
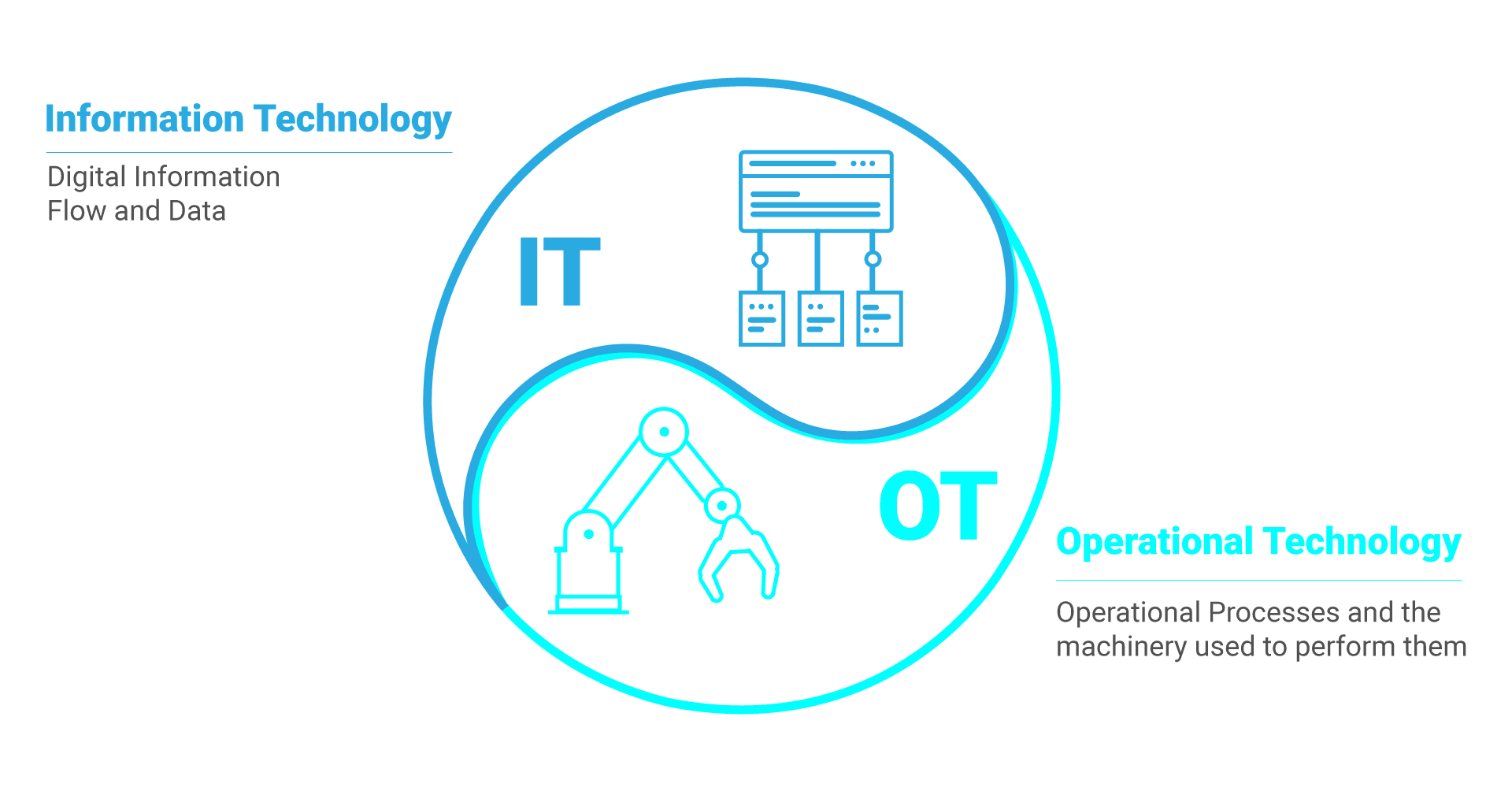
eBook: IT/OT Convergence – Spring Edition
This eBook includes stories on generative AI payloads, how IT can help accelerate digital transformation and predictions for OT/ICS security.

This eBook includes stories on generative AI payloads, how IT can help accelerate digital transformation and predictions for OT/ICS security.

OT cybersecurity is at greater risk of attacks than ever, and it requires a good, holistic plan that keeps workers educated and vigilant.

ICSP’s top 5 articles from March 2024 covered connecting IT and OT, regulating AI and a recently uncovered malware that targets OT systems.

A converged IT/OT SOC can help you defend against threats, but you definitely need buy-in throughout the organization.

Legacy OT systems, which used to operate in isolation from IT networks, are now exposed to modern cyber threats due to integration.

How secure are your OT systems? A converged IT/OT SOC can give you greater visibility and help defend against outside threats.

A converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

Eight key actions organizations can take to better protect themselves against threats targeting industrial operations and infrastructure.

Already used regularly for IT security, a converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

This webcast helped attendees learn about how organizations can create a converged IT/OT SOC. Additional questions were answered by Jim Cook.

If you’re ignoring OT and operational lifecycle management, some of your most important assets are probably insecure.

As employees take time off and businesses wind down over the holidays, cybercriminals ramp up. This creates a perfect storm of risk.

Dino Busalachi talks about purpose-built resources for OT and the new SEC ruling forcing companies to disclose cyberattacks.

New report finds a 400% increase in IoT and OT malware attacks, underscoring need for better zero-trust security for critical infrastructure.

Eric Byres talks about the improvement in regulatory frameworks and why OT/ICS systems are a juicy target for attackers.

Bringing SOAR and SOC standards to OT systems is critical as industrial cyberattacks increase in frequency and severity over time.

OT security must embrace the processes and protocols that IT put in place more than 20 years ago for enterprise networks.

The U.S. DOE, announced a new request for proposals (RFP) for up to $4.7 million to enhance the manufacturing cybersecurity landscape.

The U.S. government role in reducing OT cyber risk is bad in the short term, but it could be beneficial in the long term.

The system analyzes the likelihood that an attacker could thwart a certain security scheme to steal secret information.

What is the importance of OT managed services and how can organizations ensure around-the-clock monitoring and fortified OT security?

IT/OT convergence is vital for maximizing efficiency, but the ongoing trend toward convergence brings significant cybersecurity challenges.

CISA’s recent push for security by design and security by default could be a long-fought win for the OT community.

What is the best piece of advice cybersecurity practitioners give end users working to secure their connected OT devices?

What can the power industry learn from the evolution of NERC CIP in OT cybersecurity for improved reliability and security?

Many vulnerabilities have never been found to impact ICS/OT. That’s why it’s important to take a risk-based approach to cybersecurity.

Victor Atkins of 1898 and Co. discusses public-private partnerships, cybersecurity and critical infrastructure protection

Eric Byres talked to the ICS Pulse Podcast about the value of SBOMs, why OT is getting weaponized and reasons for optimism.

Eric Byres of aDolus discusses the themes at S4, managing vulnerabilities and the difference between cyber criminals and nation-state actors.

On the first day of the RSA Conference, Rockwell Automation attempted to help IT professionals secure OT systems.

Organizational challenges need to be addressed to achieve IT/OT convergence, from political and cultural barriers to technical complexities.

As the risk of cyber attacks on operational technology (OT) systems grows, so does the cost of OT cyber insurance.

Schreiber Foods, a part of the food and agriculture sector, was hit by a cyberattack on their computer systems used for organizing raw milk

As the world becomes digitized, businesses must understand the importance of maintaining strong IT and OT security to prevent attacks.

Tabletop exercises are a great way to help prepare an incident response plan. These exercises also help push IT/OT convergence forward.

Businesses that are over-reliant on IT to fortify OT security put themselves at risk of lost data, downtime and physical safety hazards.

Food and beverage manufacturers are wrestling with how to implement stronger manufacturing cybersecurity measures.

