
How should we assess the U.S. cybersecurity posture?
How should we be measuring the cybersecurity posture of the U.S.: activity, success, achievement? It’s hard to say.
Home | Regulations | View All

How should we be measuring the cybersecurity posture of the U.S.: activity, success, achievement? It’s hard to say.

When people talk about secure by design, do they really mean a security floor. Dale Peterson discusses a recent talk on the topic from S4.

The IMO defines maritime cyber risk as the potential threat to technology assets that could lead to security failures.

How can listed companies like Clorox establish cybersecurity good governance in 2023, especially in light of new SEC regulations.

Thomas Pace discusses why supply chain attacks are soaring, how CISA is taking positive cyber steps and how Sandra Bullock can save us.

Victor Atkins on why you should be patching known vulnerabilities in critical industries and how cybersecurity collaboration is on the rise.

Last year, NIST selected four algorithms to withstand attack by quantum computers. The agency has begun standardizing these algorithms.

NIST released a draft of the updated Cybersecurity Framework 2.0 to help organizations understand, reduce and communicate about cyber risk.

ICS Pulse interviewed Dennis Hackney about the benefits and real-world challenges of implementing zero trust in OT systems.

The National Cybersecurity Strategy has no approaches for how critical infrastructure will continue to function after a cyber incident.

The new National Cybersecurity Strategy focuses on regulation and would shift the responsibility for cyber resilience to tech giants.

DHS recently released its cybersecurity performance goals to establish a baseline of cyber for businesses and critical infrastructure. How valuable is this government involvement?

The TSA revised and reissued their Security Directive on oil and natural gas pipeline cybersecurity to focus on performance-based measures.

Protecting automation systems from cyberattacks — particularly those in critical infrastructure — has been an imperative for almost 20 years.

Given the interconnectedness of global manufacturing, companies are only as strong as the weakest link in their supply chain.

Many countries are passing IoT security legislation to create standards. What have governments done so far, and how much can this truly help? Haydn Povey talks IoT security legislation.

it’s impossible to have the discussion about protecting critical infrastructure without bringing the private sector into the mix.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently established a public catalog of vulnerabilities known to be exploited in the wild and issued a binding operational directive ordering federal agencies to patch those systems. But what impact will this really have? And what does it mean for non-government organizations?

Weaknesses in the software supply chain, coupled with reluctance from vendors to implement new changes or stray from familiar systems, have been major factors in allowing threat actors to wreak global havoc. When hackers exploit […]

In March of 2022, the Securities and Exchange Commission (SEC) proposed amendments to its cybersecurity rules and regulations. The proposed changes would require reporting of cyber incidents and disclosure of cyber mitigation strategies, both leading […]

Whether an organization is managing vulnerabilities within information technology (IT) or operational technology (OT) systems, prioritization stands as a huge factor for impactfully reducing the risk of attacks that leverage flaws within these systems. Organizations […]

The Cybersecurity and Infrastructure Security Agency (CISA) has always made recommendations along the lines of keeping the attackers out, performing cyber hygiene and detecting attacks, but they have rarely recommended the monitoring and controlling of […]
The United States government’s limited investment in the industrial infrastructure sector can be attributed to a lack of political will and leadership that has lasted for decades. However, the 2021 Infrastructure Improvement and Jobs Act […]

Learning Objectives Industrial remote workers have increased the number of remote connections. Cybersecurity risk increases with more remote connections. How are industrial companies mitigating risk? Connected workers are appearing in every industry and industrial activity. […]

The U.S. House Homeland Security Committee introduced the Cyber Incident Reporting for Critical Infrastructure Act of 2021. The bill seeks to amend the Homeland Security Act of 2002 to establish a Cyber Incident Review Office […]

Compliance regulations like the California Consumer Privacy Act (CCPA) and General Data Protection Regulation (GDPR) are created with good intentions. They aim to secure user data, ensure privacy and build trust between the companies and […]

