
eBook: Cybersecurity in Smart Factories – Spring Edition
This eBook includes stories on the steps to developing a smart factory and why smart buildings are often insecure.

This eBook includes stories on the steps to developing a smart factory and why smart buildings are often insecure.

This eBook, full of our popular Throwback Attacks, includes stories on how a Florida teen infiltrated the DoD and much more.
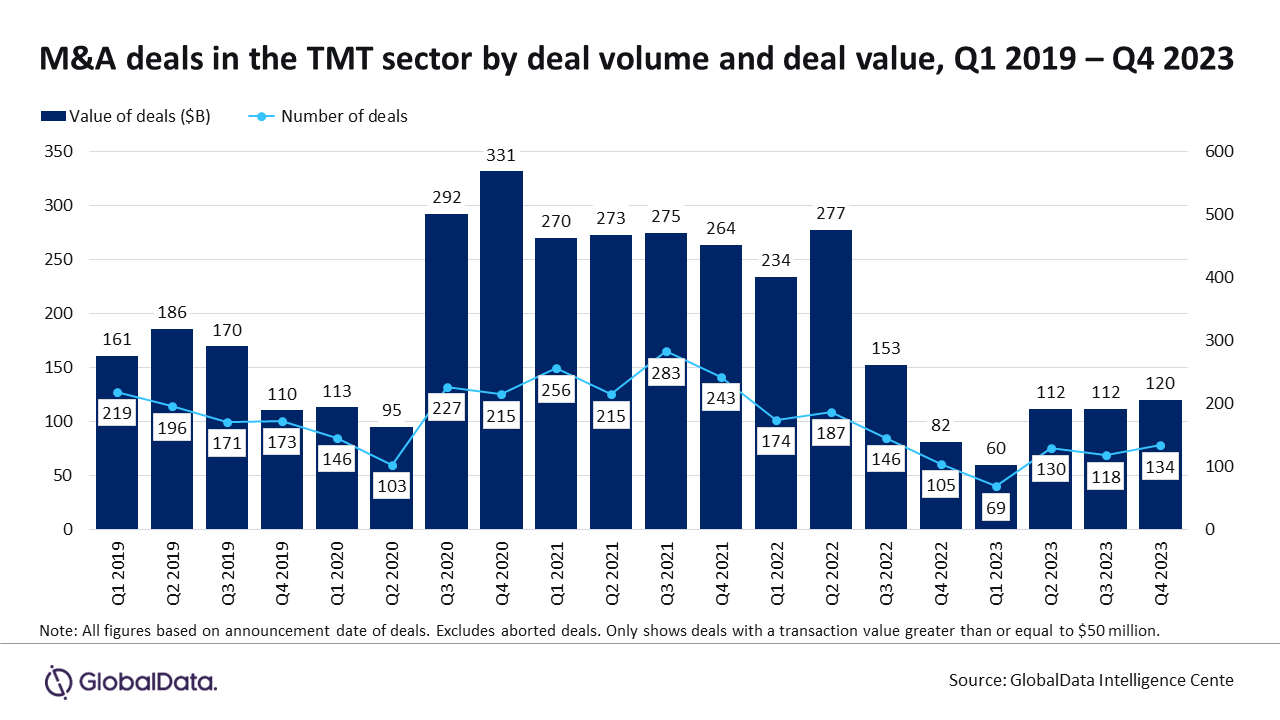
With escalating cyber threats, companies are prioritizing investments in cybersecurity capabilities, leading to a surge in M&A deals in 2023.

This eBook includes stories on how NotPetya took down shipping giant Maersk and which OT/ICS devices are the riskiest.

The top 5 articles from January 2024 covered everything from SCADA security to IT/OT convergence to operational lifecycle management.

Our top 5 pieces from December 2023 covered bringing SOC/SOAR standards to OT, mobile device management and more.

In this highly interactive webcast, Jeff McDaniel of Airgap will demonstrate how easy it is to close the identity gap for OT.

Already used regularly for IT security, a converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

This eBook includes stories on how you can detect ransomware faster and how tabletop exercises can help prepare your employees.

When evaluating an organization’s security objectives, you should understand how those objectives align to not overshoot your security target.

Debbie Gordon talks about why security is everyone’s job, how AI won’t replace humans and why “Office Space” is a cybersecurity movie.

In this webcast, learn how a standards-based, defense-in-depth approach can be effective in protecting critical services and infrastructures.
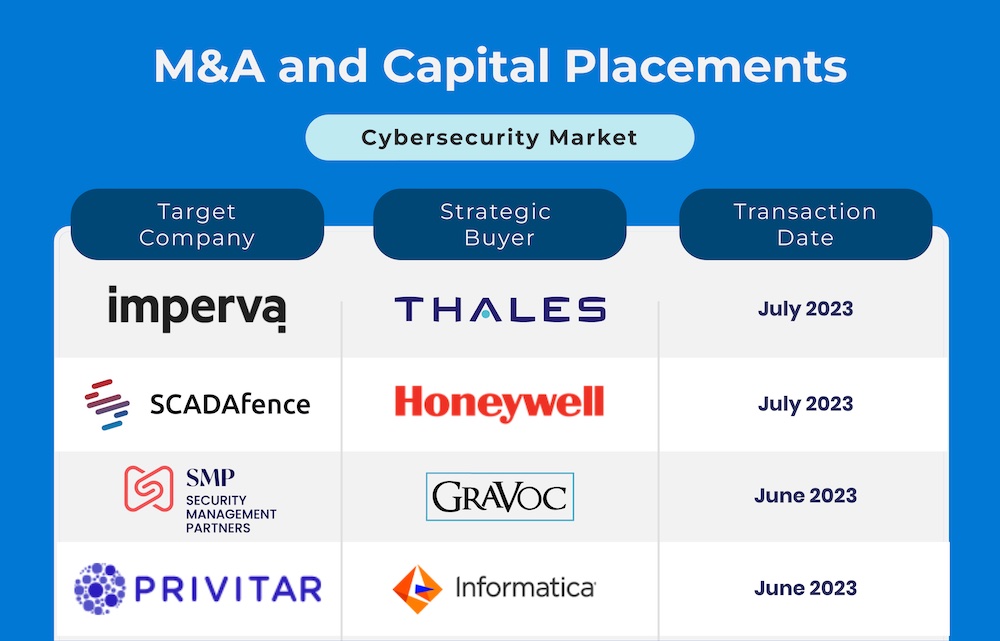
2023 is continuing to demonstrate resiliency in the mergers & acquisitions and capital placement markets for cybersecurity companies.

A Texas A&M professor is looking to move malware detection from software to hardware, creating hardware-integrated protection.