A CDV index can help measure the cyber preparedness and OT protection of a plant and critical infrastructure from cyber crime.

Looking to sell a security product to the OT market? It should require no changes to the ICS and have no impact on physical processes.

New emphasis is being placed on reducing incident severity across OT and IoT sectors, tapping into the strong safety culture of industrial environments.

A natural gas operator was hit by a ransomware attack via a spear-phishing campaign that resulted in a two-day shutdown of operations.

CISA and other organizations have released multiple notices about the importance of prioritizing vulnerabilities based on their risk.

Velta Technology and TXOne Networks offer a solution to the potential ICS and revenue disruption of the Microsoft DCOM hardening patch.

Using threat intelligence for visibility into threats to your OT network is a critical step in building a mature OT network defense.

Shadow OT is when security teams have an incomplete picture of what’s happening inside their operational systems.

We’ve seen several industrial companies that have learned a lesson from not applying industrial cybersecurity to protect their ICS networks.

Technology-enabled vulnerability assessment gathers detailed visibility of the risks of the environment and prioritizes those risks.

Enterprises have realized the importance of attack surface management to identify, prioritize and minimize threat vectors in an environment.

Jordan Lutz of Rockwell Automation speaks about recognizing the need for cyber resilience, IT/OT convergence and where to get started.

OT asset management and OT asset visibility are used similarly in the cybersecurity industry because there is not a delineation between them.

SIEM systems have the ability to collect, categorize and filter, which creates tailored security alerts for security operators.

By understanding people, processes, technologies, roles and procedures from an IT and OT perspective, you can create better digital safety.

There still is a lack of understanding as to the importance of cybersecurity, as well as the role that cybersecurity insurance should play.

How do organizations get their engineers and technicians up to speed with the knowledge and strategies needed to ensure OT security?

CFE Media brought industry experts together to discuss IT/OT convergence and why it is such an important part of cybersecurity.

What are the dynamics facing today’s OT engineers, whether they’re new to the industry or bringing years of experience?

ICS/OT infrastructure security is different in many ways from IT security, and one of the main reasons is the reverse confidentiality triad.

All organizations should ensure that cybersecurity risks (CSRM) receive appropriate attention as they conduct their ERM program.

As AI becomes more of a factor in industrial cybersecurity, what role will it play in defending supply chains and other networks?

Cybersecurity Insights There is a greater risk of cybersecurity attack against operational technology (OT) targets as machines become integrated with information technology (IT) systems. Consulting with subject matter experts (SMEs) and system integrators who are […]

IT and OT Insights IT and OT should be assessed differently from one another. However, if there is a set list of tasks to do with them working together, it must get done, which allows […]

Cybersecurity insights Ransomware is a type of cyberattack where a threat actor steals data from a company and holds it for ransom — although companies have been known to pay the ransom and get nothing […]

There has been a lot of talk lately about how to secure a budget from the C-suite. While most people seem to understand the need for cybersecurity, many companies and organizations are still lagging behind, […]

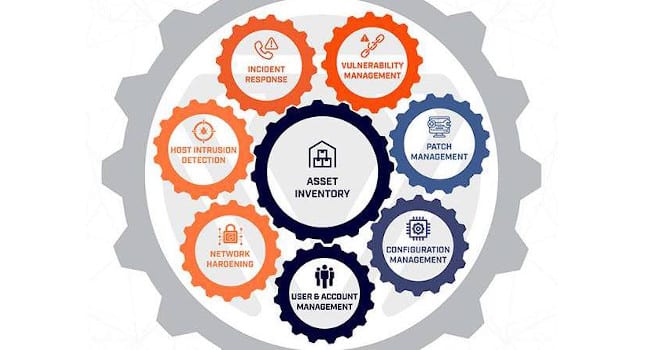
Solid asset management sits at the foundation of all cybersecurity activities. Enumerating assets into a solid inventory, tracking their current state – including configurations and versions deployed, and mapping their relationships all go a long […]

Cybersecurity insights The 2021 IBM Security Data Breach Report outlines key factors contributing to the rising costs of data breaches for industries all over the world. Health care has continued to be the most affected […]

In recent years, private companies and critical infrastructure alike have felt the full force of cyberattacks. This has put cybersecurity on the forefront of everyone’s mind, as people try to remain a step ahead of […]

As cybersecurity risk and complexity continue to grow, how is the long-standing gap between IT and OT evolving? Dragos asked four industrial security leaders that question and more in our recent webinar, What’s Behind the […]

The White House issued a statement by President Biden urging the critical infrastructure community to immediately strengthen their defenses based on their evolving understanding of Russian intent to use cyber attacks. Many of our customers are […]

The U.S. government has focused on trying to strengthen cybersecurity across all critical infrastructure sectors in recent years with actions such as the 100-day sprint and the executive order. But are these actions from the […]

Since the COVID-19 pandemic hit, the way people work has changed, opening a new world of vulnerabilities. High-profile attacks on companies like Colonial Pipeline, SolarWinds and Kaseya have put cybersecurity on everyone’s radar. But in […]

Dragos recently published the Dragos 2021 Year In Review report, which highlighted four key findings within the operational technology (OT) cyber threat landscape. This blog continues the series that expands on each of these findings, […]
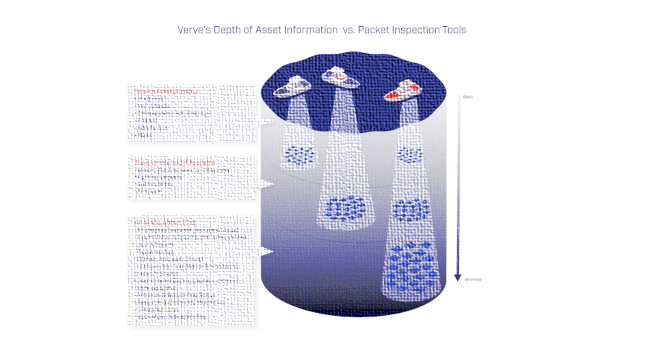
In information technology (IT), organizations have options to choose from to discover and aggregate asset information. In operation technology (OT), security asset management – discovery, inventory, risk evaluation, etc. – is more difficult given the […]

Richard Robinson discusses how to protect legacy OT assets and the role machine learning and artificial intelligence can play

Chief information security officers (CISOs) and directors of cybersecurity at industrial organizations continue to be frustrated at the challenge of applying core information technology (IT) security principles to operational technology (OT) environments. This runs the […]

On April 4, 2022, Secretary of State Antony Blinken released a statement announcing the creation of a “new” federal bureau — the Bureau of Cyberspace and Digital Policy (CDP). Even though the organization is the […]

As the Russia-Ukraine war continues, Russian cyber threat actors have been launching their attacks on the Ukrainian government. Given the widespread western support that Ukraine has received — in the form of money, weapons and harsh […]

Dragos, Inc., a leader in cybersecurity for industrial control systems (ICS)/operational technology (OT) environments, recently released its fifth annual Dragos ICS/OT Cybersecurity Year in Review (YIR) report, the most comprehensive report on cyber threats facing […]

To effectively combat pervasive cyberthreats like ransomware, organizations need to centralize their detection and response efforts. Oftentimes, they will turn to an endpoint detection and response (EDR) tool or managed detection and response (MDR) to achieve […]

Assessing and monitoring the security of operation technology (OT) systems can be aided by conducting an OT cybersecurity threat risk assessment (TRA). The process is fundamental to the protection of OT/critical infrastructure (CI) and key resources […]

Protecting information technology (IT) and operational technology (OT) networks is crucial to safeguarding the manufacturing industry. As part of the SecureAmerica’s Institute’s (SAI) nationwide initiative to empower the U.S. manufacturing enterprise, SAI and partners at […]

With the announcement of a new security directive coming from TSA for the rail industry, cybersecurity has been getting a lot of deserved attention from rail operators lately. Properly managing cyber risks in this sector of […]

Protecting key resources and critical infrastructure (CI), such as healthcare, finance, transportation, telecommunications, energy, and water/wastewater is essential to security, public health and safety, economic vitality and our overall way of life. Recent ransomware attacks, […]
Technology, AI and other cybersecurity measures can help protect businesses, but it’s nearly impossible to block every threat out there. One safety net stepping into the void to help protect companies financially is cybersecurity insurance.

