Historically, industrial control systems (ICS) could exist as a closed-loop, with an air-gapped network and a solid physical security program insulating them from the outside world. An operator could trust the integrity of their operations based on process outputs, and when processes broke down maintenance was brought in to locate and fix the issue.
Not to say it was a simple time (it wasn’t), but the internet and digital transformation has changed the game at an ever-accelerating pace. Connecting corporate and industrial systems has enabled the adoption of modern technologies, introducing efficiency gains through remote access, modern data solutions, and greater automated coordination of business & industrial processes. However, the convergence of information technology (IT) and operational technology (OT) systems has blurred the border of two worlds, led to a host of security and governance problems, and brought new uncertainty to what the scope of responsibilities of a control system integrator are or should be.
Many control system integrators thrive in this new era, in all the noise seeing the opportunity to innovate, build a competitive advantage, and deliver more value to their customer by enhancing their customer’s operational visibility and cybersecurity posture by delivering a single capability: serial communications monitoring.
Enabling efficiencies through operational health monitoring
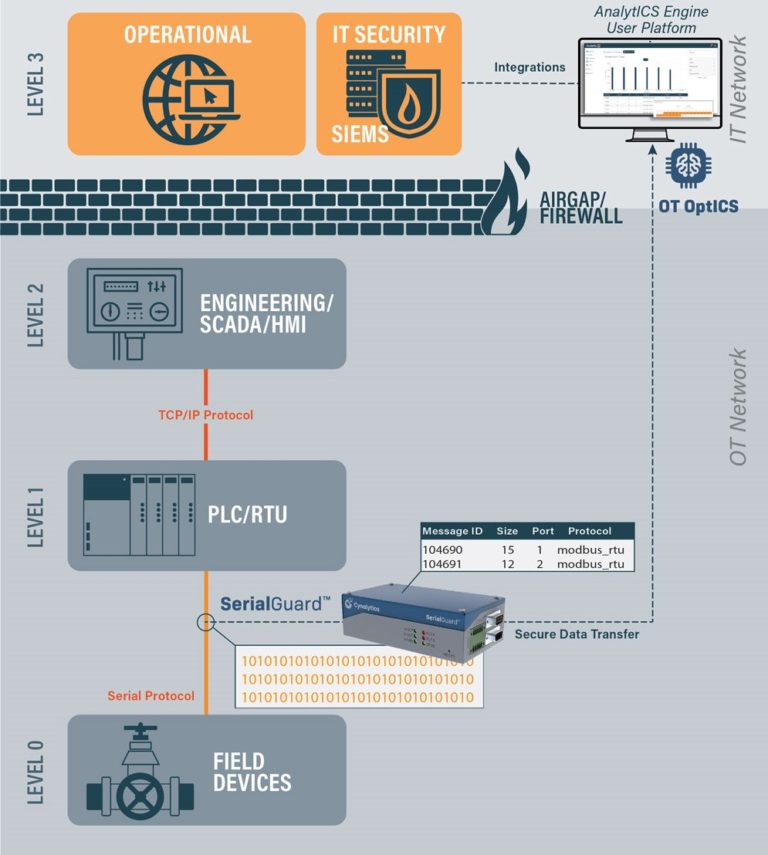
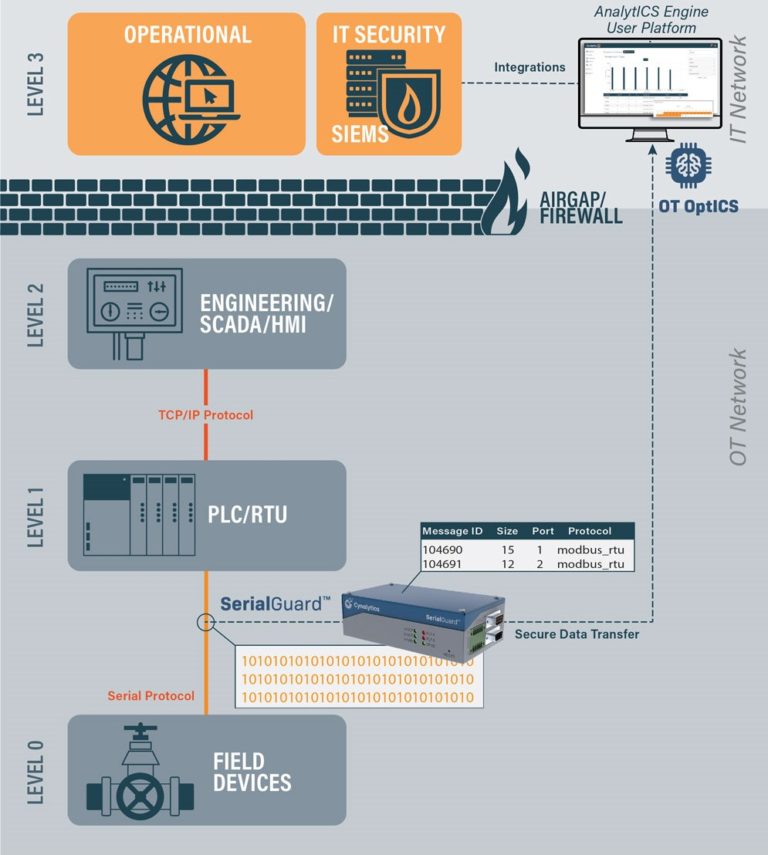
Within the Purdue Model [1], Serial Communications exist primarily at Levels 0 and 1 between logic controllers and legacy field devices –the most critical portions of the control system where physical processes occur. Calling these devices “legacy” becomes a misnomer as serial networks continue to be installed today [2]. Serial-connected devices have been a substantial part of control system communications for 40+ years and will be for the foreseeable future due to their prevalence, reliability, as well as the tremendous capital expenditure and operations effort that would have to be mobilized to replace these systems at scale.
While digital transformation has led to increased networking and data collection across the enterprise, serial communications have been an acute blind spot in control system data collection. While the status quo is to analyze device behavior at higher-levels after conversion to ethernet-based protocols, it lacks crucial context such as timing and direction data. Even when these communications are directly monitored, it is often performed with unsophisticated serial-to-Ethernet converters or active capture methods that could derail operations via device malfunction or malicious compromise by a cyber adversary.
