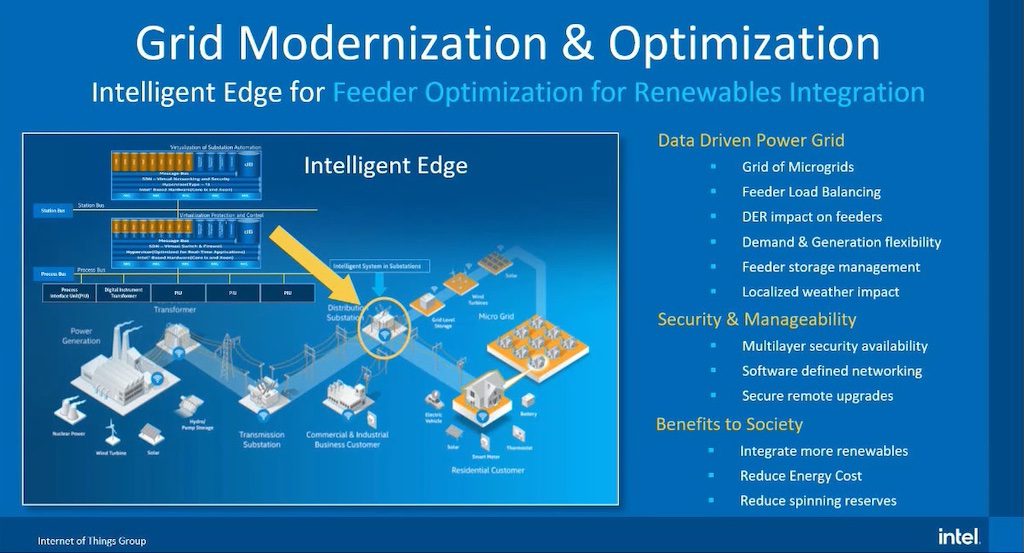
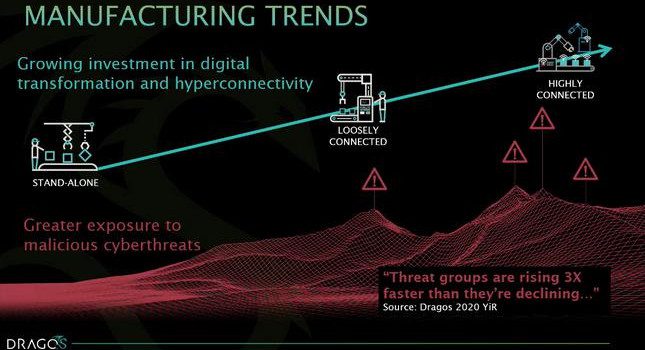
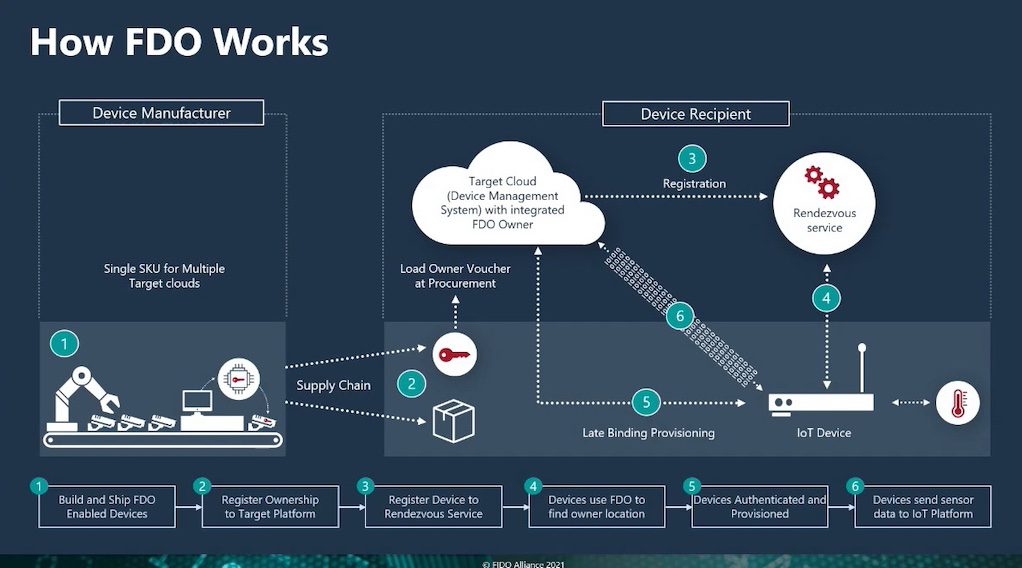
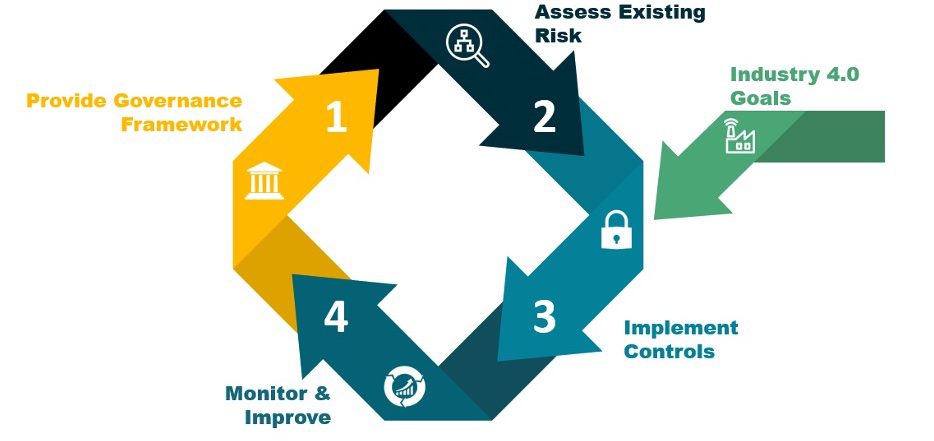
Throwback Attack: Ransomware hits multiple hospitals in coordinated attack
Threat actors are always on the lookout for pain points — manufacturing systems that can’t afford to go offline, critical infrastructure that can cause disruptions to everyday life or risks to human safety and, unfortunately, […]