An Idaho National Lab intern developed a cybersecurity research tool, AcCCS, that could improve the security of electric vehicle charging.

Research identified the riskiest OT and ICS devices to key critical infrastructure industries of manufacturing, utilities and transportation.
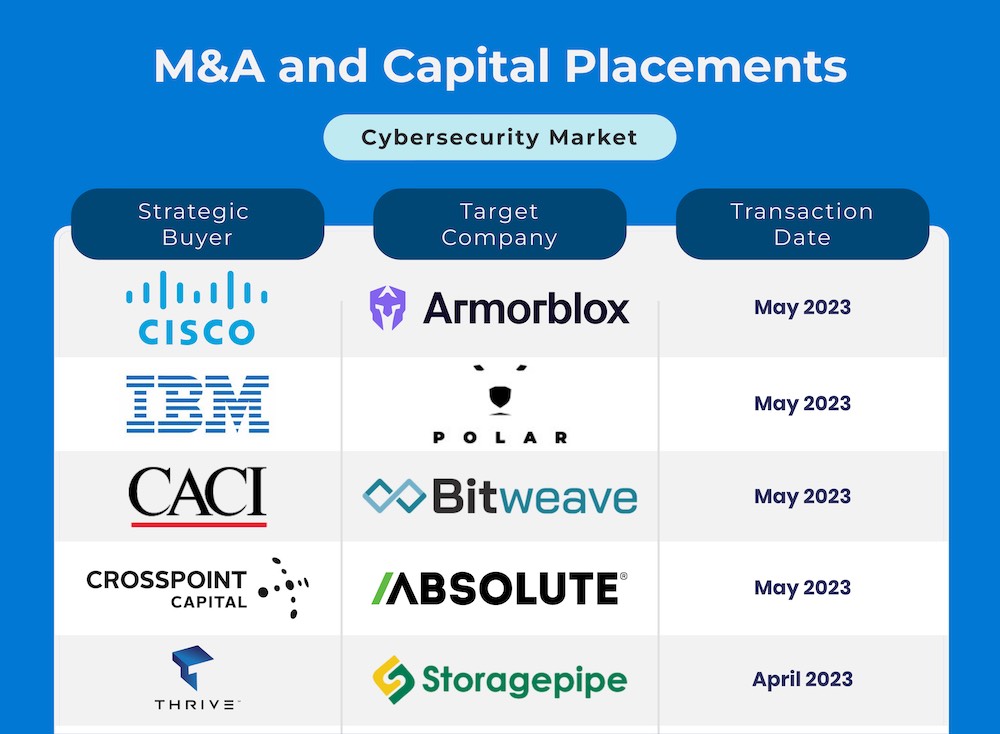
Spring 2023 is continuing to show strength and consistency in terms of cybersecurity mergers & acquisitions and capital placement.

Clint Bundy, Managing Director with Bundy Group, was recently interviewed by Gary Cohen and Tyler Wall, the hosts of the Industrial Cybersecurity Pulse Podcast. The topic was to discuss the mergers and acquisitions (M&A) and […]

This webcast will examine the rising tide of ransomware and how you can protect OT/ICS, without risking human safety or creating downtime.

This eBook includes stories on how what you need to know about the NERC CIP standards and how to minimize cybersecurity risk in manufacturing.

Purdue researchers are taking aim at the growing surge of supply chain attacks directed at third-party software suppliers and vendors.

ICSP’s top 5 articles from May 2023 covered incident response, nation-state attacks on the energy sector and the cybersecurity skills gap.
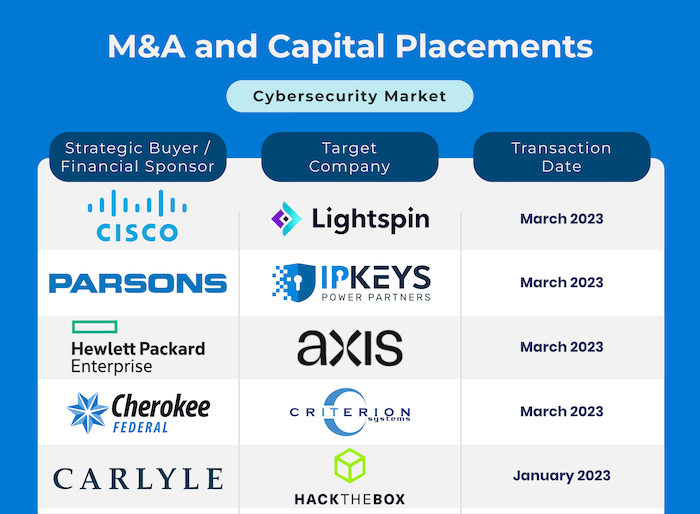
The first few months of 2023 witnessed a large number of mergers and acquisitions and capital placement activity in the cybersecurity segment.

The first day of the RSA event featured several keynotes highlighting the potential of AI and private-public partnerships in cybersecurity.

Dragos released its annual Year in Review report about the state of industrial cybersecurity. The ICSP Podcast talked to Ben Miller about it.

The top 5 ICSP articles from March 2023 covered critical infrastructure, the Biden National Cyber Strategy and IT/OT convergence.

SOOS announced the launch of its public SBOM database, where anyone can download an SPDX or CycloneDX SBOM for over 54 million packages.

Sam May of Steel Root talked to the ICS Pulse Podcast about the cybersecurity skills gap and how to combat it.