In a rapidly changing world, we are grateful technology allows industrial organizations to operate their security and operational technology (OT) systems management quite effectively from a remote environment. Although it was not designed for a […]

Most companies realize that implementing a cybersecurity maturity model is a smart move and a necessity in today’s world. The challenge for most companies is, where do they start? Let’s walk through the process to […]

Nearly every week, the cybersecurity community buzzes around a newly discovered vulnerability or breach. December’s alert for the CVE-2021-4428 vulnerability in Apache Foundation’s Log4j software is no different. Also known as the Log4Shell vulnerability, it is present […]

The ISA/IEC 62443 cybersecurity documents contain a lot of guidance that easily overwhelms or confuses people when unpacking its components. It covers a range of topics including how to: Build a Cybersecurity Management System (CSMS) […]

The NERC CIP standards are the mandatory security standards that apply to entities that own or manage facilities that are part of the U.S. and Canadian electric power grid. They were initially approved by the Federal […]

Operational technology (OT) has become a heightened target for cybersecurity attacks. The need to address OT cyber risks has never been greater. New threats are emerging every day – both targeted as well as untargeted […]

On July 20, 2021, the Cybersecurity and Infrastructure Security Agency (CISA) and the Transportation Security Administration (TSA) sent a directive to the owner/operators of critical pipelines in the United States clarifying and further defining the initial […]

As industrial cybersecurity and critical infrastructure breaches mount, senior information security officers (SISOs), information technology (IT) directors, heads of engineering and others who lead cybersecurity initiatives are increasingly required to explain their cyber risks and […]
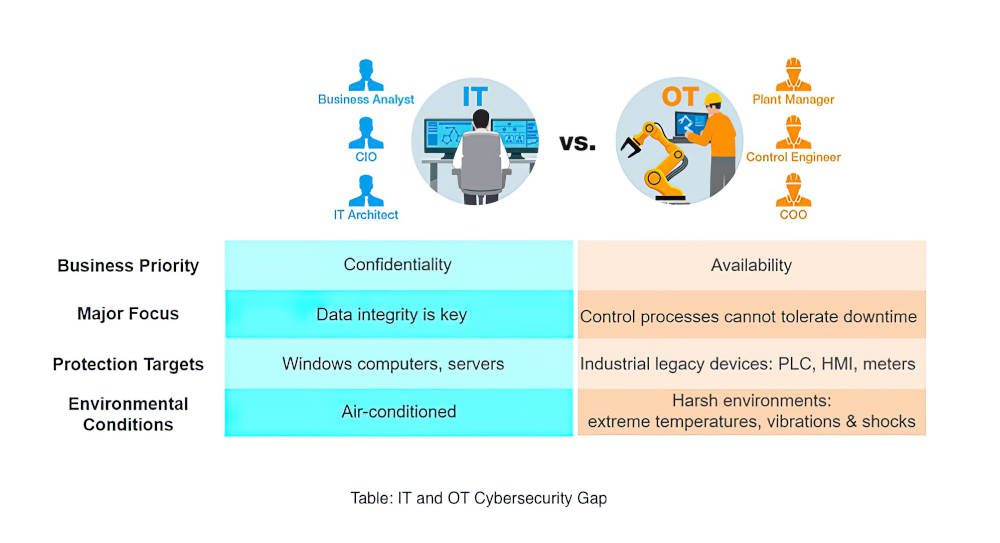
Amidst the COVID-19 pandemic, system integrators in the industrial sector moved toward one of the most influential changes in recent history, industrial digital transformation (industrial DX). However, before engaging, it is important to understand what […]

Modern industrial and critical infrastructure organizations rely on the operational technology (OT) environment to produce their goods and services. Beyond traditional information technology (IT) operations that use servers, routers, PCs and switches, these organizations also […]

Current industrial automation and control system (IACS) technology uses a blend of traditional control hardware and software with commercial off-the-shelf (COTS) information technology (IT) components (see Figure 1). This allows system designers to leverage an […]

Information technology (IT) and operational technology (OT) teams have historically been separated over the years — and for good reason. Their priorities are different. Their approaches and processes are different. They inhabit different worlds of […]

What is the NIS Directive? As part of the EU cybersecurity strategy, the European Commission first proposed the EU Network and Information Security (NIS) Directive in 2016, which was the first piece of EU-wide cybersecurity legislation. […]

Digital transformation might be great for business, but when it comes to protecting legacy OT systems, it can cause major problems

Convergence between information technology (IT) and operational technology (OT) networks requires a wide approach in order to ensure proper visibility and security. The need to control OT processes to optimize business has led to a […]

One of the most common questions we are asked at Splunk is how we work together with technologies like Industrial Defender. The discussion normally revolves around what it really means to protect and secure an […]
Matt Leipnik, lead industrial cybersecurity specialist for Nexus Controls, discusses why it’s important to create a culture of cybersecurity

Cyberattacks against industrial control systems (ICS) are growing in number and sophistication each year. The potential financial impacts from these attacks are growing in parallel. Major attacks, like the Colonial Pipeline and JBS meat plant incidents, have served as […]

More than two thousand years ago, ancient tactician Sun Tzu famously observed that, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.” While the world looks […]

It’s no secret that industrial organizations are at the forefront of cybersecurity attacks. A recent report by IBM X-force revealed the manufacturing industry jumped from the eighth most targeted industry to the second most targeted […]
How do you get buy-in for cybersecurity? And once you have that buy-in, how do you scale? Matt Leipnik of Nexus Controls offers some answers

There have been many papers and blogs written recently about how to ask your chief information security officer (CISO) for a cybersecurity budget or how operational technology (OT) personnel should engage with CISOs to ensure […]

Suzanne Gill of Control Engineering Europe spoke with a few thought leaders on the cybersecurity challenges manufacturers face and how they can best overcome them. Their suggestions and tips follow. Biggest security risks and challenges of information […]

Whether it’s the shift toward remote work or the growing importance of digital business, trends that have been around for years have only been accelerated by the COVID-19 pandemic. This holds true for the digital […]

In the course of everyday life, many of the decisions we make about information technology (IT) in a business context are simpler than they may seem at first glance. If people are buying mobile phones […]
How can companies defend against ransomware? Hayley Turner of Darktrace recommends leveraging AI to protect industrial environments

One of the most common questions I get asked while I am on a panel or after a conference presentation is on the topic of information technology/operational technology (IT/OT) convergence. A lot has been written […]

As organizations have been forced to transition to remote working, security professionals tasked with defending critical infrastructure and operational technology (OT) systems have been presented a broad set of challenges. New business measures, many of […]
Ransomware attacks can have a huge impact on OT systems and critical national infrastructure, says Hayley Turner of Darktrace

The Machinery Directive 2006/42 /EC had not been revised for 15 years and clearly needed updating. And so, a written proposal for the new machinery regulation was issued on April 21, 2021. However, since we do […]

In many industrial organizations, information technology (IT) and operational technology (OT) teams are from different planets. They have separate objectives, priorities, skills, metrics and even language. IT/OT convergence, or better said “connected industries,” requires these […]

What does information technology/operational technology (IT/OT) convergence mean? In the OT/IT cyber workspace, there are two types of companies – those seeking to converge and those that have never diverged. Both must change and both […]

