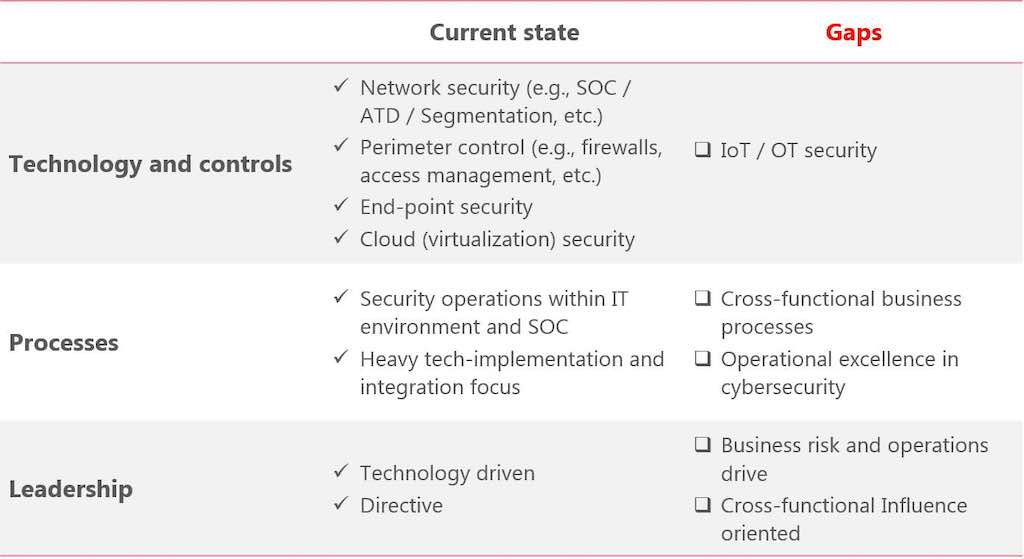
While much progress has been made, the next phase of cybersecurity requires a focus on maturity. Maturing cybersecurity in organizations is more about processes and leadership than the implementation of new tools. It calls for a programmatic approach with cross-functional engagement.
– This article originally appeared on Meditechsafe’s website. Meditechsafe is a CFE Media content partner.
Original content can be found at www.meditechsafe.com.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








