Most organizations rely heavily on security architects to vet products and assemble optimal solutions that align with security, technology, and business requirements. These technical experts spend a disproportionately large amount of energy on the integration of security infrastructure for centralization of controls and automation of security workflows. More often than not, they overemphasize integration points and capabilities in evaluating security products, which is not surprising.
After all, integration can reduce errors, provide a single consolidated view and broader situational awareness to an analyst, deliver breadth of data for artificial intelligence/machine learning (AI/ML) systems, and increase responsiveness to threats and incidents. Overall, integration and automation can increase efficiency and effectiveness of a security operations center (SOC).
Large organizations often configure their integrated infrastructure themselves. Small and medium sized enterprises rely on managed service providers’ (MSP) integrated environment. According to a study performed by Fortinet, about 82% of the surveyed organizations have integrated security environment and they are only driving further integrations to gain additional productivity value.
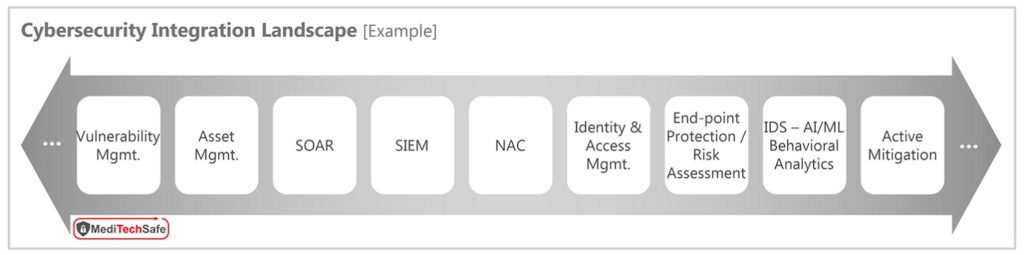
Recent cyber incidents involving SolarWinds and Kaseya VSA – some of the worst supply-chain related attacks – point to the challenges of managing integrations. Organizations integrate up to seventy different security products into a solution infrastructure. While each integration point brings some value, it also adds cost and introduces security risk. Security risk can be introduced at a product level, at an integration point, or during operation. The security risk can significantly outweigh the value of a product or the integration as seen in recent incidents. Adversaries were able to breach into thousands of end-user networks through Orion of SolarWinds and VSA of Kaseya.
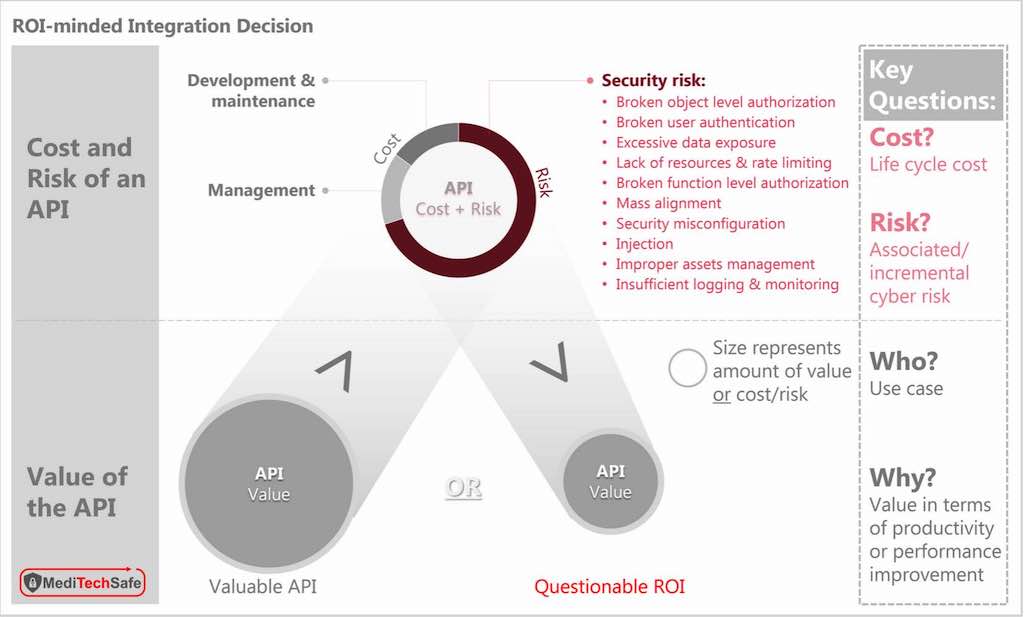