Cyber attacks on critical infrastructure’s industrial control systems (ICS) are still on the rise due, for the most part, to the increase in cybercrime and geopolitical tensions – tensions that ironically were fueled by a […]

IT (information technology) and OT (operational technology) teams have historically and traditionally been separated over the years – and for good reason. Their priorities are different. Their approaches and processes are different. They are truly […]

In the last few years, ransomware has been running rampant, hitting private companies, government entities and everyone in between in a series of increasing bold strikes. Critical infrastructure has found itself squarely in the crosshairs […]
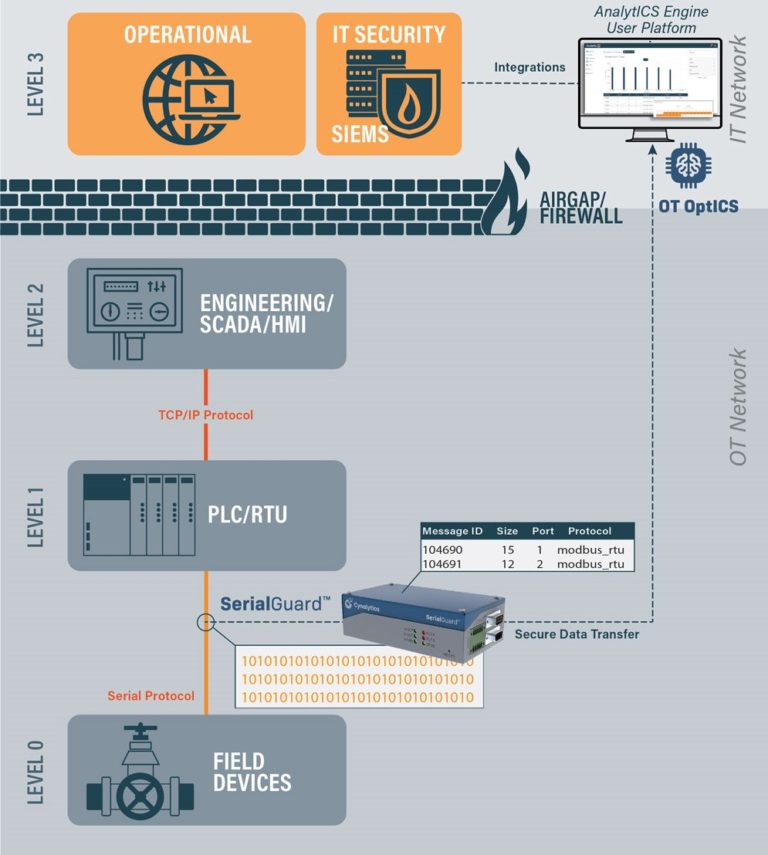
Historically, industrial control systems (ICS) could exist as a closed-loop, with an air-gapped network and a solid physical security program insulating them from the outside world. An operator could trust the integrity of their operations […]

Learning Objectives Hardening is a process whereby a computer is made more resistant to cyber intrusion from malicious attack and from accidental infection. Companies should update and patch their systems as often as they can. […]
As hackers become savvier, it’s important to supplement human and technological cyber defenses with AI, says David Masson of Darktrace

“Careful, Bill, you’ll give yourself a heart attack and ruin my vacation.” Sometimes worrying about today’s cybersecurity risks can feel like this. You implement a framework, identify vulnerabilities, evaluate those risks, address mitigations plans, and […]

A spate of recent cyberattacks on national critical infrastructure has brought production to a halt in the oil and gas industry, risked dangerous contamination of a water system in Florida, and hindered several local and […]
The age of IT/OT convergence is a good thing overall, but it has also introduced a new world of threat and accentuated the fragility of OT

Analysis performed by insurance carriers indicate that cyberattacks faced by manufacturing companies have grown by 30 times and technology companies by about 20 times since 2012. Within the last year, iconic companies from practically every […]
Improved technology, ease of access and the global pandemic have introduced an entirely new threat landscape for OT networks

The manufacturing industry is under increasing threat of cyber-related risks and attacks. In this past year, we saw a big shift in focused cybersecurity attacks on manufacturing companies. They jumped up from the eighth-largest target […]

The need for a national cybersecurity standard has become clear. Jim Crowley of Industrial Defender breaks down the cyber executive order

Featured articles in this eBook include stories on extending IT security to the plant floor, IT/OT collaboration driving digitalization and lessons learned from the SolarWinds attack.

On May 12, President Joe Biden signed an executive order to improve the nation’s cybersecurity and protect government networks

A Wall Street Journal article discusses a new set of attacks on electrical distribution providers. These attacks have targeted providers too small to be NERC regulated but may serve a critical infrastructure such as dams […]
One of the clearest “coming attractions” for operational technology (OT) is the application of traditional information technology (IT) systems or security management (ITSM) into the industrial controls environment. For nearly 20 years, IT teams have […]
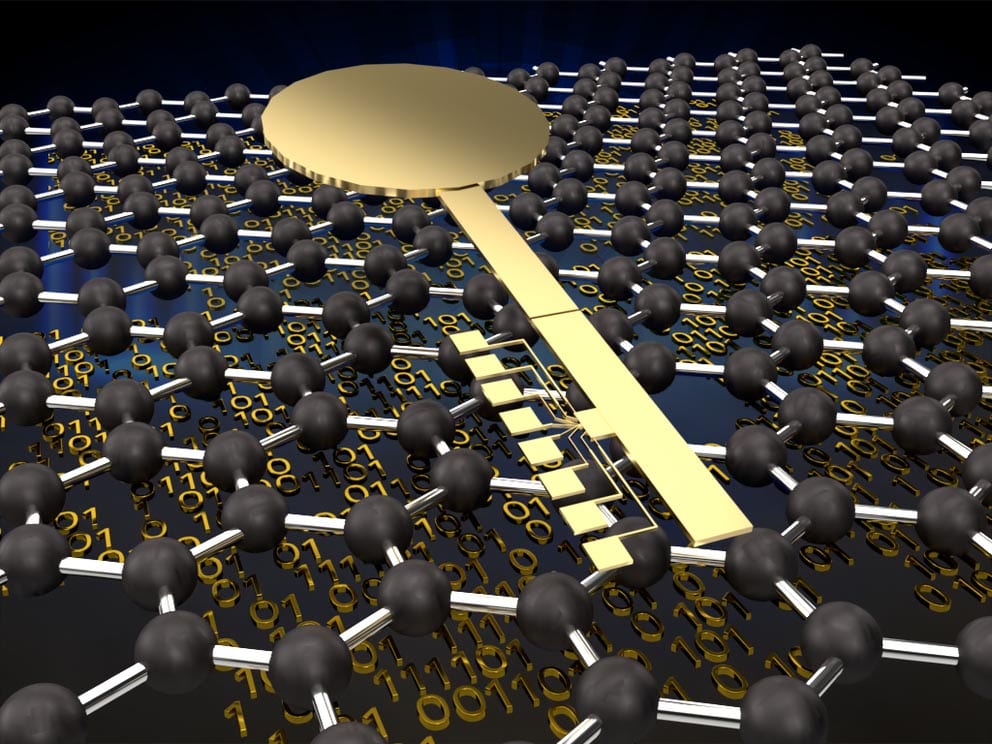
As more private data is stored and shared digitally, researchers are exploring new ways to protect data against attacks from bad actors. Current silicon technology exploits microscopic differences between computing components to create secure keys, […]
Securing operational technology (OT) networks and increasing network durability are key to enhancing operational resilience, as OT network protection still lags information technology (IT) cybersecurity. This article explains the reasons behind the lag, how this gap manifests […]

The SolarWinds hack has been a major topic of discussion of late. The software is used to monitor applications and networks at thousands of companies and most importantly US Federal and State government departments and […]

The convergence of information technology (IT) and operational technology (OT), the wider connectivity of OT with external networks, and the growing number of Industrial IoT (IIoT) devices, is helping to boost the efficiency of industrial […]

As marine renewable energy (MRE) developers prepare to deploy these technologies, efforts are underway to guard against cybersecurity threats that could threaten the function of a device and connected systems. Pacific Northwest National Laboratory (PNNL) created […]

As the technologies to bridge the divide between the worlds of information technology (IT) and operational technology (OT) within a plant have become more established, the digitalization of businesses has accelerated. The goal of this […]

IEC 62443 is the international standard for the security for industrial automation control systems (IACS). It was set up almost twenty years ago by a group of volunteers belonging to the SP99 Committee, established by […]

Hybrid networks, multi-cloud, Internet of Things (IoT), remote work and digital innovations are all driving more distributed networks and a much more expansive attack surface. The network perimeter that used to be so clearly defined now extends […]

A cyber kill chain provides a model for understanding the lifecycle of a cyber attack and helps those involved with critical infrastructure improve cybersecurity policies, technologies, training, and industrial control system (ICS) design. Learn 8 steps of one model.

