
Four ways to sharpen building system technologies
IoT and intelligent management systems have revolutionized the capabilities of our buildings by enabling better automation and increasing efficiencies for better overall building health
Home | Facilities | Page 13

IoT and intelligent management systems have revolutionized the capabilities of our buildings by enabling better automation and increasing efficiencies for better overall building health
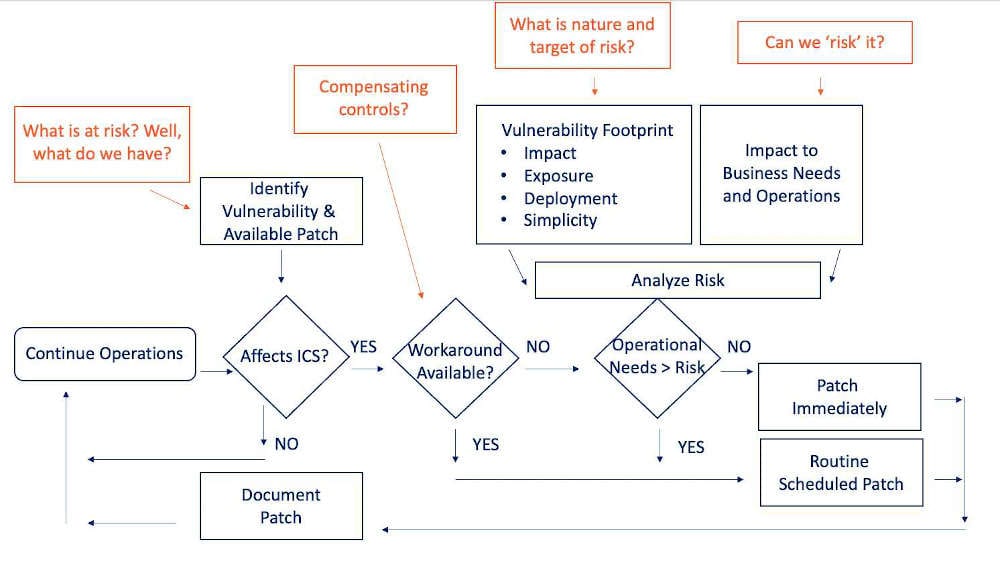
Most operational technology (OT) environments use scan-based patching tools, which are pretty standard but not overly insightful to show us what assets we have and how they are configured. What is really needed is robust […]

The COVID-19 pandemic is forcing companies to adjust their business practices and settle to a new normal. See four tips on how edge computing and the Industrial Internet of Things (IIoT) can help companies adjust.

For a robot to be safe, it must also be secure from cyberattacks in the age of Industrie 4.0 and the Industrial Internet of Things (IIoT). Everyone in the information technology (IT) and operations technology (OT) departments are responsible for ensuring this happens.

Hot on the heels of the high-profile SolarWinds attack comes the Oldsmar water treatment facility attack. This one is more targeted and focused on a specific – and very critical – piece of infrastructure. A […]

Cybersecurity education: Human hacking, the compromise of human assets, is often the first step in a cybersecurity breach, even if or when technical systems are secure. Help coworkers and those in your supply chain to avoid being the entry point for attack. Learn attack methods, five attack types and five prevention techniques.

What does OSHA teach us about industrial cybersecurity? Clearly, high cybersecurity risk could increase risk of industrial accidents, but OSHA’s model can help in other ways. Prior to 1970, worker safety in industrial settings was […]

Protecting programmable logic controllers (PLC) and programmable automation controllers (PAC) from security threats should begin even before an attack is detected.

Learning Objectives Cybersecurity global standards from IEC, ISA Global Cybersecurity Alliance and UL help lower risk. Cybersecurity education and training. The Industrial Internet of Things (IIoT), connected devices and the vast amounts of generated data create industrial […]
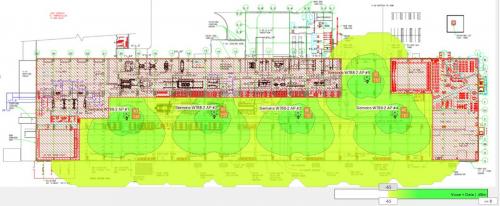
Deployments and optimal operation of industrial wireless local area networks (LANs) require attention to site survey, lifecycle management, cybersecurity and collaboration. Need to optimize existing industrial wireless networks?

IoT and intelligent management systems have revolutionized the capabilities of our buildings by enabling better automation and increasing efficiencies for better overall building health

Most operational technology (OT) environments use scan-based patching tools, which are pretty standard but not overly insightful to show us what assets we have and how they are configured. What is really needed is robust […]

The COVID-19 pandemic is forcing companies to adjust their business practices and settle to a new normal. See four tips on how edge computing and the Industrial Internet of Things (IIoT) can help companies adjust.

For a robot to be safe, it must also be secure from cyberattacks in the age of Industrie 4.0 and the Industrial Internet of Things (IIoT). Everyone in the information technology (IT) and operations technology (OT) departments are responsible for ensuring this happens.

Hot on the heels of the high-profile SolarWinds attack comes the Oldsmar water treatment facility attack. This one is more targeted and focused on a specific – and very critical – piece of infrastructure. A […]

Cybersecurity education: Human hacking, the compromise of human assets, is often the first step in a cybersecurity breach, even if or when technical systems are secure. Help coworkers and those in your supply chain to avoid being the entry point for attack. Learn attack methods, five attack types and five prevention techniques.

What does OSHA teach us about industrial cybersecurity? Clearly, high cybersecurity risk could increase risk of industrial accidents, but OSHA’s model can help in other ways. Prior to 1970, worker safety in industrial settings was […]

Protecting programmable logic controllers (PLC) and programmable automation controllers (PAC) from security threats should begin even before an attack is detected.

Learning Objectives Cybersecurity global standards from IEC, ISA Global Cybersecurity Alliance and UL help lower risk. Cybersecurity education and training. The Industrial Internet of Things (IIoT), connected devices and the vast amounts of generated data create industrial […]

Deployments and optimal operation of industrial wireless local area networks (LANs) require attention to site survey, lifecycle management, cybersecurity and collaboration. Need to optimize existing industrial wireless networks?
Keep your finger on the pulse of top industry news
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.