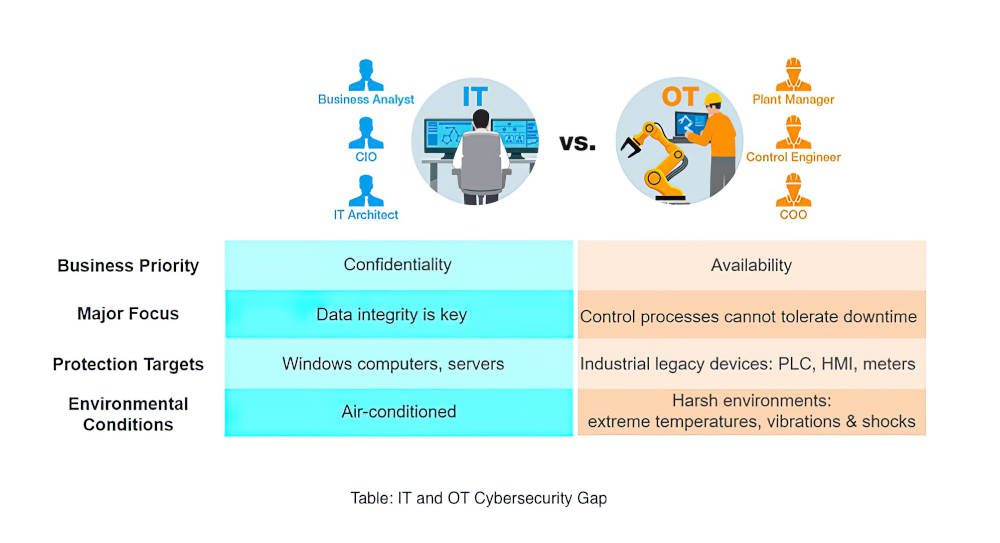
Getting buy-in: Tips on presenting cybersecurity to the boardroom
As industrial cybersecurity and critical infrastructure breaches mount, senior information security officers (SISOs), information technology (IT) directors, heads of engineering and others who lead cybersecurity initiatives are increasingly required to explain their cyber risks and […]