Many wonder where to start when attempting to protect embedded systems in OT cybersecurity? Here are two pieces of information that can help guide you when understanding cybersecurity issues for embedded devices and the never-ending […]

Intellectual property (IP) is the lifeblood of today’s globally integrated microelectronics supply chain. Protecting confidential information is vital to electronics companies around the world. The industry’s central role in ensuring the national security and economic […]

Cybersecurity has become one of the most significant financial and reputational risks for an organization. Examples of the ever-increasing cybersecurity threats include: More than 22 government entities in Texas, Florida, Maryland and Georgia faced recent […]

Many industrial leaders operate their businesses with a false sense of security. Ransomware events such as the ones faced by Norsk Hydro, Hexion, and Momentive in 2019, which caused considerable operational disruption, serve as a […]

Who should be involved in the OT cybersecurity program? This is the first question for a reason. In many information technology (IT) organizations, the answer is clear. Security requires networking, endpoint, cloud, regulatory and other […]

Cybersecurity is critical as information technology (IT) and operations technology (OT) converge, which is the first step in making the transition between the two sides almost seamless.
The SolarWinds attack has been in the news a lot lately due to the widespread scope of the attack, which went beyond one company or one specific target industry. The SolarWinds attack affected more than […]
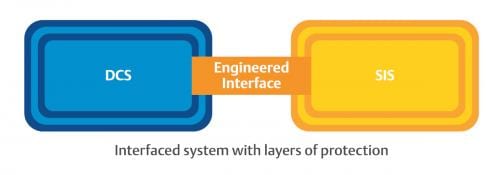
Integrated control and safety systems can simplify a strong cybersecurity posture for a manufacturer.
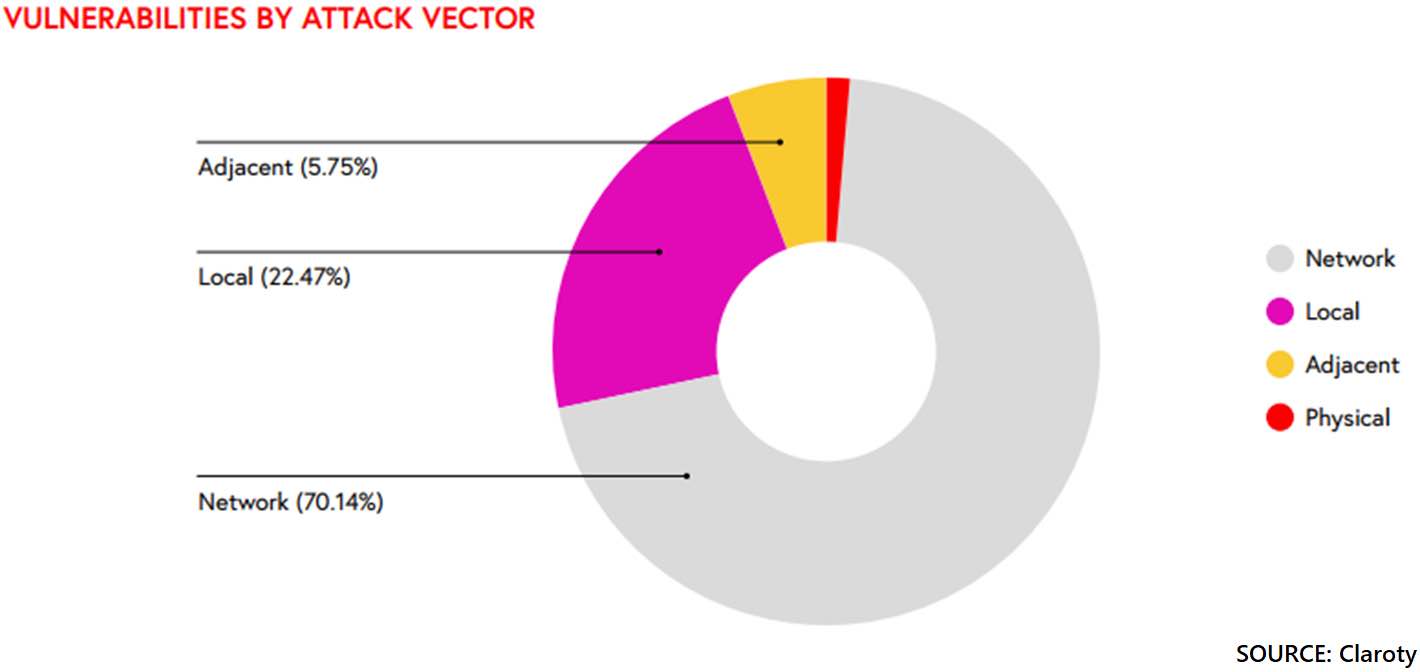
Learning Objectives ICS cybersecurity threats are increasing. Industrial networked devices, engineering workstation, remote sites may be sources of cybersecurity vulnerabilities. Standards and best practices, consistently applied, can decrease cybersecurity risk. It’s no secret information technology […]

It’s hard to know how much cybersecurity spending is enough to lower risk to an acceptable level. What is enough and what else is needed? A cybersecurity risk assessment (CRA) can help. Four tips are highlighted.

Overcome three OT/IT cybersecurity barriers and move towards cyber-resiliency in three cybersecurity steps.
Researchers warn smart manufacturing users and security professionals to be aware of advanced hackers.

Cybersecurity successes in 2020 will depend on information technology (IT) and operations (OT) coming together and collaborating and working past their differences.

Utilities need to embrace a risk-based approach to cybersecurity to match the existing basic-level of compliance. See four issues utilities are currently facing.
Converging information technology (IT) and operations technology (OT) does little to move end-to-end digitalization forward. What makes digitalization really work is successful OT and IT collaboration and an understanding of what the other side needs. See 7 tips for smarter OT and IT collaboration.

The distinction between digital and physical cybersecurity is vanishing, and the risks associated with connectivity have accelerated the need for new security protections in all aspects of manufacturing.
Understanding what devices a manufacturer has working on a network is important, but the next step is to take that knowledge and move toward prevention.
Safety and security have become more interconnected as systems once immune to cyber attacks are now becoming vulnerable in an increasingly interactive world.
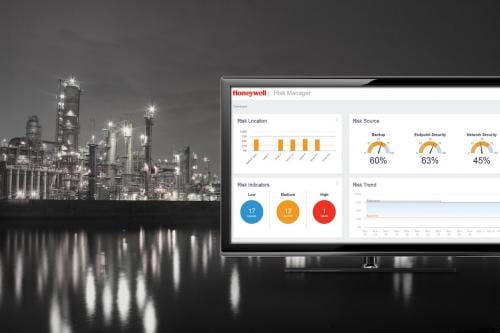
Cover story: A refinery installed a modern distributed control system (DCS) that automates and manages industrial cybersecurity tasks to reduce manual workflows, potential human error and overall company costs.