ICS Pulse’s top 5 articles from February 2023 covered the value of tabletop exercises, why IT/OT convergence requires prioritization and more.
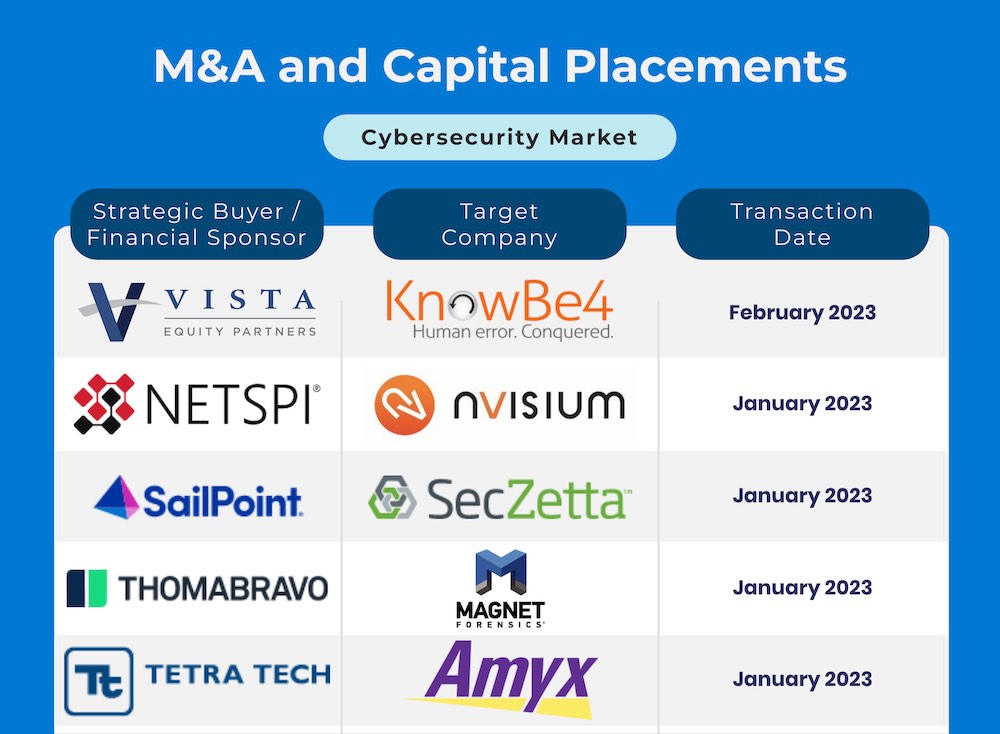
The cybersecurity mergers segment is well positioned for another robust year in terms of M&A and capital placement activity.

The Wall Street Journal held a webinar, “Mitigating Cyber Risk,” to discuss cybersecurity best practices in an evolving industry

ICS Pulse’s top 5 articles from January 2023 covered the Microsoft DCOM hardening patch, insider attacks, the new CDV index and more.

In this webcast, Jay Williams, CEO of Industrial Defender, will discuss how to secure a cybersecurity budget and get buy-in from the C-suite.

This eBook includes stories on why supply chain attacks create a target-rich environment and why supply chain and ransomware are a toxic mix.

In this mergers & acquisitions update, there is significantly more demand than supply of acquisition opportunities in the cyber sector.

This eBook includes stories on how outdated policies put systems at risk and what’s being done to protect the grid from ransomware.

Employer demand for cybersecurity workers continues to strain talent availability according to new data from CyberSeek.

Purdue works to guide the security investments of utility companies to parts of the power grid at risk of causing a blackout if hacked.

As industrial devices become more connected, cyber risk is exploding. We’re proud to announce the new, weekly ICS Pulse Podcast.

This eBook includes stories on the impact of the CMMC and how supply chain attacks are changing the nature of ICS security.

Critical infrastructure provides the essential services that keep American society running. A cyberattack on these systems could create a destabilizing effect on the nation’s physical security, economic security, public health and/or safety. Featured articles in this […]
Smart Chip Insights A smart chip must be able to communicate data between all technology, which often consumes a lot of energy and requires security measures to keep that data safe. Researchers found that using […]

Last fall, LSU announced a new initiative named FIREStarter, which would provide students with training in cybersecurity and threat analysis through the creation of a lab for cyber range exercises. These exercises would be conducted […]

The adoption of Industry 4.0 technologies is increasing efficiency and profitability across industrial control system (ICS) environments, making data available from myriad sources, and employing advanced software tools to analyze information. This gives plant staff […]

In recent months, a spate of high-profile attacks on everyone from private companies to critical infrastructure has put cybersecurity squarely on the radar. But while most seem to understand the need for cybersecurity, many companies […]

Every vendor is telling you to buy their new AI/ML product to secure your systems, ICS or not. Can AI/ML solve your cybersecurity problems
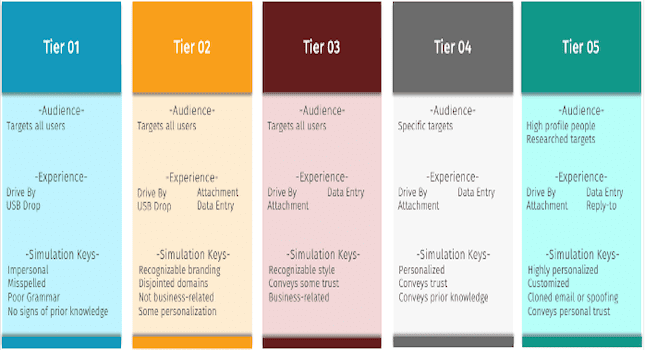
The goal of internal benchmarking is often to gain a better understanding of those entities in your company that are doing well and vice versa. With phishing simulations, you’re able to analyze the results to […]

In this webcast, UL’s cyber experts discuss Industry 4.0 cybersecurity and how you can mitigate security risks and ensure compliance

William Shakespeare might have been talking about Apple’s recently released M1 chip via his prose in “A Midnight Summer’s Dream”: “And though she be but little, she is fierce.” The company’s software runs on the […]

This webcast on June 14 will show you why OT attacks are on the rise and how MITRE ATT&CK can help you defend against them

Cybersecurity attacks against manufacturing have increased in the last several years and will continue to do. While a majority have a financial motive rather than corporate espionage, the result is the same: It costs a […]

While the mergers and acquisitions (M&A) and capital raise markets have a wary eye on numerous potential macroeconomic headwinds — the Ukrainian war, inflation, the great resignation — the cybersecurity market continues to demonstrate its […]

This webcast looks at why supply chain attacks are on the rise and what your organization can do to protect against them

Researchers have developed a technique that leverages hardware and software to improve file system security for next-generation memory technologies called non-volatile memories (NVMs). The new encryption technique also permits faster performance than existing software security […]

As smartphones have grown more sophisticated over the years, so have their accompanying security measures for identity verification. Simple passwords have been replaced by thumbprints and facial recognition. However, those methods do not solve the […]

If a sticker on a banana can make it scan as a toaster, how might strategic vandalism warp how an autonomous vehicle perceives a stop sign? Now, an immune-inspired defense system for neural networks can […]

Daily life is happening increasingly online. There isn’t a big enough cybersecurity workforce in the U.S. to keep everyone safe. That’s the problem that nearly $6 million in new funding will help the University of […]

Cyber incidents have become a major problem for large corporations, small businesses and individuals alike. No one is immune from a potential attack, which means everyone in an organization must play a role in safeguarding […]

It’s critical to understand what industrial control systems (ICS) are, why they are vital and outline the unique challenges of securing ICS. What are industrial control systems? Industrial control systems are used for managing, directing, […]

One of the biggest challenges we consistently hear from security awareness professionals is how to effectively engage, train, and secure a remote workforce. Many of us thought remote working would end in 2021, that life […]

