
Research team looking to secure blockchain from cyber attacks
A research team from Northern Arizona University is looking to secure blockchain with an architecture that is compatible with cloud-based solutions.

A research team from Northern Arizona University is looking to secure blockchain with an architecture that is compatible with cloud-based solutions.
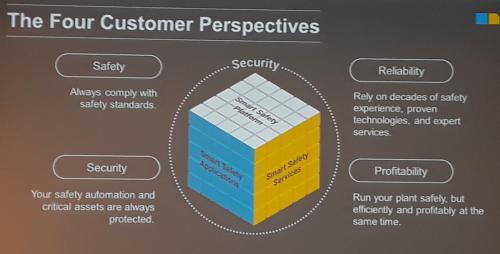
Technology update: Cybersecurity remains a key concern for manufacturing and process facilities as explained in the media session at ARC Forum 2019.

Companies can help prevent cyberattacks by forming a security operations center (SOC) to get the information technology (IT) and operations technology (OT) on the same page with the same goals.

A research team from Northern Arizona University is looking to secure blockchain with an architecture that is compatible with cloud-based solutions.

Technology update: Cybersecurity remains a key concern for manufacturing and process facilities as explained in the media session at ARC Forum 2019.

Companies can help prevent cyberattacks by forming a security operations center (SOC) to get the information technology (IT) and operations technology (OT) on the same page with the same goals.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.