Compliance regulations like the California Consumer Privacy Act (CCPA) and General Data Protection Regulation (GDPR) are created with good intentions. They aim to secure user data, ensure privacy and build trust between the companies and consumers. However, these regulations have become a double-edged sword for many organizations.
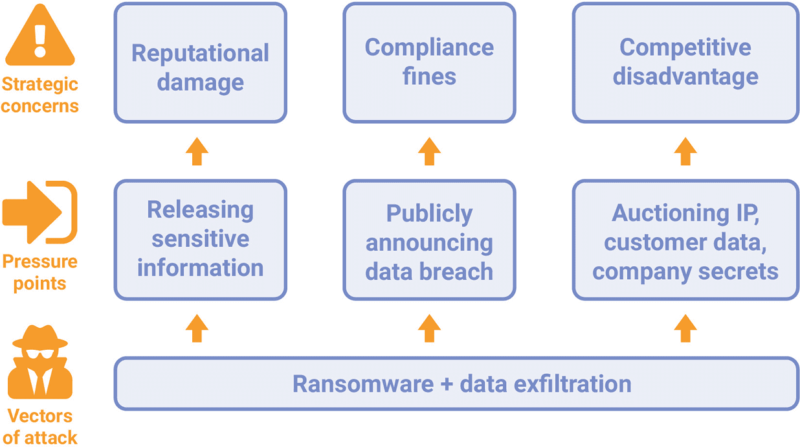
One reason for this is the rise of double extortion ransomware, where data is exfiltrated before files are encrypted. In this scenario, threat actors threaten to release sensitive company information online if the ransom is not paid. Companies can face hefty fines if they fail to comply with regulations, and thus they are pressured into paying the ransom just to keep the breach quiet.
Consequences of non-compliance
Today’s businesses face a range of demanding privacy regulations that are frequently being updated. This includes GDPR, CCPA and regulations from the New York State Department of Financial Services, or NYDFS.
With the shift to remote and dynamic working, and the ever-increasing complexity of business operations, there has been great pressure for companies to upgrade infrastructure and ensure that they are meeting all regulations.
Non-compliance can lead to significant financial penalties and drawn-out legal actions. If organizations fail to protect their data, the fees can be disastrous. GDPR can fine companies up to €20 million, or 4% of a company’s annual global turnover. For example, since 2017, Google has been fined a combined total of $9.5 billion by EU regulators.
Weaponization of compliance
Ultimately, compliance serves the important purpose of giving citizens more control and rights over their data. However, cyber criminals have realized that they can use the threat of non-compliance as a pressure point against organizations. Stolen data, if released to the public, can lead to huge regulatory fines.
We have seen this phenomenon in double extortion ransomware attacks, where threat actors steal sensitive data before they encrypt the files. Moreover, several ransomware actors, such as the Babuk gang, now have begun to forsake encryption in favor of extortion. This is because threat actors realize that exfiltration is more effective when many organizations continually back up files as a precaution against the threat of ransomware locking down files.
Ransomware actors often auction intellectual property, customer data and company secrets on the Dark Web. The Maze ransomware group established this trend back when it created a website in late 2019 to publicly “name and shame” organizations that had been compromised. These attacks included theft of information such as stolen PDF files, in addition to IP addresses and device names that were then uploaded and made publicly available on its website.
More than 70% of ransomware attacks now involve exfiltration.
The tactic was made infamous by the cyber criminal group REvil, who publicly announced their intentions on a Russian hacker forum in December 2019:
“Each attack is accompanied by a copy of commercial information. In case of refusal of payment, the data will either be sold to competitors or laid out in open sources. GDPR. Do not want to pay us – pay x10 more to the government. No problems.”
In these cases, threat actors are essentially saying, “If you pay us this small ransom, we will keep your data safe. If you don’t pay us, we have the power to release your data, and then you can take your chances with a huge compliance fine.”
Organizations may prefer to negotiate with cyber criminals and keep the breach – or the threat of breach – quiet. This is what the ransomware attackers are banking on.
How AI can help: Stopping ransomware and strengthening compliance
Compliance fines are not cheap. It took more than three years of legal proceedings for Equifax to settle their 2017 data breach. They finally settled with paying $700 million to regulators, including the Federal Trade Commission (FTC) and the Consumer Financial Protection Bureau (CFPB). Home Depot and Uber have also famously faced financial penalties of hundreds of millions of dollars.
These regulatory fines are compounding the potential consequences of ransomware. The continued ability of attackers to adapt and find new weaknesses means that it is crucial for companies to identify and contain ransomware in its earliest stages, with machine speed and precision.
With a proven ability to protect against machine-speed threats, and the ability to strengthen compliance with customizable alerts, artificial intelligence (AI) platforms can provide a powerful defense against double extortion ransomware.
Under pressure
Compliance is just one of the many strategic concerns facing ransomware victims. In addition to customer trust, valuable IP and long-term reputation, attackers and defenders are in a constant cat and mouse game, such that threat actors will continue to seek out new pressure points to extort their targets.
Organizations accordingly will benefit from using sophisticated technologies that neutralize ransomware before it has encrypted or exfiltrated files, stopping advanced threats in their earliest stages.
– This article originally appeared on Darktrace’s blog. Darktrace is a CFE Media content partner.
Original content can be found at www.darktrace.com.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