IUPUI will train diverse undergraduate and graduate students to become the next generation of cybersecurity engineers who will help the U.S. respond to national security needs, thanks to a $3.7 million grant from the National […]

The year 2021 was the year cybersecurity went mainstream. High-profile strikes such as the Colonial Pipeline ransomware attack in May 2021 and the SolarWinds supply chain hack resulted in a new U.S. Executive Order and […]

Industrial cybersecurity remains critically important to subscribers of Control Engineering, Plant Engineering, and other CFE Media and Technology publications. Hot topics in 2021 included analysis of prior cybersecurity attacks, malware, rasomware and physical plant damage […]

When cybersecurity initiatives originate with the board of directors, people pay attention. So what are some steps a board can take to keep their charges ahead of the hackers? As industrial cybersecurity and critical infrastructure […]
Cyberattacks have increased since the COVID-19 pandemic. While information technology (IT)/operational technology (OT) convergence remains a hot topic, the conversation about cybersecurity for industrial control systems (ICS) has fallen on deaf ears in some cases. […]

One of my first tasks after leaving the National Security Administration (NSA) for private industry in the early ’90s was to write my new company’s information security policy. I’m not sure my previous job as […]

Regardless of their goal or intent, hackers’ general modus operandi is about disruption and causing chaos for a company, organization or other entity. Sometimes, the hackers try to increase the lye in a water filtration […]

Many experts say companies should spend between 10 and 15% of their annual information technology (IT) budget on cyber defense, but the reality is few companies are spending even that much. While most organizations understand […]

Over the past year, there has been a sharp increase in cyberattacks using malware to target the systems of critical infrastructure such as utility companies, government agencies and organizations that provide services and products we […]
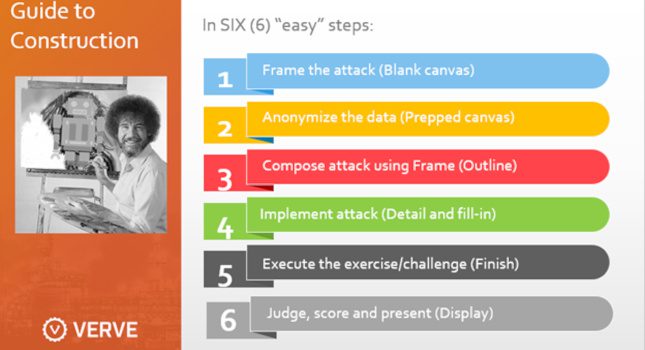
With the recent deluge of ransomware event articles discussing risks, likelihood, payment options and proposed solutions, it’s a good idea to take a step back to see where one stands with regard to preparedness, response […]

Electronics such as sensors in the “cold chain” that health systems use to keep items like COVID-19 vaccines ultra-cold during storage and transport are surprisingly vulnerable to hacking, but there are ways that health systems […]
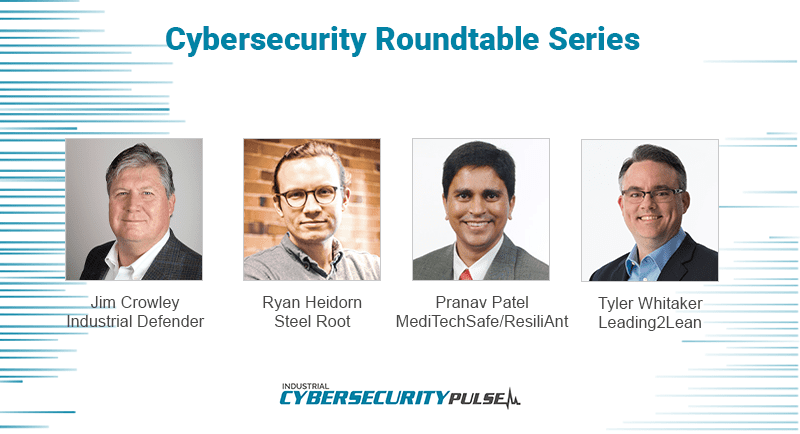
For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our third session, Jim Crowley, CEO at Industrial […]

For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our second session, Bryan Bennett, vice president and […]

For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our first session, Ron Brash, VP of technical […]

It sounds like a scene from a spy thriller. An attacker gets through the IT defenses of a nuclear power plant and feeds it fake, realistic data, tricking its computer systems and personnel into thinking […]

A new coalition that will enhance North Carolina’s economy and keep its citizens safe through education, research and outreach work in cybersecurity will benefit from a $2 million grant from the National Centers of Academic […]

Modern society is inundated with different types of smart devices designed to make people’s lives easier, from virtual assistants to household appliances and health-monitoring devices — not to mention smartphones. While each device has some […]

Oak Ridge National Laboratory (ORNL) researchers have created a technology that more realistically emulates user activities to improve cyber testbeds and ultimately prevent cyberattacks. The Data Driven User Emulation, or D2U, uniquely uses machine learning to […]

Cybersecurity continues to be a major focus of businesses, governments and individuals as the global economy pushes forward into the digital age. High-profile intrusions like Colonial Pipeline, Kaseya and JBS have proven that no one […]
Imagine a team of autonomous drones equipped with advanced sensing equipment, searching for smoke as they fly high above the Sierra Nevada mountains. Once they spot a wildfire, these leader robots relay directions to a swarm […]

To protect against attacks, companies need IT and OT to work together. This webcast presents 5 things OT can learn from IT (and vice versa)

Building on its success in preparing professionals for careers in cybersecurity, Indiana University (IU) has been awarded a grant from the National Science Foundation (NSF) for a new project to train the next generation of […]

In late September, the U.S. Department of Energy (DOE), in partnership with the Manufacturing Innovation Institute (CyManII), announced an investment of more than $1 million in five projects to help make advanced manufacturing processes and […]

The Cyber Security for Critical Assets Summit (CS4CA) will bring together hundreds of information technology (IT) and operational technology (OT) security leaders from across U.S. critical infrastructure for two days of strategy planning, insight building […]

In early August, the industry’s largest hybrid event – Black Hat USA 2021 – took place online and at the Mandalay Bay Convention Center in Las Vegas. The event, which highlighted the latest security trends […]
Energy systems historically have been consistent, safe and reliable, but that doesn’t mean they’re not a target of cyber threat. More and more attackers are now explicitly targeting the kinds of industrial control systems (ICSs) […]

Edge computing is one of the fastest growing areas in the industrial sector as organizations pursue Industry 4.0 opportunities to gain insight from assets at the edge. Over the next few years, IDC projects edge […]

Computing at the edge is one of the fastest growing areas in the industrial sector, but it can also create new cybersecurity risks

