Cybersecurity in the industrial sector is changing, and the need to look toward the future is ever present, but it is also essential to examine the past and learn from it. Now, threat actors are becoming more aware about what the industry does and seeing the value of targeting manufacturing companies, said Robert M. Lee, CEO of Dragos, in his presentation “Manufacturing Is Both a Cybersecurity Target and a Vector” at the Fortniet OT Symposium on Aug. 24.
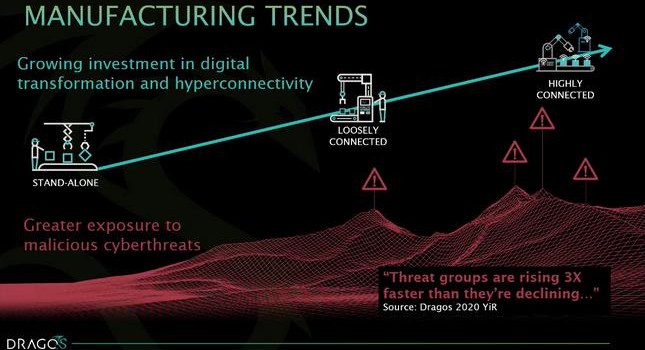
Modern companies are more digital and connected than ever before. But networks and industrial operations systems have been connected in ways beyond anyone’s understanding for a long time. What does it mean that threats are always evolving, as well? “As we look more in the industry, we find more,” Lee said, and that’s ultimately a sign of maturity. As manufacturers and industrial companies take a deeper look into OT networks, they find risks that have stayed over time.
One of the trends Dragos has found is that improved connectivity makes systems more susceptible to cyberthreats. They have tracked different threat actor groups to see if there are any patterns to how they come into existence and then fade out. Good growth, in the threat landscape, would be having more groups fall off than arrive on the scene. When one group disappears, it would be manageable if only one to two groups replaced it. However, according to a Dragos study, “threat groups are rising three times faster than they’re declining,” which means when one group falls off, another three pop up.
How to advise on vulnerabilities
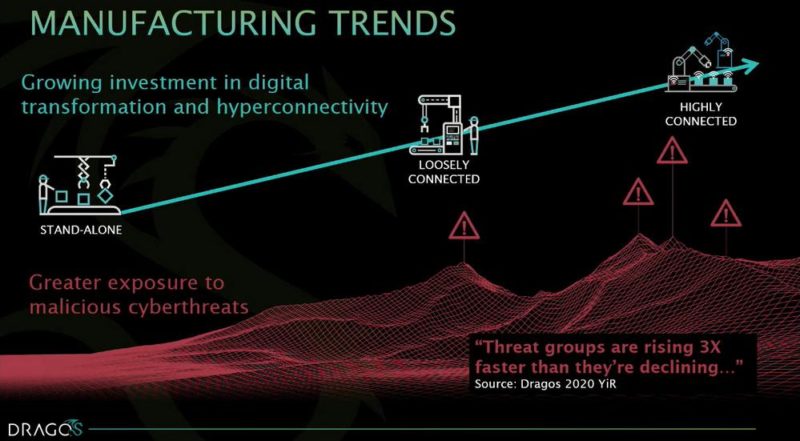
In the manufacturing sector, there isn’t necessarily a mature approach to vulnerabilities because regulations tend to overemphasize vulnerabilities, Lee said. Common challenges are common vulnerabilities and exposures (CVEs) that contain errors, having a patch but no alternative mitigation, advisories with incorrect data, advisories with no patch, and advisories with no patch and no alternative mitigation. What this means is that people see a problem but don’t always have a direct solution.
There are a lot of different vulnerabilities in systems, and sometimes that is by design. What people need to look out for are the unique ways that vulnerabilities in systems give access to adversaries. The most important strategy, Lee said, is to understand when to stop looking for vulnerabilities and focus on the ones that really matter. “The type of vulnerability that a threat attacker is looking for is unauthenticated access to remotely exploit and remotely update firmware,” Lee said.
One of the most important ways to combat vulnerabilities is by creating an informed community. Having realistic expectations of addressing vulnerabilities also helps the process move in the right direction. Placing blame on a certain department is not going to help; it’s more important to understand that not every vulnerability is going to be addressed and that’s OK. Having realistic expectations on the back end also helps.