This eBook includes stories on generative AI payloads, how IT can help accelerate digital transformation and predictions for OT/ICS security.

OT cybersecurity is at greater risk of attacks than ever, and it requires a good, holistic plan that keeps workers educated and vigilant.

ICSP’s top 5 articles from March 2024 covered connecting IT and OT, regulating AI and a recently uncovered malware that targets OT systems.

A converged IT/OT SOC can help you defend against threats, but you definitely need buy-in throughout the organization.

Legacy OT systems, which used to operate in isolation from IT networks, are now exposed to modern cyber threats due to integration.

How secure are your OT systems? A converged IT/OT SOC can give you greater visibility and help defend against outside threats.

A converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

Eight key actions organizations can take to better protect themselves against threats targeting industrial operations and infrastructure.

Already used regularly for IT security, a converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

This webcast helped attendees learn about how organizations can create a converged IT/OT SOC. Additional questions were answered by Jim Cook.

If you’re ignoring OT and operational lifecycle management, some of your most important assets are probably insecure.

As employees take time off and businesses wind down over the holidays, cybercriminals ramp up. This creates a perfect storm of risk.

Dino Busalachi talks about purpose-built resources for OT and the new SEC ruling forcing companies to disclose cyberattacks.

New report finds a 400% increase in IoT and OT malware attacks, underscoring need for better zero-trust security for critical infrastructure.

Eric Byres talks about the improvement in regulatory frameworks and why OT/ICS systems are a juicy target for attackers.

Bringing SOAR and SOC standards to OT systems is critical as industrial cyberattacks increase in frequency and severity over time.

OT security must embrace the processes and protocols that IT put in place more than 20 years ago for enterprise networks.

The U.S. DOE, announced a new request for proposals (RFP) for up to $4.7 million to enhance the manufacturing cybersecurity landscape.

The U.S. government role in reducing OT cyber risk is bad in the short term, but it could be beneficial in the long term.

The system analyzes the likelihood that an attacker could thwart a certain security scheme to steal secret information.

What is the importance of OT managed services and how can organizations ensure around-the-clock monitoring and fortified OT security?

IT/OT convergence is vital for maximizing efficiency, but the ongoing trend toward convergence brings significant cybersecurity challenges.

CISA’s recent push for security by design and security by default could be a long-fought win for the OT community.

What is the best piece of advice cybersecurity practitioners give end users working to secure their connected OT devices?

What can the power industry learn from the evolution of NERC CIP in OT cybersecurity for improved reliability and security?

Many vulnerabilities have never been found to impact ICS/OT. That’s why it’s important to take a risk-based approach to cybersecurity.

Victor Atkins of 1898 and Co. discusses public-private partnerships, cybersecurity and critical infrastructure protection

Eric Byres talked to the ICS Pulse Podcast about the value of SBOMs, why OT is getting weaponized and reasons for optimism.

Eric Byres of aDolus discusses the themes at S4, managing vulnerabilities and the difference between cyber criminals and nation-state actors.

On the first day of the RSA Conference, Rockwell Automation attempted to help IT professionals secure OT systems.

Organizational challenges need to be addressed to achieve IT/OT convergence, from political and cultural barriers to technical complexities.

As the risk of cyber attacks on operational technology (OT) systems grows, so does the cost of OT cyber insurance.

Schreiber Foods, a part of the food and agriculture sector, was hit by a cyberattack on their computer systems used for organizing raw milk

As the world becomes digitized, businesses must understand the importance of maintaining strong IT and OT security to prevent attacks.

Tabletop exercises are a great way to help prepare an incident response plan. These exercises also help push IT/OT convergence forward.

Businesses that are over-reliant on IT to fortify OT security put themselves at risk of lost data, downtime and physical safety hazards.

Food and beverage manufacturers are wrestling with how to implement stronger manufacturing cybersecurity measures.

A CDV index can help measure the cyber preparedness and OT protection of a plant and critical infrastructure from cyber crime.

Looking to sell a security product to the OT market? It should require no changes to the ICS and have no impact on physical processes.

New emphasis is being placed on reducing incident severity across OT and IoT sectors, tapping into the strong safety culture of industrial environments.

A natural gas operator was hit by a ransomware attack via a spear-phishing campaign that resulted in a two-day shutdown of operations.

CISA and other organizations have released multiple notices about the importance of prioritizing vulnerabilities based on their risk.

Velta Technology and TXOne Networks offer a solution to the potential ICS and revenue disruption of the Microsoft DCOM hardening patch.

Using threat intelligence for visibility into threats to your OT network is a critical step in building a mature OT network defense.

Shadow OT is when security teams have an incomplete picture of what’s happening inside their operational systems.

We’ve seen several industrial companies that have learned a lesson from not applying industrial cybersecurity to protect their ICS networks.

Technology-enabled vulnerability assessment gathers detailed visibility of the risks of the environment and prioritizes those risks.

Enterprises have realized the importance of attack surface management to identify, prioritize and minimize threat vectors in an environment.

Jordan Lutz of Rockwell Automation speaks about recognizing the need for cyber resilience, IT/OT convergence and where to get started.

OT asset management and OT asset visibility are used similarly in the cybersecurity industry because there is not a delineation between them.

SIEM systems have the ability to collect, categorize and filter, which creates tailored security alerts for security operators.

By understanding people, processes, technologies, roles and procedures from an IT and OT perspective, you can create better digital safety.

There still is a lack of understanding as to the importance of cybersecurity, as well as the role that cybersecurity insurance should play.

How do organizations get their engineers and technicians up to speed with the knowledge and strategies needed to ensure OT security?

CFE Media brought industry experts together to discuss IT/OT convergence and why it is such an important part of cybersecurity.

What are the dynamics facing today’s OT engineers, whether they’re new to the industry or bringing years of experience?

ICS/OT infrastructure security is different in many ways from IT security, and one of the main reasons is the reverse confidentiality triad.

All organizations should ensure that cybersecurity risks (CSRM) receive appropriate attention as they conduct their ERM program.

As AI becomes more of a factor in industrial cybersecurity, what role will it play in defending supply chains and other networks?

Cybersecurity Insights There is a greater risk of cybersecurity attack against operational technology (OT) targets as machines become integrated with information technology (IT) systems. Consulting with subject matter experts (SMEs) and system integrators who are […]

IT and OT Insights IT and OT should be assessed differently from one another. However, if there is a set list of tasks to do with them working together, it must get done, which allows […]

Cybersecurity insights Ransomware is a type of cyberattack where a threat actor steals data from a company and holds it for ransom — although companies have been known to pay the ransom and get nothing […]

There has been a lot of talk lately about how to secure a budget from the C-suite. While most people seem to understand the need for cybersecurity, many companies and organizations are still lagging behind, […]

Solid asset management sits at the foundation of all cybersecurity activities. Enumerating assets into a solid inventory, tracking their current state – including configurations and versions deployed, and mapping their relationships all go a long […]

Cybersecurity insights The 2021 IBM Security Data Breach Report outlines key factors contributing to the rising costs of data breaches for industries all over the world. Health care has continued to be the most affected […]

In recent years, private companies and critical infrastructure alike have felt the full force of cyberattacks. This has put cybersecurity on the forefront of everyone’s mind, as people try to remain a step ahead of […]

As cybersecurity risk and complexity continue to grow, how is the long-standing gap between IT and OT evolving? Dragos asked four industrial security leaders that question and more in our recent webinar, What’s Behind the […]

The White House issued a statement by President Biden urging the critical infrastructure community to immediately strengthen their defenses based on their evolving understanding of Russian intent to use cyber attacks. Many of our customers are […]

The U.S. government has focused on trying to strengthen cybersecurity across all critical infrastructure sectors in recent years with actions such as the 100-day sprint and the executive order. But are these actions from the […]

