Not long ago, a major water utilities firm in the UK revealed plans to move a significant part of their supervisory control and data acquisition (SCADA) system to the cloud. This is one of the most high-profile transitions of operational technology (OT) to managed cloud services to date.
Though moving industrial control systems (ICS) to the cloud has been theoretically possible for at least 10 years, the associated risks have meant that uptake has been slow. Operational technology is often bespoke and has traditionally been isolated from the internet, and so moving OT systems to the cloud can impact reliability, performance and security. ICSs are high-stakes environments. The slightest period of downtime can have significant ramifications for the safety of workers and the business as a whole.
These considerations have traditionally led most organizations to conclude that the benefits of moving ICS to the cloud — namely, making it cheaper and easier to manage, and improving its availability — are outweighed by the risks. Even though workers may be able to remotely control equipment on the factory floor, for example, the threat of those with malicious intent gaining access to the same protocols is a strong deterrent for organizations to hold back on digital transformation in this area.
However, the conditions brought about by the pandemic have brought unique challenges to the management of SCADA systems on-site, causing organizations to consider secure ways to slowly transition these environments to the cloud.
But as OT converges with information technology (IT) in the cloud, so too do their respective risks. Only complete and unified visibility across both IT and OT will allow companies to accelerate their digital transformation whilst at the same time managing the associated risks of digitization and of their increasingly dynamic workforces.
ICSaaS
What will this ICS cloud infrastructure look like in practice? ICS applications, services and databases, such as the Historian, would be hosted in the cloud, with programmable logic controllers (PLCs) feeding data directly to the cloud. With this underway, workstations can access the ICS data remotely. The attack surface of software as a service (SaaS) for ICS — or ICSaaS — would end up looking more similar to common SaaS networks than to a traditional SCADA/ICS network.
Simply put, moving industrial systems to the cloud renders traditional security concepts obsolete. The network segmentation and hierarchy recommended by the Purdue model, for instance, will become less relevant as more high-stakes environments embrace digital transformation.
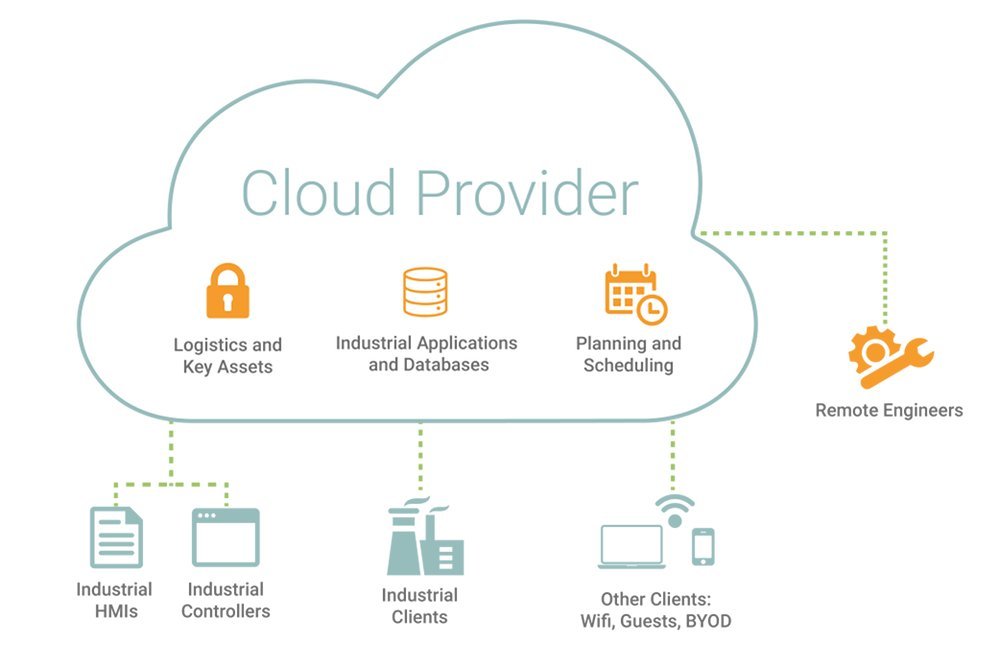
Figure 1: A schematic of ICSaaS cloud infrastructure
Security concerns with the cloud
The usual security concerns associated with SaaS carry over to ICS environments as they converge with the cloud. With ICSaaS, the data involved in industrial processes can be accessed from anywhere, raising questions about data security, as well as compliance and regulation.