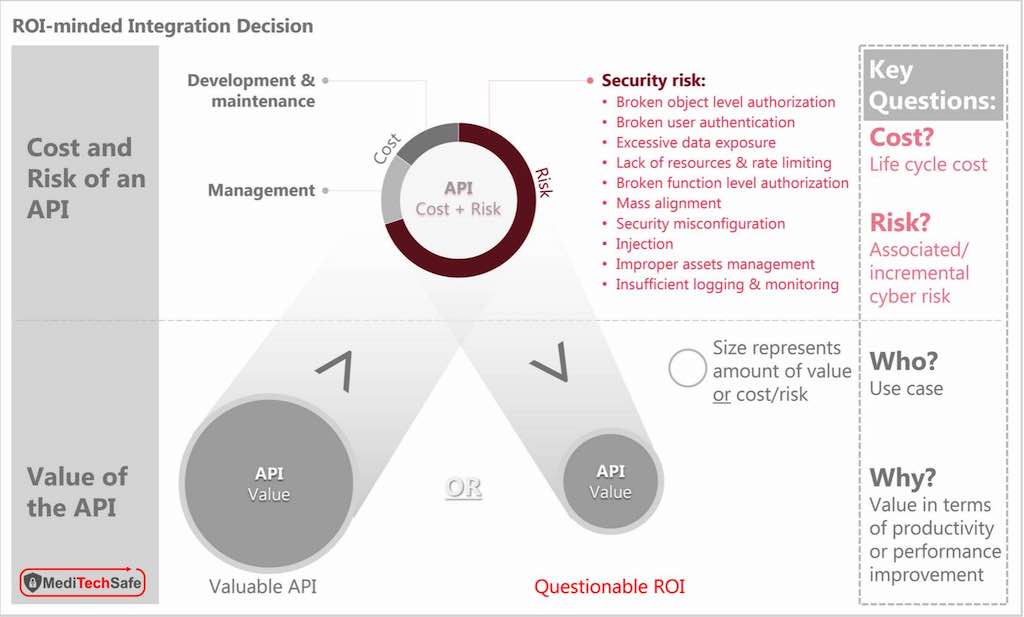
While organizations with technical expertise in security can easily integrate multiple products into an integrated security infrastructure, they often struggle to fully capture the whole dimension of risk management. A risk management mindset would require one to identify:
- What risk is being retired by a given action
- What the cost of implementing the action is
- What new risk the action introduces.
For example, the value of an intrusion detection system (IDS) is in its ability to enable quicker response to contain potential damage from a breach. By integrating it with the network access control (NAC), one can isolate specific network segments based on an IDS alert; this automation delivers incremental value in terms of improved responsiveness. Hence, the IDS and its integration with NAC can retire certain level of risk. That risk retirement value needs to be weighed against the cost of implementation and management of the integration.
Furthermore, the IDS packages are notoriously plagued by false positives. Hence, an organization must either add the cost of validating each alert or consider the risk of operational disruption from network access actions directed by the false positives. If the IDS or integration point were somehow compromised, an adversary could potentially gain access to the NAC. This additional risk may have to be taken into consideration in the decision-making process.
The risk management mindset requires security technical experts to cultivate multidimensional problem-solving skills with a strong business acumen. Hence, as organizations look to evolve their cybersecurity strategies, should security architects consider, introducing “strategic air-gaps” in their architecture and prioritizing a risk-based approach over a purely integration-based mindset?
– This article originally appeared on Meditechsafe’s website. Meditechsafe is a CFE Media content partner.
Original content can be found at www.meditechsafe.com.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.