While President Joe Biden’s July 28 executive order establishing his industrial control system (ICS) cybersecurity initiative was focused primarily on the electricity subsector, it did say that an action plan for natural gas pipelines was […]

I recently participated in a panel discussion on the Cybersecurity Executive Order’s Impact on Embedded Device Security. I signed off with a comment about my biggest worry: Someone will combine professional ransomware with a software supply […]

With the rise ransomware and increasingly frequent attacks on national critical Infrastructure, the U.S. government has tried to step in with a few measures to shore up cybersecurity. These have included things like the Executive […]

Throughout this year, the Biden administration has released several directives to strengthen the United States’ cybersecurity posture. Among them are the National Security Memorandum, the Cybersecurity Executive Order and the 100-day electric plan. It’s clear […]

To protect systems, people need to think like hackers, and that means knowing where the weak links in the supply chain are. SBOMs can help

Cyber defense expert Naval Dome and the offshore division of a supermajor have completed a joint project to identify and mitigate cyber risks common to offshore deepwater drilling rigs. Findings from the two-year project, culminating […]

Eric Byres, CTO of aDolus Technology, talks about supply chain attacks, where hackers target the weaker links in a supply chain network

The U.S. Department of Defense (DoD) supply chain has been under attack. This year’s ransomware events — such as the ones faced by a U.S. maritime base that brought cameras, door-access control systems and critical […]

On Sept. 29, 2020, the U.S. Department of Defense (DoD) released an interim rule to amend the Defense Federal Acquisition Regulation Supplement (DFARS) to implement a DoD assessment methodology and cybersecurity maturity model certification (CMMC) […]

Companies and governments alike are now facing a cybersecurity threat the likes of which the world has never seen. It’s bigger, faster and more sophisticated, which has the potential to overwhelm the humans tasked with […]

Prior to the late ’90s, terrorist groups were most often viewed through the lens of law enforcement and crime, not as a national security priority. Their pursuit was led by the FBI and international police […]

Amidst all the high-profile cyberattacks of the last year, President Joe Biden released a National Security Memorandum (NSM) on Improving Cybersecurity for Critical Infrastructure Control Systems. It covers how the government wants to improve cybersecurity […]

The CVSS was designed for IT responders, and many in OT question its effectiveness in measuring ICS vulnerabilities, says Ron Brash of Verve
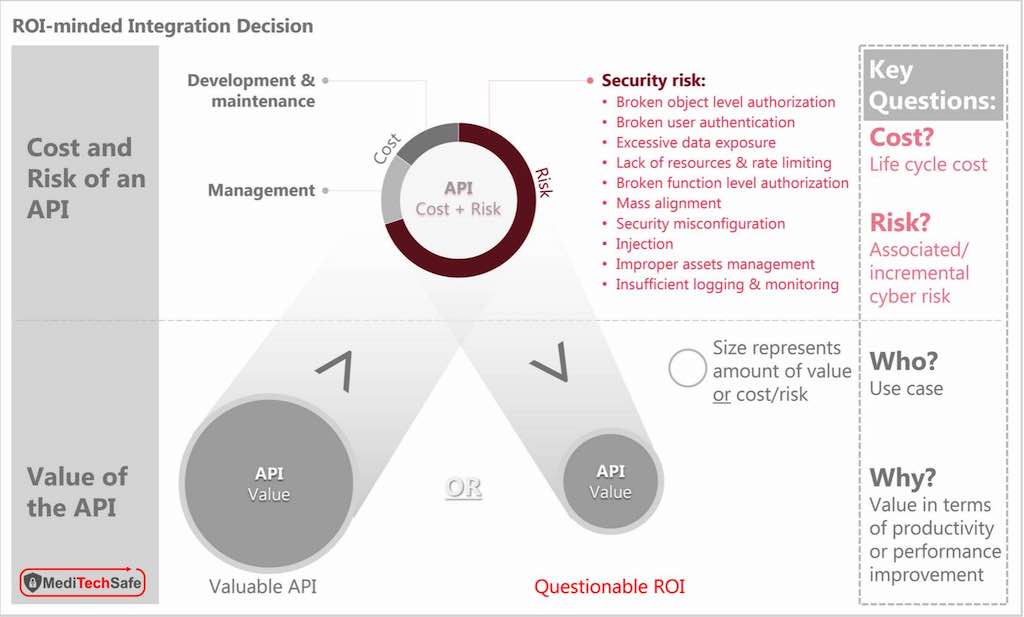
Most organizations rely heavily on security architects to vet products and assemble optimal solutions that align with security, technology, and business requirements. These technical experts spend a disproportionately large amount of energy on the integration […]