Without the right approach to cybersecurity, cyber-physical systems involving the Internet of Things, Big Data and cloud computing are nothing more than an expanded attack surface for hackers

In this session, the presenter will outline the current threat landscape, identify some of the most common vulnerabilities and outline some practical first steps to take to secure industrial control systems, as well as how to take a more holistic view of ICS security

Cyber-physical systems serve as the foundation and the invention base of the modern society making them critical to both government and business

Not so long ago, a strong password felt mighty enough to keep a user safe and computer data private. But now, there are heightened risks in malware, phishing, spearphishing and denial-of-service attacks. Even scarier, it […]

Washington State University has been selected as a recipient of a $1.5 million Department of Defense (DOD) grant to establish a new cybersecurity education and research program. The Northwest Virtual Institute for Cybersecurity Education and […]

New York City is the first city in the U.S. to open its own operational cybersecurity defense center. Located in lower Manhattan, this real-time operational center is the first of its kind. According to the […]

Data presented by the Atlas VPN research team reveals that 31% of businesses in the U.S. are forced to close down as a consequence of falling victim to ransomware attacks. The vast majority of firms […]

With ransomware attacks on critical national infrastructure on the rise, the U.S. government has stepped up its cybersecurity response. So far, this has included a cybersecurity executive order from the White House and the creation […]

Because corporations and governments rely on computers and the internet to run everything from the electric grid, healthcare, and water systems, computer security is extremely important to all of us. It is increasingly being breached: […]
Ryan Heidorn, co-founder and managing partner at Steel Root, walks DoD vendors through what they need to know about the CMMC
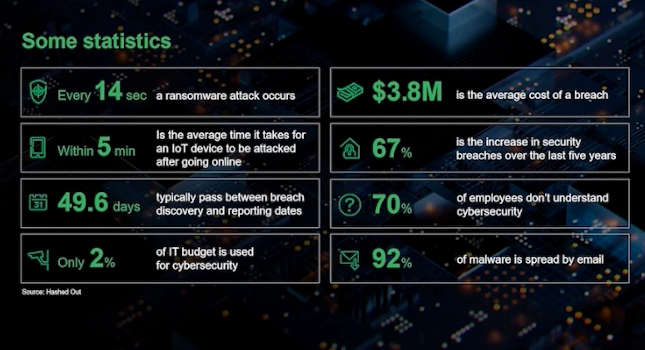
Manufacturing is undergoing some major changes and turning toward a digital transformation. Technology is becoming more intertwined with one another thanks to the Industrial Internet of Things (IIoT) and other concepts are bringing everything together. […]

Cybersecurity has become a major topic after recent high-profile attacks such as SolarWinds and the Oldsmar attack in Florida. Our work world continues to change due to COVID-19 and is forcing cybersecurity to the front […]

They fought the chip and the chip won. MORPHEUS, an “unhackable” computer chip developed by computer science researchers at the University of Michigan, lived up to its name in its first bug bounty competition. It […]

Video courtesy: CxEnergy Presenter: Derek Hedrick, Ameritech Data Solutions Why has Cybercrime become so prevalent? Because it’s easy, it’s hard to get caught, and it’s really profitable, generating more than $1.5 trillion in 2018 alone. Meanwhile, […]

If recent cyberattacks like SolarWinds and Oldsmar have demonstrated anything, it’s the vulnerability landscape in operational technology (OT) and manufacturing is changing rapidly – and not necessarily for the better. Risks are higher than ever […]

Seeq is co-sponsoring the Microsoft Energy Core Methane Emissions Hackathon virtual event. The objective of the hackathon is to overlay oil & gas asset and geographic information system data to pinpoint leak location, and to […]

Between the SolarWinds cyberattack and the smaller, but no less frightening, Oldsmar attack on a water treatment plant near Tampa Bay, Florida., cybersecurity has been front and center in the news. But these two cyberattacks […]

The Hackers’ Epoch: The Cybersecurity Card Game by Scruffy City Games helps students understand online threats and teaches them fundamental terms they’ll need to learn. After playing the game, when they read a news article […]

Featured articles in this eBook include stories on cybersecurity for IIoT robots, cybersecurity asset updates and using cybersecurity to improve tomorrow’s manufacturing operations.

In March 2020, the global working population endured a mass migration from office work to work from home, leading to a huge increase in the number of remote connections through which people interact with their […]

Looking to learn more about industrial cybersecurity? Register for the on-demand cybersecurity webcast

Age of existing assets are the greatest cybersecurity risk factor, 67% in 2020 Control Engineering research, up from 46% in 2016. This is of particular concern with remote operations increasing due to the COVID-19 pandemic and manufacturing starting up again.

Engineering researchers at the National Center for Reliable Electric Power Transmission, based at the University of Arkansas, Fayetteville, are partnering with the Forge Institute and the University of Arkansas at Little Rock to advance applied research […]

Cybersecurity advice about process, technologies, people (internal) and external threat resulted from the Control Engineering 2020 Cybersecurity Research Report. See graphic of technologies and services used online.

Many manufacturers do business with the U.S. Department of Defense (DOD) directly or through original equipment manufacturers (OEMs) and other contractors. The industry is paying attention to the new Cybersecurity Maturity Model Certification (CMMC) because […]
Pulse Points: NeoSystems, an IT systems integrator, has been recognized as an RPO by the Cybersecurity Maturity Model Certification (CMMC) Accreditation Board (AB). The CMMC model itself is created, managed and mandated by the Department […]
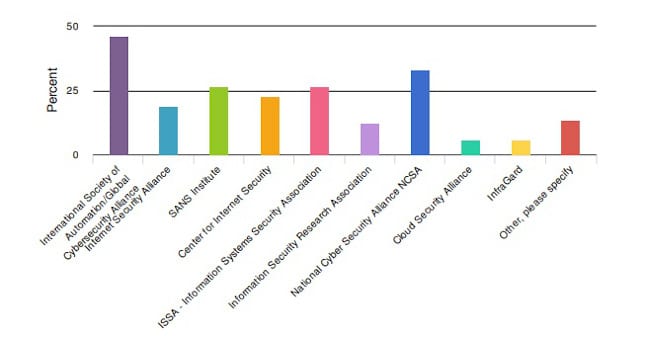
There are many associations dedicated to cybersecurity information out there for engineers. Many of them are dedicated to helping engineers regardless of their specialty, particularly in the last few years. It’s a necessity with the […]

The University of Arkansas received a five-year, $4.63 million award from the National Science Foundation to recruit, educate and train the next generation of cybersecurity professionals.

