
Cybersecurity services market predicted to grow at 10.7% from 2023 to 2032
According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.
Home | Strategies | View All

According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.

ODVA, governing body for EtherNet/IP, DeviceNet and other protocols, stepped up cybersecurity with single-pair Ethernet (SPE) capabilities.

In 2019, 38% of respondents considered threats to ICS as “high,” and grew to 40% in 2021, 41% in 2022 and 44% in 2023
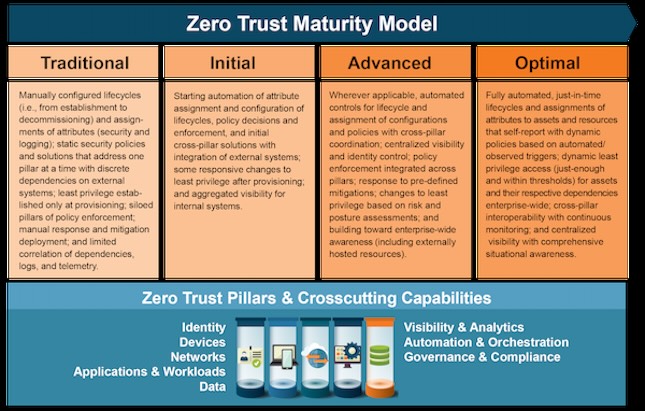
A zero trust mentality involves decisions across multiple pillars and organizational variables, informing the organization’s decisions.

Executing a threat hunt is a major topic in security operations discussions and becomes even more so when plans are made to traverse IT & OT.

On Oct. 31, 2023, version 14 of the MITRE ATT&CK framework was released. It’s designed to bolster cloud security with 18 new techniques.

Recently, Industrial Cybersecurity Pulse spoke with Leah Dodson of Nextlink Labs about integrating cybersecurity into products.
NIST releases version 2.0 of its cybersecurity framework, the first major update since its creation in 2014.

A big part safeguarding critical infrastructure from cyber threats revolves around cyber insurance and the cost to protect systems.

Industrial companies face a delicate balancing act between driving operational efficiency and defending against cyberattacks.

Ethan Schmertzler of Dispel discusses how new advances in AI are impacting industrial cybersecurity and social engineering attacks.
The Dragos 2023 OT Cybersecurity Year in Review has lessons and strategies, guiding you to a more secure industrial future.

Recently, the ICS Pulse talked to Leah Dodson of Nextlink Labs about the importance of communication in cybersecurity.

Understanding the value of government moves toward secure default configuration, insecure by design and secure by design.

Our top 5 pieces from November covered everything from the impact of large language models to increased holiday threats.

Our top 5 articles of October covered everything from avoiding scams to cyber-informed engineering to building stronger cyber habits.
Rockwell Automation and Dragos look at how executives and boards are addressing the state of manufacturing cybersecurity.

How can cybersecurity professionals emphasize the importance of OT cybersecurity to ICS boards and senior leadership?

Moty Kanias talks about why it’s essential to move toward cyber prevention and how AI is going to impact everything.

The top 5 from September 2023 covered how to cut through cybersecurity marketing and why security testing should be part of your strategy.

When it comes to cyberattacks on operational technology, should reputational risk be the highest consequence category?

the ICS Pulse Podcast talked to Mike Nelson of CyberCX about the cyber strategy that companies should be applying to be proactive.

Older generations from the United States, Canada and Australia were more likely to change their passwords compared to younger generations.

Lesley Carhart, of Dragos, discusses the dangers of supply chain compromise and how to get started with incident response.

Mike Nelson of CyberCX talks about the importance of security testing and how the industry has grown into adopting cybersecurity tactics.

Lesley Carhart, of Dragos, talks about how they got into cybersecurity and why concerns about ChatGPT might be overblown.

Debbie Gordon, of Cloud Range, on what companies can learn from tabletop exercises and why cyber training is so essential.
Debbie Gordon, of Cloud Range, discusses why attack simulation is important, whether you’re a Fortune 500 company or a mom-and-pop shop.
The top 5 articles from July 2023 covered the riskiest OT devices, how AI will impact cybersecurity and challenges facing IT/OT convergence.

On the ICS Pulse Podcast, we talked to Dennis Hackney, a cybersecurity professional, about zero trust in OT.

In a rapidly digitizing world, the importance of cybersecurity in safeguarding MES is becoming increasingly crucial.

