The ISA/IEC 62443 cybersecurity documents contain a lot of guidance that easily overwhelms or confuses people when unpacking its components. It covers a range of topics including how to:
- Build a Cybersecurity Management System (CSMS)
- Structure industrial cybersecurity assessments (while not replacing actual ISA 84, for example)
- Define security requirements for several Foundational Requirement (FR) areas
- Define, determine, apply and evaluate target Security Levels (SL).
This article, though, is not to rehash those topics – those can be found in this ISA 62443 all-in-one guide – but, instead, this article aims to help asset owners, integrators and customers understand how to begin a cybersecurity program to improve overall maturity against the elements of the IEC 62443 standard.
In the information technology (IT) cybersecurity world, there is a plethora of frameworks and education. But in operational technology (OT) cybersecurity, it is paralyzing to understand and properly implement meaningful security. The good news is that it can be done safely in a way that considers both enterprise/IT and OT/ICS audiences via a phased and pragmatic approach.
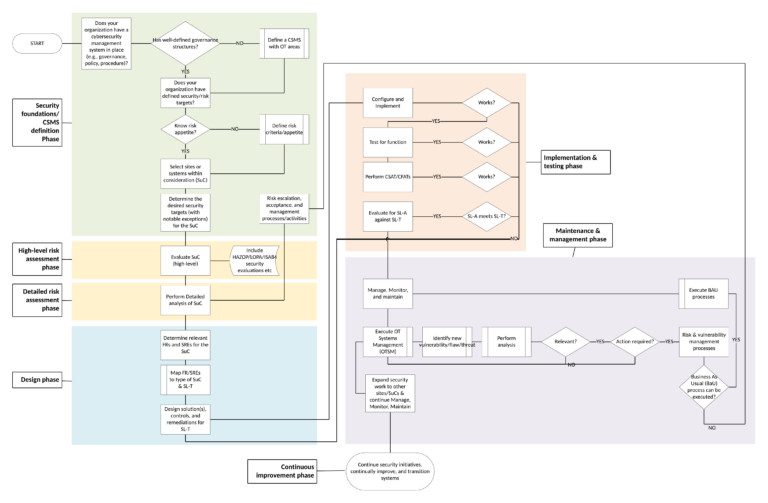
Five steps to build an ICS cybersecurity program using IEC 62443 standards
- Security foundations – Cybersecurity management system (CSMS) definition
- Develop the objectives, policies, metrics and governance for the overall ICS security program
- Risk assessment
- Develop a detailed view of risks at each facility, endpoint, network and user
- Design of security program
- Prioritize a set of initiatives to reduce risks across each area to achieve the security objectives established in Phase 1
- Implementation and testing
- Execute the plan and conduct robust testing of solutions, standalone as well as in concert with each other
- Maintenance and continuous improvement
- Ensure controls and execution are monitored and tracked and improvement occurs over time
For audiences that are more visual, the following diagram illustrates the five phases aligned for IEC 62443 compatibility:
Key takeaways from the standards
- Achieving IACS cybersecurity requires a combination of people, processes and technologies. The foundational elements of a CSMS define an enterprise’s overall cybersecurity objectives including its risk tolerance, the potential impacts of events, the policies that the organization will adopt to ensure security, etc. These are not a “tool.” They require thoughtful debate and trade-offs, discussed at senior levels of an organization.
However, to ensure the implementation of these policies, as well as the maintenance and continuous improvement of overall security levels (SLs), technology is a critical component in the overall program. As we hear over and over, the No. 1 challenge in achieving ICS cybersecurity is resources. Technology enables greater efficiency and effectiveness to reduce the resource burdens required.
- Monitoring is NOT enough. Security requires active management of the devices and systems to ensure they are secured as designed, and that security is maintained – and improved – over time. Certainly, monitoring or initial visibility is an important component. But to achieve true security level improvements, organizations need to conduct “OT systems management” to patch, harden configurations, manage users and accounts, manage antivirus and other protective solutions, etc. This active management is a necessary capability in the overall Cyber Security Management System of any organization.
This point is perhaps best made in reviewing the Foundational Requirements (FR) in IEC 62443.
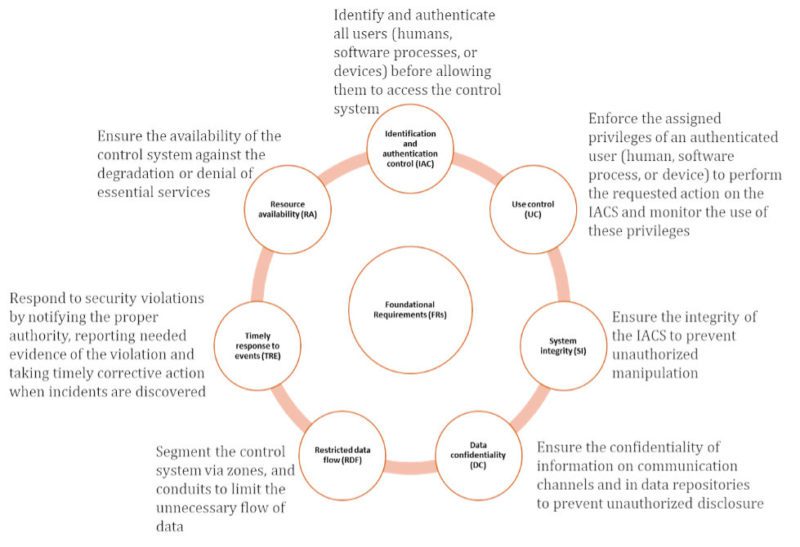
- FRs require a wide range of security management across all Systems Under Consideration (SUC), both device level and process level, requiring holistic security approaches.
The FRs are comprehensive across a range of security elements. IEC 62443 applies both to product development/procurement as well as to the overall process operations of industrial controls systems. Many manufacturers are pursuing SL 1 or 2 status for their products, which is a great initial outcome of the standards. But true security will require operators themselves to adopt the standards across their systems-of-systems. Security of the control system involves the interaction of many components, broken into “zones” and “conduits.” IEC 62443 requires taking this systemwide look at security to increase maturity across the landscape.
To manage IEC 62443 across FRs, organizations need to manage their implementation and continuous improvement across multiple security elements and layers of SUCs. Using just one capability to secure an OT environment would be difficult for any resource, skilled or not, but organizations need to do this across multiple capabilities. Fortunately, the ISA/IEC 62443 committees have a diverse audience of original equipment manufacturers (OEMs), asset owners and security practitioners, and the focus is on a combination of management, action, monitoring and procedure. Each of these FRs can have specific SRs or another form of enhancement based on the use case.
If we are to continue with the philosophy that an organization’s security is made up of more than a single product’s SL-T designation, then it should stand to reason that cyber risk reduction for an asset owner must not just be for zones, conduits, devices and endpoints – but instead inclusive of the larger ecosystem at a facility. This would mean an asset owner needs to cover in-depth several FRs, multiple systems, zones and conduits.
ISA 62443 alignment requires coverage across all areas of the people-process-technology spectrum. In fact, it explores organizational aspects including requiring processes/procedures, maintaining asset inventories, applying security controls and, of course, having the resources or partners to do so. This means an effective security product should be robust and not limit itself to targeting one specific type of asset. Security is not a one-time investment, but a continuous investment similar to purchasing and maintaining a vehicle.
– This article originally appeared on Verve’s blog. Verve is a CFE Media content partner.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