West Virginia University has received a $1 million award from the National Science Foundation (NSF) to prepare students for cybersecurity jobs with a project called “ACCESS,” which cultivates cybersecurity experts through scholarships and education.
Aydin Aysu, a researcher at North Carolina State University, is offering a course to prepare students to make use of next-generation cybersecurity tools such as cryptography hardware.

A team of researchers at Iowa State University are looking to deploy fleets of drones, but it’s trickier than it sounds due to unexpected weather events and cybersecurity concerns.

Researchers from the University of Bath and Goldsmiths investigate whether a device that plugs in to a PC and signals to a user to change their password could help improve cybersecurity.

A research team from Northern Arizona University is looking to secure blockchain with an architecture that is compatible with cloud-based solutions.
Technology update: Cybersecurity remains a key concern for manufacturing and process facilities as explained in the media session at ARC Forum 2019.

Companies can help prevent cyberattacks by forming a security operations center (SOC) to get the information technology (IT) and operations technology (OT) on the same page with the same goals.

This eBook includes stories on the steps to developing a smart factory and why smart buildings are often insecure.

This eBook, full of our popular Throwback Attacks, includes stories on how a Florida teen infiltrated the DoD and much more.

With escalating cyber threats, companies are prioritizing investments in cybersecurity capabilities, leading to a surge in M&A deals in 2023.

This eBook includes stories on how NotPetya took down shipping giant Maersk and which OT/ICS devices are the riskiest.

The top 5 articles from January 2024 covered everything from SCADA security to IT/OT convergence to operational lifecycle management.

Our top 5 pieces from December 2023 covered bringing SOC/SOAR standards to OT, mobile device management and more.

In this highly interactive webcast, Jeff McDaniel of Airgap will demonstrate how easy it is to close the identity gap for OT.

Already used regularly for IT security, a converged IT/OT SOC can give you greater visibility across your operations and help you defend against outside threats.

This eBook includes stories on how you can detect ransomware faster and how tabletop exercises can help prepare your employees.

When evaluating an organization’s security objectives, you should understand how those objectives align to not overshoot your security target.

Debbie Gordon talks about why security is everyone’s job, how AI won’t replace humans and why “Office Space” is a cybersecurity movie.

In this webcast, learn how a standards-based, defense-in-depth approach can be effective in protecting critical services and infrastructures.

2023 is continuing to demonstrate resiliency in the mergers & acquisitions and capital placement markets for cybersecurity companies.

A Texas A&M professor is looking to move malware detection from software to hardware, creating hardware-integrated protection.

An Idaho National Lab intern developed a cybersecurity research tool, AcCCS, that could improve the security of electric vehicle charging.

Research identified the riskiest OT and ICS devices to key critical infrastructure industries of manufacturing, utilities and transportation.

Spring 2023 is continuing to show strength and consistency in terms of cybersecurity mergers & acquisitions and capital placement.

Clint Bundy, Managing Director with Bundy Group, was recently interviewed by Gary Cohen and Tyler Wall, the hosts of the Industrial Cybersecurity Pulse Podcast. The topic was to discuss the mergers and acquisitions (M&A) and […]

This webcast will examine the rising tide of ransomware and how you can protect OT/ICS, without risking human safety or creating downtime.

This eBook includes stories on how what you need to know about the NERC CIP standards and how to minimize cybersecurity risk in manufacturing.

Purdue researchers are taking aim at the growing surge of supply chain attacks directed at third-party software suppliers and vendors.

ICSP’s top 5 articles from May 2023 covered incident response, nation-state attacks on the energy sector and the cybersecurity skills gap.

The first few months of 2023 witnessed a large number of mergers and acquisitions and capital placement activity in the cybersecurity segment.

The first day of the RSA event featured several keynotes highlighting the potential of AI and private-public partnerships in cybersecurity.

Dragos released its annual Year in Review report about the state of industrial cybersecurity. The ICSP Podcast talked to Ben Miller about it.

The top 5 ICSP articles from March 2023 covered critical infrastructure, the Biden National Cyber Strategy and IT/OT convergence.

SOOS announced the launch of its public SBOM database, where anyone can download an SPDX or CycloneDX SBOM for over 54 million packages.

Sam May of Steel Root talked to the ICS Pulse Podcast about the cybersecurity skills gap and how to combat it.

ICS Pulse’s top 5 articles from February 2023 covered the value of tabletop exercises, why IT/OT convergence requires prioritization and more.

The cybersecurity mergers segment is well positioned for another robust year in terms of M&A and capital placement activity.

The Wall Street Journal held a webinar, “Mitigating Cyber Risk,” to discuss cybersecurity best practices in an evolving industry

ICS Pulse’s top 5 articles from January 2023 covered the Microsoft DCOM hardening patch, insider attacks, the new CDV index and more.

In this webcast, Jay Williams, CEO of Industrial Defender, will discuss how to secure a cybersecurity budget and get buy-in from the C-suite.

This eBook includes stories on why supply chain attacks create a target-rich environment and why supply chain and ransomware are a toxic mix.

In this mergers & acquisitions update, there is significantly more demand than supply of acquisition opportunities in the cyber sector.

This eBook includes stories on how outdated policies put systems at risk and what’s being done to protect the grid from ransomware.

Employer demand for cybersecurity workers continues to strain talent availability according to new data from CyberSeek.

Purdue works to guide the security investments of utility companies to parts of the power grid at risk of causing a blackout if hacked.

As industrial devices become more connected, cyber risk is exploding. We’re proud to announce the new, weekly ICS Pulse Podcast.

This eBook includes stories on the impact of the CMMC and how supply chain attacks are changing the nature of ICS security.

Critical infrastructure provides the essential services that keep American society running. A cyberattack on these systems could create a destabilizing effect on the nation’s physical security, economic security, public health and/or safety. Featured articles in this […]

Smart Chip Insights A smart chip must be able to communicate data between all technology, which often consumes a lot of energy and requires security measures to keep that data safe. Researchers found that using […]

Last fall, LSU announced a new initiative named FIREStarter, which would provide students with training in cybersecurity and threat analysis through the creation of a lab for cyber range exercises. These exercises would be conducted […]

The adoption of Industry 4.0 technologies is increasing efficiency and profitability across industrial control system (ICS) environments, making data available from myriad sources, and employing advanced software tools to analyze information. This gives plant staff […]

In recent months, a spate of high-profile attacks on everyone from private companies to critical infrastructure has put cybersecurity squarely on the radar. But while most seem to understand the need for cybersecurity, many companies […]

Every vendor is telling you to buy their new AI/ML product to secure your systems, ICS or not. Can AI/ML solve your cybersecurity problems