With the power of serial communications data and a scalable way to process and analyze it, firms can optimize operational inefficiencies and locate malfunctions prior to failure conditions. While monitoring serial communications seems like a difficult tradeoff between operational efficiency and resiliency, operators can get the best of both worlds with passive and fail-safe capture methods. The visibility brought by proper serial communications monitoring lets control system operators cut costs through robust operational health monitoring.
Cybersecurity is an increasing threat to critical infrastructure
The largest downside to digital transformation is it comes with a cybersecurity tradeoff. Attackers have become increasingly aggressive in pursuing cyber-physical effects such as critical infrastructure downtime, asset damage, and process manipulation. The increased target on the back of critical infrastructure has put business continuity and human safety at risk, from IT-based attacks such as Colonial Pipeline to advanced OT attacks such as Industroyer that shut off power to ~200,000 people in Kiev in 2016.
Serial communications are unencrypted and unauthenticated, which pre-digital transformation was mostly a non-issue. However without serial communication monitoring capabilities, an ICS is now susceptible to false feedback attacks similar to Stuxnet, where a logic controller or other intermediary device is compromised. With this position established, a cyber adversary can send normal data to operators while having free rein to alter field device behavior to the tune of process disruption and asset destruction. The reality of this attack capability further ensures that adopting zero-trust visibility at every level of the ICS is critical to an organization’s cybersecurity posture.
– This article originally appeared on Cynalytica’s blog. Cynalytica is a CFE Media content partner. Edited by Chris Vavra, web content manager, Control Engineering, CFE Media, cvavra@cfemedia.com.
Cynalytica, Inc., is a partner member of the Control System Integrators Association (CSIA). For more, visit the company profile on the Industrial Automation Exchange.
REFERENCES
[1] Theodore Williams, Institute for Interdisciplinary Engineering Studies – Purdue University – https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.194.6112&rep=rep1&type=pdf
[2] Jonathan Baeckel, SANS.edu Graduate Research, 2021 – https://www.sans.org/reading-room/whitepapers/ICS/paper/40125
Original content can be found at cynalytica.com.
Do you have experience and expertise with the topics mentioned in this article? You should consider contributing content to our CFE Media editorial team and getting the recognition you and your company deserve. Click here to start this process.