Since the COVID-19 pandemic hit, the way people work has changed, opening a new world of vulnerabilities. High-profile attacks on companies like Colonial Pipeline, SolarWinds and Kaseya have put cybersecurity on everyone’s radar. But in […]

Dragos recently published the Dragos 2021 Year In Review report, which highlighted four key findings within the operational technology (OT) cyber threat landscape. This blog continues the series that expands on each of these findings, […]

In information technology (IT), organizations have options to choose from to discover and aggregate asset information. In operation technology (OT), security asset management – discovery, inventory, risk evaluation, etc. – is more difficult given the […]

Richard Robinson discusses how to protect legacy OT assets and the role machine learning and artificial intelligence can play

Chief information security officers (CISOs) and directors of cybersecurity at industrial organizations continue to be frustrated at the challenge of applying core information technology (IT) security principles to operational technology (OT) environments. This runs the […]

On April 4, 2022, Secretary of State Antony Blinken released a statement announcing the creation of a “new” federal bureau — the Bureau of Cyberspace and Digital Policy (CDP). Even though the organization is the […]

As the Russia-Ukraine war continues, Russian cyber threat actors have been launching their attacks on the Ukrainian government. Given the widespread western support that Ukraine has received — in the form of money, weapons and harsh […]

Dragos, Inc., a leader in cybersecurity for industrial control systems (ICS)/operational technology (OT) environments, recently released its fifth annual Dragos ICS/OT Cybersecurity Year in Review (YIR) report, the most comprehensive report on cyber threats facing […]

To effectively combat pervasive cyberthreats like ransomware, organizations need to centralize their detection and response efforts. Oftentimes, they will turn to an endpoint detection and response (EDR) tool or managed detection and response (MDR) to achieve […]

Assessing and monitoring the security of operation technology (OT) systems can be aided by conducting an OT cybersecurity threat risk assessment (TRA). The process is fundamental to the protection of OT/critical infrastructure (CI) and key resources […]

Protecting information technology (IT) and operational technology (OT) networks is crucial to safeguarding the manufacturing industry. As part of the SecureAmerica’s Institute’s (SAI) nationwide initiative to empower the U.S. manufacturing enterprise, SAI and partners at […]

With the announcement of a new security directive coming from TSA for the rail industry, cybersecurity has been getting a lot of deserved attention from rail operators lately. Properly managing cyber risks in this sector of […]

Protecting key resources and critical infrastructure (CI), such as healthcare, finance, transportation, telecommunications, energy, and water/wastewater is essential to security, public health and safety, economic vitality and our overall way of life. Recent ransomware attacks, […]

Technology, AI and other cybersecurity measures can help protect businesses, but it’s nearly impossible to block every threat out there. One safety net stepping into the void to help protect companies financially is cybersecurity insurance.

In a rapidly changing world, we are grateful technology allows industrial organizations to operate their security and operational technology (OT) systems management quite effectively from a remote environment. Although it was not designed for a […]

Most companies realize that implementing a cybersecurity maturity model is a smart move and a necessity in today’s world. The challenge for most companies is, where do they start? Let’s walk through the process to […]

Nearly every week, the cybersecurity community buzzes around a newly discovered vulnerability or breach. December’s alert for the CVE-2021-4428 vulnerability in Apache Foundation’s Log4j software is no different. Also known as the Log4Shell vulnerability, it is present […]

The ISA/IEC 62443 cybersecurity documents contain a lot of guidance that easily overwhelms or confuses people when unpacking its components. It covers a range of topics including how to: Build a Cybersecurity Management System (CSMS) […]

The NERC CIP standards are the mandatory security standards that apply to entities that own or manage facilities that are part of the U.S. and Canadian electric power grid. They were initially approved by the Federal […]

Operational technology (OT) has become a heightened target for cybersecurity attacks. The need to address OT cyber risks has never been greater. New threats are emerging every day – both targeted as well as untargeted […]

On July 20, 2021, the Cybersecurity and Infrastructure Security Agency (CISA) and the Transportation Security Administration (TSA) sent a directive to the owner/operators of critical pipelines in the United States clarifying and further defining the initial […]

As industrial cybersecurity and critical infrastructure breaches mount, senior information security officers (SISOs), information technology (IT) directors, heads of engineering and others who lead cybersecurity initiatives are increasingly required to explain their cyber risks and […]

Amidst the COVID-19 pandemic, system integrators in the industrial sector moved toward one of the most influential changes in recent history, industrial digital transformation (industrial DX). However, before engaging, it is important to understand what […]

Modern industrial and critical infrastructure organizations rely on the operational technology (OT) environment to produce their goods and services. Beyond traditional information technology (IT) operations that use servers, routers, PCs and switches, these organizations also […]

Current industrial automation and control system (IACS) technology uses a blend of traditional control hardware and software with commercial off-the-shelf (COTS) information technology (IT) components (see Figure 1). This allows system designers to leverage an […]

Information technology (IT) and operational technology (OT) teams have historically been separated over the years — and for good reason. Their priorities are different. Their approaches and processes are different. They inhabit different worlds of […]

What is the NIS Directive? As part of the EU cybersecurity strategy, the European Commission first proposed the EU Network and Information Security (NIS) Directive in 2016, which was the first piece of EU-wide cybersecurity legislation. […]

Digital transformation might be great for business, but when it comes to protecting legacy OT systems, it can cause major problems

Convergence between information technology (IT) and operational technology (OT) networks requires a wide approach in order to ensure proper visibility and security. The need to control OT processes to optimize business has led to a […]

One of the most common questions we are asked at Splunk is how we work together with technologies like Industrial Defender. The discussion normally revolves around what it really means to protect and secure an […]

Matt Leipnik, lead industrial cybersecurity specialist for Nexus Controls, discusses why it’s important to create a culture of cybersecurity

Cyberattacks against industrial control systems (ICS) are growing in number and sophistication each year. The potential financial impacts from these attacks are growing in parallel. Major attacks, like the Colonial Pipeline and JBS meat plant incidents, have served as […]

More than two thousand years ago, ancient tactician Sun Tzu famously observed that, “If you know the enemy and know yourself, you need not fear the result of a hundred battles.” While the world looks […]

It’s no secret that industrial organizations are at the forefront of cybersecurity attacks. A recent report by IBM X-force revealed the manufacturing industry jumped from the eighth most targeted industry to the second most targeted […]

How do you get buy-in for cybersecurity? And once you have that buy-in, how do you scale? Matt Leipnik of Nexus Controls offers some answers

There have been many papers and blogs written recently about how to ask your chief information security officer (CISO) for a cybersecurity budget or how operational technology (OT) personnel should engage with CISOs to ensure […]

Suzanne Gill of Control Engineering Europe spoke with a few thought leaders on the cybersecurity challenges manufacturers face and how they can best overcome them. Their suggestions and tips follow. Biggest security risks and challenges of information […]

Whether it’s the shift toward remote work or the growing importance of digital business, trends that have been around for years have only been accelerated by the COVID-19 pandemic. This holds true for the digital […]

In the course of everyday life, many of the decisions we make about information technology (IT) in a business context are simpler than they may seem at first glance. If people are buying mobile phones […]

How can companies defend against ransomware? Hayley Turner of Darktrace recommends leveraging AI to protect industrial environments

One of the most common questions I get asked while I am on a panel or after a conference presentation is on the topic of information technology/operational technology (IT/OT) convergence. A lot has been written […]

As organizations have been forced to transition to remote working, security professionals tasked with defending critical infrastructure and operational technology (OT) systems have been presented a broad set of challenges. New business measures, many of […]

Ransomware attacks can have a huge impact on OT systems and critical national infrastructure, says Hayley Turner of Darktrace