The goal of internal benchmarking is often to gain a better understanding of those entities in your company that are doing well and vice versa. With phishing simulations, you’re able to analyze the results to […]

In this webcast, UL’s cyber experts discuss Industry 4.0 cybersecurity and how you can mitigate security risks and ensure compliance

William Shakespeare might have been talking about Apple’s recently released M1 chip via his prose in “A Midnight Summer’s Dream”: “And though she be but little, she is fierce.” The company’s software runs on the […]

This webcast on June 14 will show you why OT attacks are on the rise and how MITRE ATT&CK can help you defend against them

Cybersecurity attacks against manufacturing have increased in the last several years and will continue to do. While a majority have a financial motive rather than corporate espionage, the result is the same: It costs a […]

While the mergers and acquisitions (M&A) and capital raise markets have a wary eye on numerous potential macroeconomic headwinds — the Ukrainian war, inflation, the great resignation — the cybersecurity market continues to demonstrate its […]

This webcast looks at why supply chain attacks are on the rise and what your organization can do to protect against them

Researchers have developed a technique that leverages hardware and software to improve file system security for next-generation memory technologies called non-volatile memories (NVMs). The new encryption technique also permits faster performance than existing software security […]

As smartphones have grown more sophisticated over the years, so have their accompanying security measures for identity verification. Simple passwords have been replaced by thumbprints and facial recognition. However, those methods do not solve the […]

If a sticker on a banana can make it scan as a toaster, how might strategic vandalism warp how an autonomous vehicle perceives a stop sign? Now, an immune-inspired defense system for neural networks can […]

Daily life is happening increasingly online. There isn’t a big enough cybersecurity workforce in the U.S. to keep everyone safe. That’s the problem that nearly $6 million in new funding will help the University of […]

Cyber incidents have become a major problem for large corporations, small businesses and individuals alike. No one is immune from a potential attack, which means everyone in an organization must play a role in safeguarding […]

It’s critical to understand what industrial control systems (ICS) are, why they are vital and outline the unique challenges of securing ICS. What are industrial control systems? Industrial control systems are used for managing, directing, […]

One of the biggest challenges we consistently hear from security awareness professionals is how to effectively engage, train, and secure a remote workforce. Many of us thought remote working would end in 2021, that life […]

IUPUI will train diverse undergraduate and graduate students to become the next generation of cybersecurity engineers who will help the U.S. respond to national security needs, thanks to a $3.7 million grant from the National […]

The year 2021 was the year cybersecurity went mainstream. High-profile strikes such as the Colonial Pipeline ransomware attack in May 2021 and the SolarWinds supply chain hack resulted in a new U.S. Executive Order and […]

Industrial cybersecurity remains critically important to subscribers of Control Engineering, Plant Engineering, and other CFE Media and Technology publications. Hot topics in 2021 included analysis of prior cybersecurity attacks, malware, rasomware and physical plant damage […]

When cybersecurity initiatives originate with the board of directors, people pay attention. So what are some steps a board can take to keep their charges ahead of the hackers? As industrial cybersecurity and critical infrastructure […]

Cyberattacks have increased since the COVID-19 pandemic. While information technology (IT)/operational technology (OT) convergence remains a hot topic, the conversation about cybersecurity for industrial control systems (ICS) has fallen on deaf ears in some cases. […]

One of my first tasks after leaving the National Security Administration (NSA) for private industry in the early ’90s was to write my new company’s information security policy. I’m not sure my previous job as […]

Regardless of their goal or intent, hackers’ general modus operandi is about disruption and causing chaos for a company, organization or other entity. Sometimes, the hackers try to increase the lye in a water filtration […]

Many experts say companies should spend between 10 and 15% of their annual information technology (IT) budget on cyber defense, but the reality is few companies are spending even that much. While most organizations understand […]

Over the past year, there has been a sharp increase in cyberattacks using malware to target the systems of critical infrastructure such as utility companies, government agencies and organizations that provide services and products we […]

With the recent deluge of ransomware event articles discussing risks, likelihood, payment options and proposed solutions, it’s a good idea to take a step back to see where one stands with regard to preparedness, response […]

Electronics such as sensors in the “cold chain” that health systems use to keep items like COVID-19 vaccines ultra-cold during storage and transport are surprisingly vulnerable to hacking, but there are ways that health systems […]

For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our third session, Jim Crowley, CEO at Industrial […]

For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our second session, Bryan Bennett, vice president and […]

For Cybersecurity Awareness Month, ICS Pulse put together groups of leading industry experts for a series of extensive roundtable conversations about the issues impacting cybersecurity today. In our first session, Ron Brash, VP of technical […]

It sounds like a scene from a spy thriller. An attacker gets through the IT defenses of a nuclear power plant and feeds it fake, realistic data, tricking its computer systems and personnel into thinking […]

A new coalition that will enhance North Carolina’s economy and keep its citizens safe through education, research and outreach work in cybersecurity will benefit from a $2 million grant from the National Centers of Academic […]

Modern society is inundated with different types of smart devices designed to make people’s lives easier, from virtual assistants to household appliances and health-monitoring devices — not to mention smartphones. While each device has some […]

Oak Ridge National Laboratory (ORNL) researchers have created a technology that more realistically emulates user activities to improve cyber testbeds and ultimately prevent cyberattacks. The Data Driven User Emulation, or D2U, uniquely uses machine learning to […]

Cybersecurity continues to be a major focus of businesses, governments and individuals as the global economy pushes forward into the digital age. High-profile intrusions like Colonial Pipeline, Kaseya and JBS have proven that no one […]

Imagine a team of autonomous drones equipped with advanced sensing equipment, searching for smoke as they fly high above the Sierra Nevada mountains. Once they spot a wildfire, these leader robots relay directions to a swarm […]

To protect against attacks, companies need IT and OT to work together. This webcast presents 5 things OT can learn from IT (and vice versa)

Building on its success in preparing professionals for careers in cybersecurity, Indiana University (IU) has been awarded a grant from the National Science Foundation (NSF) for a new project to train the next generation of […]

In late September, the U.S. Department of Energy (DOE), in partnership with the Manufacturing Innovation Institute (CyManII), announced an investment of more than $1 million in five projects to help make advanced manufacturing processes and […]

The Cyber Security for Critical Assets Summit (CS4CA) will bring together hundreds of information technology (IT) and operational technology (OT) security leaders from across U.S. critical infrastructure for two days of strategy planning, insight building […]

In early August, the industry’s largest hybrid event – Black Hat USA 2021 – took place online and at the Mandalay Bay Convention Center in Las Vegas. The event, which highlighted the latest security trends […]