The top 5 articles from June 2023 covered zero-trust architecture, protecting MES and driving Industry 4.0 through IT/OT convergence.
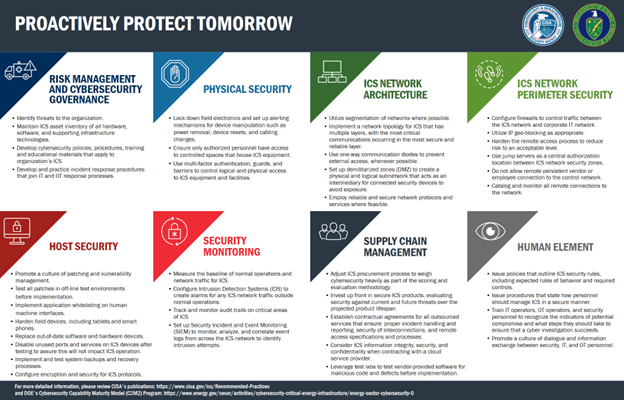
Analysis of the ICS advisory supports the development of appropriate strategies for their environments based on real-world risks.

A company’s ability to protect OT and critical infrastructure will be determined by how well it can cultivate cybersecurity talent.

Unscheduled and unplanned downtime on the plant floor can have significant consequences for manufacturing organizations.

Each new internet-connected device carries with it the burden of joining your network in accordance with latest cybersecurity practices.

Critical infrastructure is under attack. ICSP talked to Victor Atkins of 1898 and Co. about protecting critical infrastructure.

By identifying vulnerable suppliers and mitigating supply chain risk, a company can take proactive steps to protect their cybersecurity.

Manufacturing is the most targeted industry in the world for cyberattacks, and midsized manufacturers must have appropriate protections.
Learn how to prevent ransomware in OT/ICS industrial environments with 5 key steps to reduce the risk of an attack.

How do you get your organization cybersecurity prepared? Tabletop exercises are a great way to help build your incident response plan.

Asset visibility is the foundation of most cybersecurity activities, but many companies struggle to understand their own infrastructure.

Analysts at GlobalData offer their views of what 2023 holds for cybersecurity, including zero-trust cybersecurity.

Your ICS equipment could be at risk of shutdown on March 14, 2023, with the Microsoft DCOM hardening patch.

Critical infrastructure cybersecurity insights Critical infrastructure is very important to society and maintaining the basic needs of human life in modern times. Because of this, there is a need for critical infrastructure cybersecurity to protect […]

Endpoint security is the process of identifying, detecting, protecting and responding to cybersecurity threats at the device level.

Cyber criminals are experts at finding ways into protected systems and exploiting the information they find.

As the world becomes more and more connected, managing and mitigating cybersecurity risk with a SOC is a step toward cyber cleanliness.
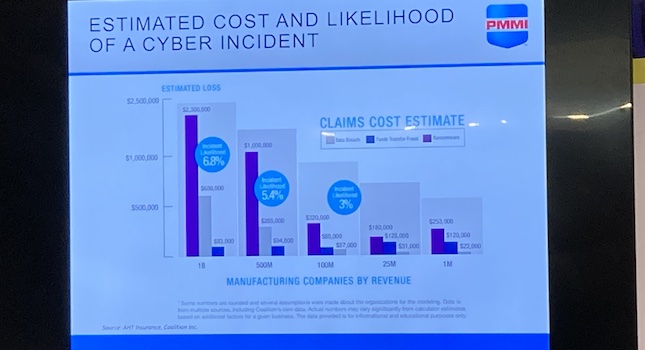
Defending and responding to cybersecurity breaches is an important part of gaining new and better security practices.

David Masson, Sam May and Bryan Bennett discuss the importance of having a business continuity plan in the event of a cyberattack.

Ransomware has evolved into a fully-fledged industry, with competing groups that continually introduce new capabilities and techniques.

At Black Hat 25, Omdia Senior Principal Analyst Rik Turner spoke on zero trust and its place in the current landscape.

How SBOMs can help protect the supply chain and why things are likely to get worse before they get better.

At Black Hat, Kyle Tobener discusses harm reduction, reviews the research and proposes a framework for applying it to cybersecurity risks.