The Machinery Directive 2006/42 /EC had not been revised for 15 years and clearly needed updating. And so, a written proposal for the new machinery regulation was issued on April 21, 2021. However, since we do […]

In many industrial organizations, information technology (IT) and operational technology (OT) teams are from different planets. They have separate objectives, priorities, skills, metrics and even language. IT/OT convergence, or better said “connected industries,” requires these […]

What does information technology/operational technology (IT/OT) convergence mean? In the OT/IT cyber workspace, there are two types of companies – those seeking to converge and those that have never diverged. Both must change and both […]

Cyber attacks on critical infrastructure’s industrial control systems (ICS) are still on the rise due, for the most part, to the increase in cybercrime and geopolitical tensions – tensions that ironically were fueled by a […]

IT (information technology) and OT (operational technology) teams have historically and traditionally been separated over the years – and for good reason. Their priorities are different. Their approaches and processes are different. They are truly […]

In the last few years, ransomware has been running rampant, hitting private companies, government entities and everyone in between in a series of increasing bold strikes. Critical infrastructure has found itself squarely in the crosshairs […]

Historically, industrial control systems (ICS) could exist as a closed-loop, with an air-gapped network and a solid physical security program insulating them from the outside world. An operator could trust the integrity of their operations […]

Learning Objectives Hardening is a process whereby a computer is made more resistant to cyber intrusion from malicious attack and from accidental infection. Companies should update and patch their systems as often as they can. […]

As hackers become savvier, it’s important to supplement human and technological cyber defenses with AI, says David Masson of Darktrace

“Careful, Bill, you’ll give yourself a heart attack and ruin my vacation.” Sometimes worrying about today’s cybersecurity risks can feel like this. You implement a framework, identify vulnerabilities, evaluate those risks, address mitigations plans, and […]

A spate of recent cyberattacks on national critical infrastructure has brought production to a halt in the oil and gas industry, risked dangerous contamination of a water system in Florida, and hindered several local and […]

The age of IT/OT convergence is a good thing overall, but it has also introduced a new world of threat and accentuated the fragility of OT

Analysis performed by insurance carriers indicate that cyberattacks faced by manufacturing companies have grown by 30 times and technology companies by about 20 times since 2012. Within the last year, iconic companies from practically every […]

Improved technology, ease of access and the global pandemic have introduced an entirely new threat landscape for OT networks

The manufacturing industry is under increasing threat of cyber-related risks and attacks. In this past year, we saw a big shift in focused cybersecurity attacks on manufacturing companies. They jumped up from the eighth-largest target […]

The need for a national cybersecurity standard has become clear. Jim Crowley of Industrial Defender breaks down the cyber executive order

Featured articles in this eBook include stories on extending IT security to the plant floor, IT/OT collaboration driving digitalization and lessons learned from the SolarWinds attack.

On May 12, President Joe Biden signed an executive order to improve the nation’s cybersecurity and protect government networks

A Wall Street Journal article discusses a new set of attacks on electrical distribution providers. These attacks have targeted providers too small to be NERC regulated but may serve a critical infrastructure such as dams […]

One of the clearest “coming attractions” for operational technology (OT) is the application of traditional information technology (IT) systems or security management (ITSM) into the industrial controls environment. For nearly 20 years, IT teams have […]

As more private data is stored and shared digitally, researchers are exploring new ways to protect data against attacks from bad actors. Current silicon technology exploits microscopic differences between computing components to create secure keys, […]

Securing operational technology (OT) networks and increasing network durability are key to enhancing operational resilience, as OT network protection still lags information technology (IT) cybersecurity. This article explains the reasons behind the lag, how this gap manifests […]

The SolarWinds hack has been a major topic of discussion of late. The software is used to monitor applications and networks at thousands of companies and most importantly US Federal and State government departments and […]

The convergence of information technology (IT) and operational technology (OT), the wider connectivity of OT with external networks, and the growing number of Industrial IoT (IIoT) devices, is helping to boost the efficiency of industrial […]

As marine renewable energy (MRE) developers prepare to deploy these technologies, efforts are underway to guard against cybersecurity threats that could threaten the function of a device and connected systems. Pacific Northwest National Laboratory (PNNL) created […]

As the technologies to bridge the divide between the worlds of information technology (IT) and operational technology (OT) within a plant have become more established, the digitalization of businesses has accelerated. The goal of this […]

IEC 62443 is the international standard for the security for industrial automation control systems (IACS). It was set up almost twenty years ago by a group of volunteers belonging to the SP99 Committee, established by […]

Hybrid networks, multi-cloud, Internet of Things (IoT), remote work and digital innovations are all driving more distributed networks and a much more expansive attack surface. The network perimeter that used to be so clearly defined now extends […]

A cyber kill chain provides a model for understanding the lifecycle of a cyber attack and helps those involved with critical infrastructure improve cybersecurity policies, technologies, training, and industrial control system (ICS) design. Learn 8 steps of one model.

Many wonder where to start when attempting to protect embedded systems in OT cybersecurity? Here are two pieces of information that can help guide you when understanding cybersecurity issues for embedded devices and the never-ending […]

Intellectual property (IP) is the lifeblood of today’s globally integrated microelectronics supply chain. Protecting confidential information is vital to electronics companies around the world. The industry’s central role in ensuring the national security and economic […]

Cybersecurity has become one of the most significant financial and reputational risks for an organization. Examples of the ever-increasing cybersecurity threats include: More than 22 government entities in Texas, Florida, Maryland and Georgia faced recent […]

Many industrial leaders operate their businesses with a false sense of security. Ransomware events such as the ones faced by Norsk Hydro, Hexion, and Momentive in 2019, which caused considerable operational disruption, serve as a […]

Who should be involved in the OT cybersecurity program? This is the first question for a reason. In many information technology (IT) organizations, the answer is clear. Security requires networking, endpoint, cloud, regulatory and other […]

Cybersecurity is critical as information technology (IT) and operations technology (OT) converge, which is the first step in making the transition between the two sides almost seamless.

The SolarWinds attack has been in the news a lot lately due to the widespread scope of the attack, which went beyond one company or one specific target industry. The SolarWinds attack affected more than […]

Integrated control and safety systems can simplify a strong cybersecurity posture for a manufacturer.

Learning Objectives ICS cybersecurity threats are increasing. Industrial networked devices, engineering workstation, remote sites may be sources of cybersecurity vulnerabilities. Standards and best practices, consistently applied, can decrease cybersecurity risk. It’s no secret information technology […]

It’s hard to know how much cybersecurity spending is enough to lower risk to an acceptable level. What is enough and what else is needed? A cybersecurity risk assessment (CRA) can help. Four tips are highlighted.

Overcome three OT/IT cybersecurity barriers and move towards cyber-resiliency in three cybersecurity steps.

Researchers warn smart manufacturing users and security professionals to be aware of advanced hackers.

Cybersecurity successes in 2020 will depend on information technology (IT) and operations (OT) coming together and collaborating and working past their differences.

Utilities need to embrace a risk-based approach to cybersecurity to match the existing basic-level of compliance. See four issues utilities are currently facing.

Converging information technology (IT) and operations technology (OT) does little to move end-to-end digitalization forward. What makes digitalization really work is successful OT and IT collaboration and an understanding of what the other side needs. See 7 tips for smarter OT and IT collaboration.

The distinction between digital and physical cybersecurity is vanishing, and the risks associated with connectivity have accelerated the need for new security protections in all aspects of manufacturing.
Understanding what devices a manufacturer has working on a network is important, but the next step is to take that knowledge and move toward prevention.

Safety and security have become more interconnected as systems once immune to cyber attacks are now becoming vulnerable in an increasingly interactive world.

Cover story: A refinery installed a modern distributed control system (DCS) that automates and manages industrial cybersecurity tasks to reduce manual workflows, potential human error and overall company costs.
Keep your finger on the pulse of top industry news
This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.