Energy systems historically have been consistent, safe and reliable, but that doesn’t mean they’re not a target of cyber threat. More and more attackers are now explicitly targeting the kinds of industrial control systems (ICSs) […]

Edge computing is one of the fastest growing areas in the industrial sector as organizations pursue Industry 4.0 opportunities to gain insight from assets at the edge. Over the next few years, IDC projects edge […]

Computing at the edge is one of the fastest growing areas in the industrial sector, but it can also create new cybersecurity risks

Without the right approach to cybersecurity, cyber-physical systems involving the Internet of Things, Big Data and cloud computing are nothing more than an expanded attack surface for hackers

In this session, the presenter will outline the current threat landscape, identify some of the most common vulnerabilities and outline some practical first steps to take to secure industrial control systems, as well as how to take a more holistic view of ICS security

Cyber-physical systems serve as the foundation and the invention base of the modern society making them critical to both government and business

Not so long ago, a strong password felt mighty enough to keep a user safe and computer data private. But now, there are heightened risks in malware, phishing, spearphishing and denial-of-service attacks. Even scarier, it […]

Washington State University has been selected as a recipient of a $1.5 million Department of Defense (DOD) grant to establish a new cybersecurity education and research program. The Northwest Virtual Institute for Cybersecurity Education and […]

New York City is the first city in the U.S. to open its own operational cybersecurity defense center. Located in lower Manhattan, this real-time operational center is the first of its kind. According to the […]

Data presented by the Atlas VPN research team reveals that 31% of businesses in the U.S. are forced to close down as a consequence of falling victim to ransomware attacks. The vast majority of firms […]

With ransomware attacks on critical national infrastructure on the rise, the U.S. government has stepped up its cybersecurity response. So far, this has included a cybersecurity executive order from the White House and the creation […]

Because corporations and governments rely on computers and the internet to run everything from the electric grid, healthcare, and water systems, computer security is extremely important to all of us. It is increasingly being breached: […]

Ryan Heidorn, co-founder and managing partner at Steel Root, walks DoD vendors through what they need to know about the CMMC

Manufacturing is undergoing some major changes and turning toward a digital transformation. Technology is becoming more intertwined with one another thanks to the Industrial Internet of Things (IIoT) and other concepts are bringing everything together. […]

Cybersecurity has become a major topic after recent high-profile attacks such as SolarWinds and the Oldsmar attack in Florida. Our work world continues to change due to COVID-19 and is forcing cybersecurity to the front […]

They fought the chip and the chip won. MORPHEUS, an “unhackable” computer chip developed by computer science researchers at the University of Michigan, lived up to its name in its first bug bounty competition. It […]

Video courtesy: CxEnergy Presenter: Derek Hedrick, Ameritech Data Solutions Why has Cybercrime become so prevalent? Because it’s easy, it’s hard to get caught, and it’s really profitable, generating more than $1.5 trillion in 2018 alone. Meanwhile, […]

If recent cyberattacks like SolarWinds and Oldsmar have demonstrated anything, it’s the vulnerability landscape in operational technology (OT) and manufacturing is changing rapidly – and not necessarily for the better. Risks are higher than ever […]

Seeq is co-sponsoring the Microsoft Energy Core Methane Emissions Hackathon virtual event. The objective of the hackathon is to overlay oil & gas asset and geographic information system data to pinpoint leak location, and to […]

Between the SolarWinds cyberattack and the smaller, but no less frightening, Oldsmar attack on a water treatment plant near Tampa Bay, Florida., cybersecurity has been front and center in the news. But these two cyberattacks […]

The Hackers’ Epoch: The Cybersecurity Card Game by Scruffy City Games helps students understand online threats and teaches them fundamental terms they’ll need to learn. After playing the game, when they read a news article […]

Featured articles in this eBook include stories on cybersecurity for IIoT robots, cybersecurity asset updates and using cybersecurity to improve tomorrow’s manufacturing operations.

In March 2020, the global working population endured a mass migration from office work to work from home, leading to a huge increase in the number of remote connections through which people interact with their […]

Looking to learn more about industrial cybersecurity? Register for the on-demand cybersecurity webcast

Age of existing assets are the greatest cybersecurity risk factor, 67% in 2020 Control Engineering research, up from 46% in 2016. This is of particular concern with remote operations increasing due to the COVID-19 pandemic and manufacturing starting up again.

Engineering researchers at the National Center for Reliable Electric Power Transmission, based at the University of Arkansas, Fayetteville, are partnering with the Forge Institute and the University of Arkansas at Little Rock to advance applied research […]

Cybersecurity advice about process, technologies, people (internal) and external threat resulted from the Control Engineering 2020 Cybersecurity Research Report. See graphic of technologies and services used online.

Many manufacturers do business with the U.S. Department of Defense (DOD) directly or through original equipment manufacturers (OEMs) and other contractors. The industry is paying attention to the new Cybersecurity Maturity Model Certification (CMMC) because […]

Pulse Points: NeoSystems, an IT systems integrator, has been recognized as an RPO by the Cybersecurity Maturity Model Certification (CMMC) Accreditation Board (AB). The CMMC model itself is created, managed and mandated by the Department […]

There are many associations dedicated to cybersecurity information out there for engineers. Many of them are dedicated to helping engineers regardless of their specialty, particularly in the last few years. It’s a necessity with the […]

The University of Arkansas received a five-year, $4.63 million award from the National Science Foundation to recruit, educate and train the next generation of cybersecurity professionals.

West Virginia University has received a $1 million award from the National Science Foundation (NSF) to prepare students for cybersecurity jobs with a project called “ACCESS,” which cultivates cybersecurity experts through scholarships and education.

Aydin Aysu, a researcher at North Carolina State University, is offering a course to prepare students to make use of next-generation cybersecurity tools such as cryptography hardware.

A team of researchers at Iowa State University are looking to deploy fleets of drones, but it’s trickier than it sounds due to unexpected weather events and cybersecurity concerns.

Researchers from the University of Bath and Goldsmiths investigate whether a device that plugs in to a PC and signals to a user to change their password could help improve cybersecurity.

A research team from Northern Arizona University is looking to secure blockchain with an architecture that is compatible with cloud-based solutions.

Technology update: Cybersecurity remains a key concern for manufacturing and process facilities as explained in the media session at ARC Forum 2019.

Companies can help prevent cyberattacks by forming a security operations center (SOC) to get the information technology (IT) and operations technology (OT) on the same page with the same goals.
Keep your finger on the pulse of top industry news

This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Strictly Necessary Cookie should be enabled at all times so that we can save your preferences for cookie settings.
If you disable this cookie, we will not be able to save your preferences. This means that every time you visit this website you will need to enable or disable cookies again.