Chris Krebs looks back at the first 25 years of Black Hat and attempts to gauge where the industry is going in the next 25.
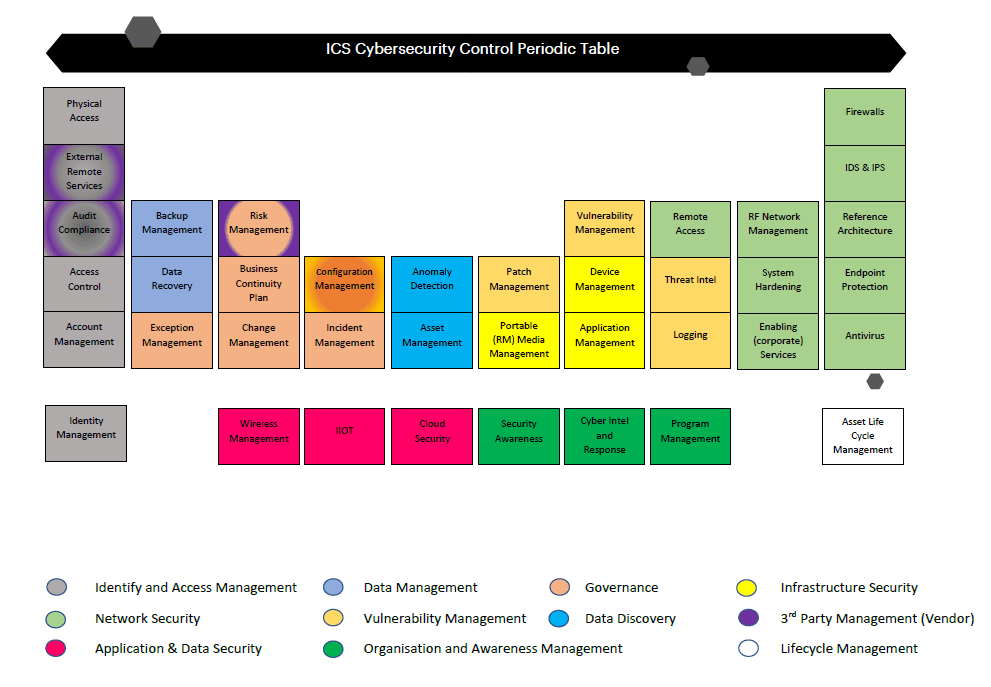
ICS Insights It is crucial to have proper cybersecurity when it comes to industrial control systems. The ICS periodic table provides insights on the best practices of industrial cybersecurity on industrial control systems. It is […]

Cybersecurity Insights As automation has become a regular feature of food processing facilities, the necessity for proper cybersecurity measures is more important than ever. It’s important to develop and implement a security awareness program, set […]

As an extra layer of security, several online services have adopted push notification-based two-factor authentication systems, whereby users must approve login attempts through a mobile device. In current authentication systems, especially the “tap to approve” […]

As the nature of digital warfare evolves, the need for a workforce trained in cybersecurity is critical for defending the United States from attacks. In response to the growing threat and the need for talent, […]

The CU Boulder-led initiative—MATCH, or Multi-tier Assistance, Training and Computational Help—is part of a larger program called Advanced Cyberinfrastructure Coordination Ecosystem: Services and Support (ACCESS). ACCESS is replacing the Extreme Science and Engineering Discovery Environment […]

It’s been a tough year for cybersecurity teams. Critical infrastructure has faced an onslaught of cyberattacks, including high profile incidents like the Colonial Pipeline and JBS ransomware attacks and the Florida water treatment plant hack, and the situation doesn’t look […]

Air gaps and segmentation are common concepts to secure operational technology (OT) networks with the goal of minimizing the harm of a breach and threats by isolating it to a limited part of the network. Unless an […]
A poorly worded email or a message sent in anger can be costly to the average person’s professional career. That’s nothing compared to a single email that cost Austria-based airplane component manufacturer FACC close to […]

It has been said that anything is for sale for the right price, and that includes your most trusted employees. Bribes can turn trusted employees into malicious insiders who secretly help launch a ransomware attack […]

The inability to stop production and a bureaucratic approval process are the main barriers that inhibit industrial cybersecurity projects according to a report by Kaspersky.

Regardless of how companies buffer supply chain gaps, they need to be cybersecure.

Without evidence of security performance, companies may be left with significant cybersecurity risk, according to a Mandiant research report.

Address five areas to improve remote operations, of growing importance to keep manufacturing sites running efficiently, reliably and safely from a distance, to address COVID-19 pandemic concerns and demographic workforce pressures. Secure software and devices can improve remote access, cybersecurity and digitization.

Manufacturers are realizing the potential dangers from cyber attacks, but that is the first step in the process. Learn how companies are trying to combat this growing problem and what more they can do.