Due to innovative business models behind ransomware-as-a-service, fundamental increase in reliance on vulnerable information technology (IT) systems by physical process controls and the evolving cyber insurance market means that every industrial organization needs to reassess […]

Ransomware attacks have skyrocketed in recent years. There is no sign of slowing down despite the increase in spending and risk awareness. Cybersecurity personnel often feel burned-out and relatively ineffective. They are constantly firefighting, and […]

The Federal Service for Technical and Export Control (FSTEC) is a difficult topic, but it is essential to explore in order to understand how this strict Russian regulation affects cybersecurity tool manufacturers and system integrators. […]

President Joe Biden signed a cybersecurity executive order on May 12 to help strengthen the federal government’s cyber defenses and increase cooperation between the public and private sectors. The Executive Order on Improving the Nation’s […]

The Biden administration took an unusual and aggressive step last week when it formally blamed Russia’s Foreign Intelligence Service for the SolarWinds cyberattack and imposed new Russian sanctions. Given the bold nature of the breach, […]

President Biden declared January 27, 2021 to be Climate Day, and released a set of Executive Actions to address the Climate Crisis. The strategic goal of these policies is to “lead a clean energy revolution […]

When the Biden administration took over in January 2021, they made it clear the government response to cybersecurity will be a major focus

Over the last few months, there has a noticeable uptick in public ransomware attacks. High-profile and often highly advanced ransomware variants, such as Egregor, Maze, REvil/Sodinokibi have been noted in almost every industry around the […]

Protecting industrial automation systems is easier when controllers offer built-in cybersecurity features.
The International Society of Automation (isa.org) is a non-profit professional association founded in 1945 to create a better world through automation. ISA advances technical competence by connecting the automation community to achieve operational excellence. The […]
Despite the threats of cyberattack on computer-controlled industrial systems, utilities and other users of these systems can be hesitant to adopt common security technologies out of concern for their impact on system performance. NIST has […]

System integrators need to ensure that their automation systems are IEC 62443-compliant to adhere to international cybersecurity requirements.

As the industry continues to gain momentum in wireless control solutions, what is the future of lighting controls in critical applications such as a health care environment?

Cybersecurity regulations are deliberately written to be forward looking and encourage best behaviors and companies should be vigilant in their compliance to prevent potential cyber attacks.

Supply chain security is crucial as data becomes more important to a company’s success. Ten principles from the Charter of Trust and 17 baseline requirements for the supply chain are highlighted.

How should we be measuring the cybersecurity posture of the U.S.: activity, success, achievement? It’s hard to say.

When people talk about secure by design, do they really mean a security floor. Dale Peterson discusses a recent talk on the topic from S4.

The IMO defines maritime cyber risk as the potential threat to technology assets that could lead to security failures.

How can listed companies like Clorox establish cybersecurity good governance in 2023, especially in light of new SEC regulations.

Thomas Pace discusses why supply chain attacks are soaring, how CISA is taking positive cyber steps and how Sandra Bullock can save us.

Victor Atkins on why you should be patching known vulnerabilities in critical industries and how cybersecurity collaboration is on the rise.

Last year, NIST selected four algorithms to withstand attack by quantum computers. The agency has begun standardizing these algorithms.

NIST released a draft of the updated Cybersecurity Framework 2.0 to help organizations understand, reduce and communicate about cyber risk.

