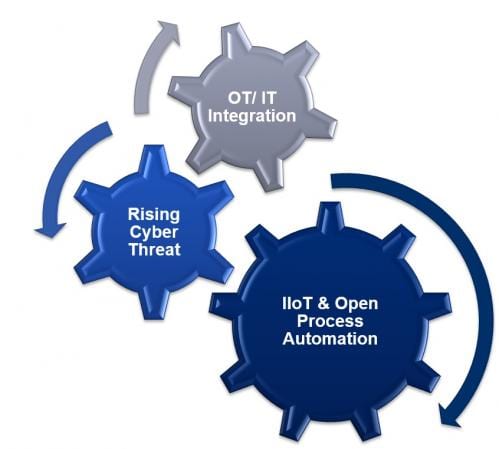
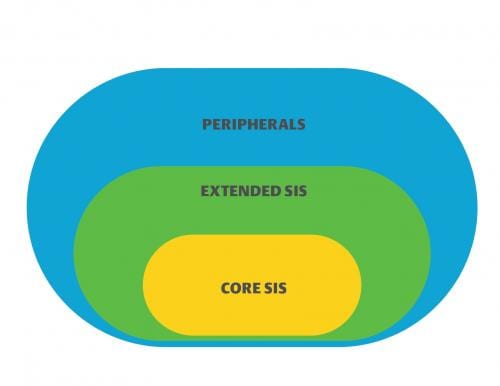
Throwback Attack: WannaCry ransomware takes Renault-Nissan plants offline
In 2017, auto manufacturer Renault-Nissan became one of many organizations around the world to fall victim to the WannaCry ransomware. While WannaCry was effectively halted within a few days of its discovery, it was one […]