Manufacturers’ technology often wasn’t built to suppress today’s digital threats and with the advent of mobile technology in the workplace, it is easy for hackers to exploit this soft weaknesses.

According to latest research report by DataHorizzon Research, the cybersecurity services market size was valued at $208.3 billion in 2023.

ODVA, governing body for EtherNet/IP, DeviceNet and other protocols, stepped up cybersecurity with single-pair Ethernet (SPE) capabilities.

In 2019, 38% of respondents considered threats to ICS as “high,” and grew to 40% in 2021, 41% in 2022 and 44% in 2023

A zero trust mentality involves decisions across multiple pillars and organizational variables, informing the organization’s decisions.

Executing a threat hunt is a major topic in security operations discussions and becomes even more so when plans are made to traverse IT & OT.

On Oct. 31, 2023, version 14 of the MITRE ATT&CK framework was released. It’s designed to bolster cloud security with 18 new techniques.

Recently, Industrial Cybersecurity Pulse spoke with Leah Dodson of Nextlink Labs about integrating cybersecurity into products.

NIST releases version 2.0 of its cybersecurity framework, the first major update since its creation in 2014.

A big part safeguarding critical infrastructure from cyber threats revolves around cyber insurance and the cost to protect systems.

Industrial companies face a delicate balancing act between driving operational efficiency and defending against cyberattacks.

Ethan Schmertzler of Dispel discusses how new advances in AI are impacting industrial cybersecurity and social engineering attacks.

The Dragos 2023 OT Cybersecurity Year in Review has lessons and strategies, guiding you to a more secure industrial future.

Recently, the ICS Pulse talked to Leah Dodson of Nextlink Labs about the importance of communication in cybersecurity.

Understanding the value of government moves toward secure default configuration, insecure by design and secure by design.

Our top 5 pieces from November covered everything from the impact of large language models to increased holiday threats.

Our top 5 articles of October covered everything from avoiding scams to cyber-informed engineering to building stronger cyber habits.

Rockwell Automation and Dragos look at how executives and boards are addressing the state of manufacturing cybersecurity.

How can cybersecurity professionals emphasize the importance of OT cybersecurity to ICS boards and senior leadership?

Moty Kanias talks about why it’s essential to move toward cyber prevention and how AI is going to impact everything.

The top 5 from September 2023 covered how to cut through cybersecurity marketing and why security testing should be part of your strategy.

When it comes to cyberattacks on operational technology, should reputational risk be the highest consequence category?

the ICS Pulse Podcast talked to Mike Nelson of CyberCX about the cyber strategy that companies should be applying to be proactive.

Older generations from the United States, Canada and Australia were more likely to change their passwords compared to younger generations.

Lesley Carhart, of Dragos, discusses the dangers of supply chain compromise and how to get started with incident response.

Mike Nelson of CyberCX talks about the importance of security testing and how the industry has grown into adopting cybersecurity tactics.

Lesley Carhart, of Dragos, talks about how they got into cybersecurity and why concerns about ChatGPT might be overblown.

Debbie Gordon, of Cloud Range, on what companies can learn from tabletop exercises and why cyber training is so essential.

Debbie Gordon, of Cloud Range, discusses why attack simulation is important, whether you’re a Fortune 500 company or a mom-and-pop shop.

The top 5 articles from July 2023 covered the riskiest OT devices, how AI will impact cybersecurity and challenges facing IT/OT convergence.

On the ICS Pulse Podcast, we talked to Dennis Hackney, a cybersecurity professional, about zero trust in OT.

In a rapidly digitizing world, the importance of cybersecurity in safeguarding MES is becoming increasingly crucial.

The top 5 articles from June 2023 covered zero-trust architecture, protecting MES and driving Industry 4.0 through IT/OT convergence.

Analysis of the ICS advisory supports the development of appropriate strategies for their environments based on real-world risks.

A company’s ability to protect OT and critical infrastructure will be determined by how well it can cultivate cybersecurity talent.

Unscheduled and unplanned downtime on the plant floor can have significant consequences for manufacturing organizations.

Each new internet-connected device carries with it the burden of joining your network in accordance with latest cybersecurity practices.

Critical infrastructure is under attack. ICSP talked to Victor Atkins of 1898 and Co. about protecting critical infrastructure.

By identifying vulnerable suppliers and mitigating supply chain risk, a company can take proactive steps to protect their cybersecurity.