ICS Pulse interviewed Dennis Hackney about the benefits and real-world challenges of implementing zero trust in OT systems.

The National Cybersecurity Strategy has no approaches for how critical infrastructure will continue to function after a cyber incident.

The new National Cybersecurity Strategy focuses on regulation and would shift the responsibility for cyber resilience to tech giants.

DHS recently released its cybersecurity performance goals to establish a baseline of cyber for businesses and critical infrastructure. How valuable is this government involvement?

The TSA revised and reissued their Security Directive on oil and natural gas pipeline cybersecurity to focus on performance-based measures.

Protecting automation systems from cyberattacks — particularly those in critical infrastructure — has been an imperative for almost 20 years.

Given the interconnectedness of global manufacturing, companies are only as strong as the weakest link in their supply chain.

Many countries are passing IoT security legislation to create standards. What have governments done so far, and how much can this truly help? Haydn Povey talks IoT security legislation.

it’s impossible to have the discussion about protecting critical infrastructure without bringing the private sector into the mix.

The U.S. Cybersecurity and Infrastructure Security Agency (CISA) recently established a public catalog of vulnerabilities known to be exploited in the wild and issued a binding operational directive ordering federal agencies to patch those systems. But what impact will this really have? And what does it mean for non-government organizations?

Weaknesses in the software supply chain, coupled with reluctance from vendors to implement new changes or stray from familiar systems, have been major factors in allowing threat actors to wreak global havoc. When hackers exploit […]

In March of 2022, the Securities and Exchange Commission (SEC) proposed amendments to its cybersecurity rules and regulations. The proposed changes would require reporting of cyber incidents and disclosure of cyber mitigation strategies, both leading […]

Whether an organization is managing vulnerabilities within information technology (IT) or operational technology (OT) systems, prioritization stands as a huge factor for impactfully reducing the risk of attacks that leverage flaws within these systems. Organizations […]

The Cybersecurity and Infrastructure Security Agency (CISA) has always made recommendations along the lines of keeping the attackers out, performing cyber hygiene and detecting attacks, but they have rarely recommended the monitoring and controlling of […]

The United States government’s limited investment in the industrial infrastructure sector can be attributed to a lack of political will and leadership that has lasted for decades. However, the 2021 Infrastructure Improvement and Jobs Act […]

Learning Objectives Industrial remote workers have increased the number of remote connections. Cybersecurity risk increases with more remote connections. How are industrial companies mitigating risk? Connected workers are appearing in every industry and industrial activity. […]

The U.S. House Homeland Security Committee introduced the Cyber Incident Reporting for Critical Infrastructure Act of 2021. The bill seeks to amend the Homeland Security Act of 2002 to establish a Cyber Incident Review Office […]

Compliance regulations like the California Consumer Privacy Act (CCPA) and General Data Protection Regulation (GDPR) are created with good intentions. They aim to secure user data, ensure privacy and build trust between the companies and […]

While President Joe Biden’s July 28 executive order establishing his industrial control system (ICS) cybersecurity initiative was focused primarily on the electricity subsector, it did say that an action plan for natural gas pipelines was […]

I recently participated in a panel discussion on the Cybersecurity Executive Order’s Impact on Embedded Device Security. I signed off with a comment about my biggest worry: Someone will combine professional ransomware with a software supply […]

With the rise ransomware and increasingly frequent attacks on national critical Infrastructure, the U.S. government has tried to step in with a few measures to shore up cybersecurity. These have included things like the Executive […]

Throughout this year, the Biden administration has released several directives to strengthen the United States’ cybersecurity posture. Among them are the National Security Memorandum, the Cybersecurity Executive Order and the 100-day electric plan. It’s clear […]

To protect systems, people need to think like hackers, and that means knowing where the weak links in the supply chain are. SBOMs can help

Cyber defense expert Naval Dome and the offshore division of a supermajor have completed a joint project to identify and mitigate cyber risks common to offshore deepwater drilling rigs. Findings from the two-year project, culminating […]