Further, with ICSaaS, there is a loss of visibility and control over network. Not only does the workforce become increasingly dynamic, no longer bound to the HQ, but organizations also depend on a wider range of technologies on a daily basis – which means more work for security teams trying to keep up with these variables. These factors increase risk from insider threat, as well of a host of other attack vectors that emerge when industrial operations are being handled by workers who are not physically present in the on-prem workspaces.
As industrial workers begin to carry out operations in the cloud, siloed and static security controls will succumb to the same pitfalls as they have in today’s dynamic workforce. Their hard-coded, pre-defined rules and signatures are not designed to adapt with sudden transformation, so they will be forced into either default inclusion listing, or will produce unworkable numbers of false positives, impacting operations.
ICS security teams require a fundamentally different approach. Hundreds of organizations in the industrial space are turning to self-learning, artificial intelligence (AI)-powered technology that continuously adapts and learns patterns of behavior across the digital ecosystem – from ICS to the cloud and beyond – in order to distinguish “strange but benign” behavior as well as “strange but threatening” activity indicative of a cyber threat.
AI technology learns on the job, understanding normal for every user, device and controller. This enables it to detect anomalies that signal an intrusion.
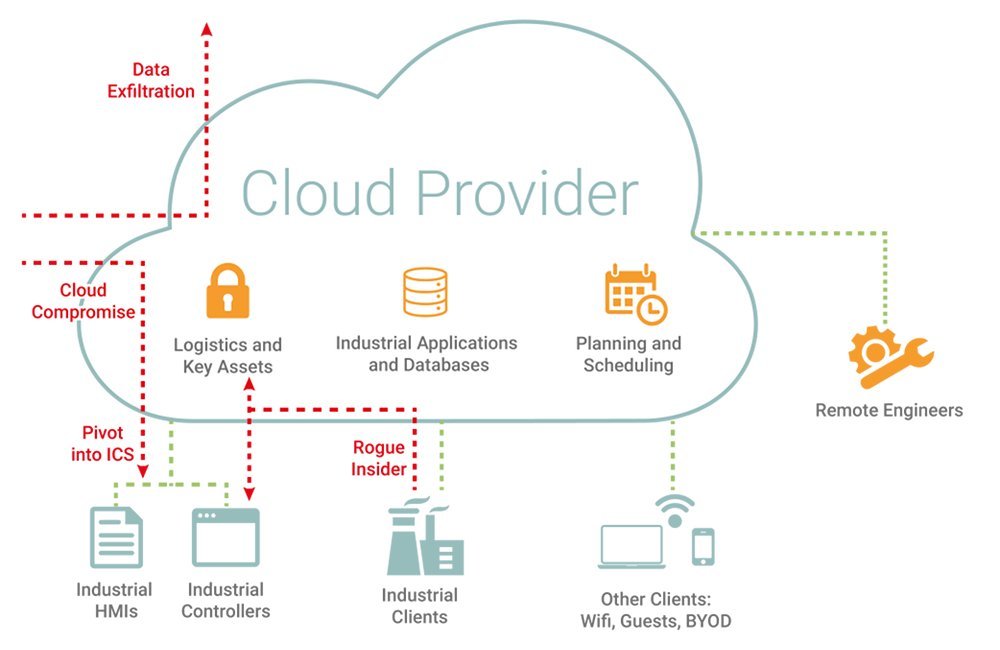
Figure 2: Possible threats to an ICSaaS cloud infrastructure
ICSaaS and artificial intelligence
As ICSaaS comes of age, attackers will exploit never before seen attack vectors. The combined challenges of cloud security and ICS security — loss of visibility, communication barriers, varying technical knowledge, differing capabilities, misaligned objectives — make securing ICSaaS cloud infrastructure a considerable challenge.
Attacks seen in the wild recently, such as the EKANS ransomware, have managed to breach the IT and OT divide. These blind spots, however, can be illuminated by a unified platform approach to securing industrial and IT systems. Monitoring activity across the entire digital estate allows a single system to recognize when malicious activity in one area might become a precursor to compromise in another, more critical, area.
By moving away from rules and signatures of predefined threats and learning digital “patterns of life” across the organization, AI represents a step-change in cybersecurity. Introducing self-learning AI systems into the security infrastructure allows for real-time detection and investigation into threats across the entire digital estate. This capability will enable more archaic OT systems to go through digital transformation whilst managing the risks brought about by ICSaaS.
Thanks to Darktrace analyst Oakley Cox for his insights on the above investigation.
– This article originally appeared on Darktrace’s blog. Darktrace is a CFE Media content partner.
Original content can be found at www.darktrace.com.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.