Manufacturing is the most targeted industry in the world for cyberattacks, and midsized manufacturers must have appropriate protections.

Learn how to prevent ransomware in OT/ICS industrial environments with 5 key steps to reduce the risk of an attack.

How do you get your organization cybersecurity prepared? Tabletop exercises are a great way to help build your incident response plan.

Asset visibility is the foundation of most cybersecurity activities, but many companies struggle to understand their own infrastructure.

Analysts at GlobalData offer their views of what 2023 holds for cybersecurity, including zero-trust cybersecurity.

Your ICS equipment could be at risk of shutdown on March 14, 2023, with the Microsoft DCOM hardening patch.

Critical infrastructure cybersecurity insights Critical infrastructure is very important to society and maintaining the basic needs of human life in modern times. Because of this, there is a need for critical infrastructure cybersecurity to protect […]

Endpoint security is the process of identifying, detecting, protecting and responding to cybersecurity threats at the device level.

Cyber criminals are experts at finding ways into protected systems and exploiting the information they find.

As the world becomes more and more connected, managing and mitigating cybersecurity risk with a SOC is a step toward cyber cleanliness.

Defending and responding to cybersecurity breaches is an important part of gaining new and better security practices.

David Masson, Sam May and Bryan Bennett discuss the importance of having a business continuity plan in the event of a cyberattack.

Ransomware has evolved into a fully-fledged industry, with competing groups that continually introduce new capabilities and techniques.

At Black Hat 25, Omdia Senior Principal Analyst Rik Turner spoke on zero trust and its place in the current landscape.

How SBOMs can help protect the supply chain and why things are likely to get worse before they get better.

At Black Hat, Kyle Tobener discusses harm reduction, reviews the research and proposes a framework for applying it to cybersecurity risks.

Chris Krebs looks back at the first 25 years of Black Hat and attempts to gauge where the industry is going in the next 25.

ICS Insights It is crucial to have proper cybersecurity when it comes to industrial control systems. The ICS periodic table provides insights on the best practices of industrial cybersecurity on industrial control systems. It is […]

Cybersecurity Insights As automation has become a regular feature of food processing facilities, the necessity for proper cybersecurity measures is more important than ever. It’s important to develop and implement a security awareness program, set […]

As an extra layer of security, several online services have adopted push notification-based two-factor authentication systems, whereby users must approve login attempts through a mobile device. In current authentication systems, especially the “tap to approve” […]

As the nature of digital warfare evolves, the need for a workforce trained in cybersecurity is critical for defending the United States from attacks. In response to the growing threat and the need for talent, […]

The CU Boulder-led initiative—MATCH, or Multi-tier Assistance, Training and Computational Help—is part of a larger program called Advanced Cyberinfrastructure Coordination Ecosystem: Services and Support (ACCESS). ACCESS is replacing the Extreme Science and Engineering Discovery Environment […]

It’s been a tough year for cybersecurity teams. Critical infrastructure has faced an onslaught of cyberattacks, including high profile incidents like the Colonial Pipeline and JBS ransomware attacks and the Florida water treatment plant hack, and the situation doesn’t look […]

Air gaps and segmentation are common concepts to secure operational technology (OT) networks with the goal of minimizing the harm of a breach and threats by isolating it to a limited part of the network. Unless an […]

A poorly worded email or a message sent in anger can be costly to the average person’s professional career. That’s nothing compared to a single email that cost Austria-based airplane component manufacturer FACC close to […]

It has been said that anything is for sale for the right price, and that includes your most trusted employees. Bribes can turn trusted employees into malicious insiders who secretly help launch a ransomware attack […]

The inability to stop production and a bureaucratic approval process are the main barriers that inhibit industrial cybersecurity projects according to a report by Kaspersky.

Regardless of how companies buffer supply chain gaps, they need to be cybersecure.

Without evidence of security performance, companies may be left with significant cybersecurity risk, according to a Mandiant research report.

Address five areas to improve remote operations, of growing importance to keep manufacturing sites running efficiently, reliably and safely from a distance, to address COVID-19 pandemic concerns and demographic workforce pressures. Secure software and devices can improve remote access, cybersecurity and digitization.

Manufacturers are realizing the potential dangers from cyber attacks, but that is the first step in the process. Learn how companies are trying to combat this growing problem and what more they can do.

Manufacturers’ technology often wasn’t built to suppress today’s digital threats and with the advent of mobile technology in the workplace, it is easy for hackers to exploit this soft weaknesses.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.