Eric Byres, CTO of aDolus Technology, talks about supply chain attacks, where hackers target the weaker links in a supply chain network

The U.S. Department of Defense (DoD) supply chain has been under attack. This year’s ransomware events — such as the ones faced by a U.S. maritime base that brought cameras, door-access control systems and critical […]

On Sept. 29, 2020, the U.S. Department of Defense (DoD) released an interim rule to amend the Defense Federal Acquisition Regulation Supplement (DFARS) to implement a DoD assessment methodology and cybersecurity maturity model certification (CMMC) […]

Companies and governments alike are now facing a cybersecurity threat the likes of which the world has never seen. It’s bigger, faster and more sophisticated, which has the potential to overwhelm the humans tasked with […]

Prior to the late ’90s, terrorist groups were most often viewed through the lens of law enforcement and crime, not as a national security priority. Their pursuit was led by the FBI and international police […]

Amidst all the high-profile cyberattacks of the last year, President Joe Biden released a National Security Memorandum (NSM) on Improving Cybersecurity for Critical Infrastructure Control Systems. It covers how the government wants to improve cybersecurity […]

The CVSS was designed for IT responders, and many in OT question its effectiveness in measuring ICS vulnerabilities, says Ron Brash of Verve

Most organizations rely heavily on security architects to vet products and assemble optimal solutions that align with security, technology, and business requirements. These technical experts spend a disproportionately large amount of energy on the integration […]

Due to innovative business models behind ransomware-as-a-service, fundamental increase in reliance on vulnerable information technology (IT) systems by physical process controls and the evolving cyber insurance market means that every industrial organization needs to reassess […]

Ransomware attacks have skyrocketed in recent years. There is no sign of slowing down despite the increase in spending and risk awareness. Cybersecurity personnel often feel burned-out and relatively ineffective. They are constantly firefighting, and […]

The Federal Service for Technical and Export Control (FSTEC) is a difficult topic, but it is essential to explore in order to understand how this strict Russian regulation affects cybersecurity tool manufacturers and system integrators. […]

President Joe Biden signed a cybersecurity executive order on May 12 to help strengthen the federal government’s cyber defenses and increase cooperation between the public and private sectors. The Executive Order on Improving the Nation’s […]

The Biden administration took an unusual and aggressive step last week when it formally blamed Russia’s Foreign Intelligence Service for the SolarWinds cyberattack and imposed new Russian sanctions. Given the bold nature of the breach, […]

President Biden declared January 27, 2021 to be Climate Day, and released a set of Executive Actions to address the Climate Crisis. The strategic goal of these policies is to “lead a clean energy revolution […]

When the Biden administration took over in January 2021, they made it clear the government response to cybersecurity will be a major focus

Over the last few months, there has a noticeable uptick in public ransomware attacks. High-profile and often highly advanced ransomware variants, such as Egregor, Maze, REvil/Sodinokibi have been noted in almost every industry around the […]

Protecting industrial automation systems is easier when controllers offer built-in cybersecurity features.
The International Society of Automation (isa.org) is a non-profit professional association founded in 1945 to create a better world through automation. ISA advances technical competence by connecting the automation community to achieve operational excellence. The […]
Despite the threats of cyberattack on computer-controlled industrial systems, utilities and other users of these systems can be hesitant to adopt common security technologies out of concern for their impact on system performance. NIST has […]

System integrators need to ensure that their automation systems are IEC 62443-compliant to adhere to international cybersecurity requirements.

As the industry continues to gain momentum in wireless control solutions, what is the future of lighting controls in critical applications such as a health care environment?

Cybersecurity regulations are deliberately written to be forward looking and encourage best behaviors and companies should be vigilant in their compliance to prevent potential cyber attacks.

Supply chain security is crucial as data becomes more important to a company’s success. Ten principles from the Charter of Trust and 17 baseline requirements for the supply chain are highlighted.
Keep your finger on the pulse of top industry news
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.