“You can get to a smaller set of TTPs (tactics, techniques and procedures), and that can get you a defensible and scalable detection strategy versus being aware of every single anomaly or every single indicator that ever happens in your environment,” said Lee.
Threat groups
There are about 15 threat activity groups Dragos is tracking that target industrial companies around the world, and six of them explicitly target manufacturing. When these groups are targeting a certain company, that company needs to take immediate action. Dragos calls these six groups Wassonite, Vanadinite, Covellite, Xenotime, Talonite and Kamacite.
Wassonite, in particular, has been tracked since November 2019. What Dragos found is that their malware is information technology (IT)-based, which means that if an operational technology (OT) team sees it, they generally assume it is regular malware and nothing special. However, the point isn’t to focus on the malware itself, but on the fact that the company has a human threat.
A company has to think about what the intentions of the attackers are and what kind of impact they could have on the company as a whole. For example, Dragos found that Wassonite was focused on intellectual property, such as the way a company does business. There is competitive value for these insights. The threat is in the adversary and what they do, not the specific malware they use.
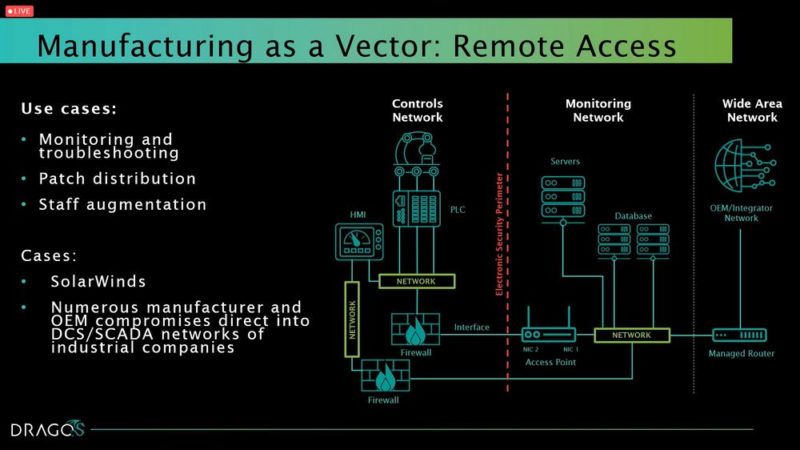
In another example, Solar Winds, “I think we underreacted and we got extremely fortunate that a strategic adversary did not want to do something disruptive because they would have been able to do something disruptive across major portions of our infrastructure if they had so desired,” said Lee. There is a reason why concerns are so high now. The stakes are higher.
Reduce cyberthreats
At the executive level, people tend to focus on IT cybersecurity. For a long time, people thought OT networks weren’t connected to other networks, so they focused all of their efforts on the IT side. However, to reduce risk as a whole, companies need to focus on all of the departments, not just IT. Giving resources to the exposed operation side will allow people to address the risks they face, as well.
“Tons of plants that are getting hit from ransomware just on the fact that we didn’t know better or we did a lot of preventative actions, and then we walked away,” said Lee. What people didn’t think about was the fact that the prevention taken in the beginning, such as firewalls, can atrophy over time.
“Just by having not only better network visibility but also understanding what’s going on in IT and OT, you can get a pretty good view of some of these actors and how they’ve compromised these organizations for weeks or months before ransomware strikes,” Lee said. One assumption people make is that once they recognize they have been hit by ransomware, they don’t think they have time to combat it. However, there are weeks or months of opportunity to detect any threat actors in a company’s system.
“Everybody is going to get breached. Dragos as a security company one day will be breached. The idea that we can just not have being breached as a topic in the community is silly. You will get breached, but how do you respond to it, and what are the expectations and what transparency do you give to your customers to help them make their decisions that’s what you get measured on,” Lee said.
Some of Lee’s recommendations are to restrict access and account management. For example, limit the number of domain administrators, and separate all of the administrators into their own organizational units (OUs). Develop cyberattack response plans, and have them be more than one paragraph. People should know how to respond in an emergency in the most efficient way. Verify that third-party connections and OT interactions are monitored, and take an encompassing approach for visibility into OT environments so there isn’t a gap in monitoring.
Transparency, prevention and response are all key elements that should evolve with the evolving threats. Having a cyberattack target a company isn’t the end of the world, but not having the appropriate responses would be.
For more from the Fortinet OT Symposium, check out the article: Secure device onboarding for manufacturing supply chain.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.